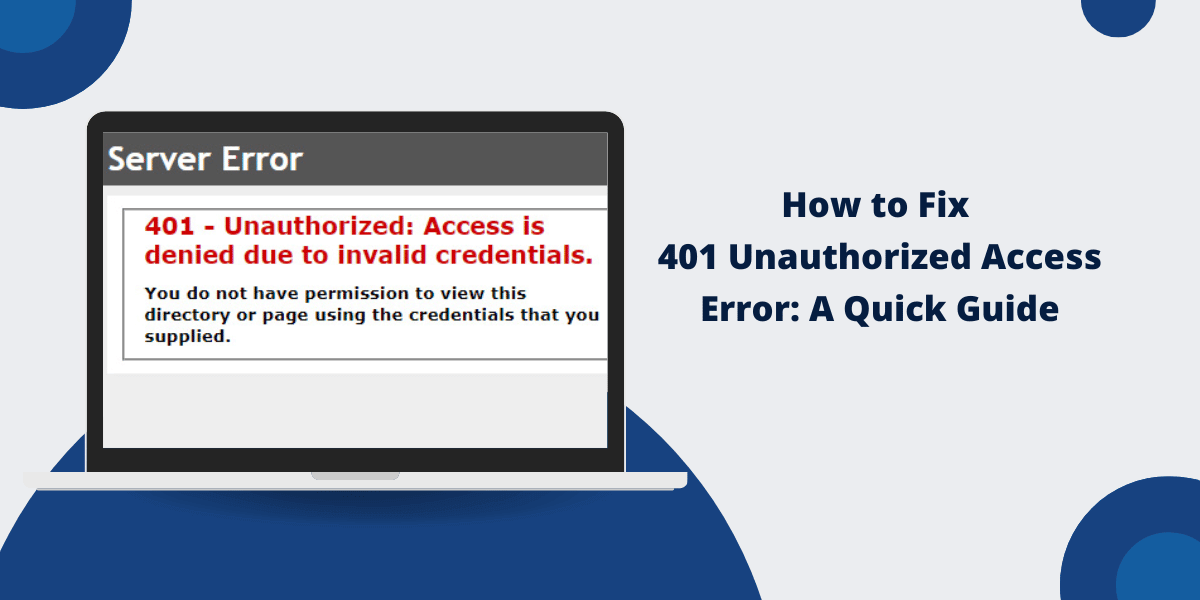
What is the 401 HTTP Status Code?
The 401 Unauthorized is an HTTP status code that indicates the request to the web server requires user authentication. The full name is “401 Unauthorized” or “HTTP 401,” as defined in the HTTP specification RFC 7235. The 401 code is in the class of 400 codes that signify a client-side error, meaning the requesting client did not provide a valid request. To Fix the 401 Unauthorized Access Error, it’s crucial to understand the root causes and implement the appropriate solutions.
Specifically, 401 means that the client tried accessing a protected resource that requires Authentication, but valid credentials were not sent to the request. This could be missing, invalid, or expired login details like username/password or access token.
As a result, the server rejects the request and returns the 401 error in the response. This prompts the client to retry the request with proper authentication credentials.
Key Takeaways
- The 401 Unauthorized error occurs when a user tries to access a protected resource without providing valid authentication credentials.
- It’s an HTTP status code whose full name is “401 Unauthorized” or “HTTP 401.
- The error indicates that the request requires user authentication. The requested resource cannot be accessed anonymously.
- Common causes include missing or invalid credentials, such as username/password, expired login sessions, inadequate access rights, and disabled user accounts.
- The 401 error is different from the 403 Forbidden error, which means the user is authenticated but not authorized to access the page.
- To resolve a 401 error, users need to log in with the correct credentials or fix invalid/expired tokens. Developers must check authentication logic.
- Browsers will typically display a standard 401 error page. APIs return a 401 status code in the response.
- Proper error handling, like redirecting users to a login page, is important for a good user experience.
When Does the 401 Error Occur?
The 401 Unauthorized error occurs in any of these situations:
- No authentication: The user tries to access a protected resource or page that requires logging in, but no credentials were sent in the request.
- Invalid credentials: The request includes Authentication, such as a username/password or token, but the details are incorrect or don’t match those of a valid user.
- Expired credentials: The login session or access token has expired, so valid credentials were provided initially but are no longer valid.
- Insufficient access rights: The user is logged in and authenticated, but does not have adequate permissions to access the particular resource.
- Disabled user account: The user’s account is disabled or deactivated, so the login credentials are correct but rejected.
The 401 error ultimately means the server is unable to identify and authenticate the user making the request.
Without knowing the user’s identity and access rights, the server cannot authorize the request and has to block access to maintain security.
How 401 Errors Differ from 403 Forbidden
The 401 Unauthorized status code is often confused with the 403 Forbidden error, but they have distinct meanings:
- 401 Unauthorized means the user is not authenticated. They have not logged in or provided valid credentials.
- 403 Forbidden means the user is authenticated (logged in) but not authorized to access the specific resource or perform the requested operation.
In other words:
- 401 = Authentication failure. The user is unnamed/anonymous as far as the server is concerned.
- 403 = Authorization failure. The user’s identity is known, but they don’t have permission.
For example, anyone can log in to a website with valid credentials and become an authenticated user. However, they may still get a 403 error if they try accessing admin pages that only site moderators are authorized to view.
What are the Common Causes of 401 Unauthorized Access Error
Here are some of the most common reasons why a 401 Unauthorized error occurs:
Missing Credentials
The user tries accessing a login-protected page when not logged in. No authentication details like username/password are sent in the request.
For example, going directly to https://www.google.com/mail instead of logging in at https://accounts.google.com first.
Entering the Wrong Login Details
The user provides a username and password, but the details don’t match a valid user account, resulting in invalid credentials.
Typos in usernames, entering an old forgotten password, or signing in with the wrong email are common issues here.
Expired Login Session
The user was previously logged in, but the login session expired after being idle for some time.
Most web apps have a session timeout that logs users out automatically after, say, 30 minutes of inactivity.
Invalid or Expired Access Token
In server-side apps and APIs, client requests are authenticated using access tokens rather than direct logins.
The token could be invalid if signed incorrectly on the server. It could also expire if the lifetime is limited, say to 24 hours.
Insufficient User Access Rights
The user has a valid account and is logged in, but does not have the right access permissions for the particular resource.
For example, a standard website member is trying to access admin-only pages.
Disabled User Account
The user account has been deactivated or blocked by the admin. So, the credentials match an existing account, but Authentication fails when it is disabled.
Accounts may be disabled due to inactivity, violations, or unverified email addresses.
Application Authentication Logic Errors
Bugs in application code that handles login validation, credential checking, account statuses, etc. can incorrectly result in 401 errors.
For example, if valid credentials erroneously fail your account validation checks.
CORS Authentication Issues
Cross-Origin Resource Sharing (CORS) misconfigurations can block cross-origin AJAX requests, incorrectly returning 401 errors.
This happens when the API server has tight CORS policies that reject requests from other domains.
How to Fix the 401 Unauthorized Access Error
To resolve 401 unauthorized issues, the general solution is to provide valid authentication credentials:
- Log in: To identify themselves, users should first log in or sign up for missing credentials.
- Enter correct credentials: Fix typos in usernames or passwords. Retrieve forgotten passwords.
- Re-authenticate: If the old login session has expired, Refresh the page or make a new request to re-initialize a new one.
- Request new access token: Obtain a fresh token if the current one is invalid or expired.
- Gain access permissions: Request authorization for additional access from site admins.
- Use active account: Switch to an account that is enabled if the current one was disabled.
- Update server policies: Loosen CORS policies on API servers to allow cross-origin AJAX requests.
- Fix authentication bugs: For application logic errors causing invalid 401s, check code handling credentials, tokens, access rights, etc.
401 Error Handling Best Practices
When dealing with 401 errors, following some best practices will improve security, user experience, and overall application robustness:
Browser Behavior
- The browser automatically displays a stock 401 page or alert indicating the request was unauthorized.
- It includes a WWW-Authenticate header prompting for credentials.
- The browser cancels the original request and does not display any content.
- It does not cache or store the 401 error page due to its sensitive nature.
- Browsers may preemptively send Authorization headers in requests to sites that previously returned 401s, avoiding second errors.
Server Response
- The server returns a 401 status line in the HTTP response, with no response body.
- It must send a WWW-Authenticate header indicating that the authentication scheme is required.
- The Location header can be used to redirect unauthorized requests to a login page.
- 401 responses have no caching directives, so pages are never cached when Authentication fails.
- The response body can provide additional context for developers. But browsers will not render it.
APIs and 401 Errors
In APIs accessed by other applications, not browsers, a 401 error is returned as:
- The numeric 401 status code in the response.
- A JSON response body with a relevant error reason to help developers debug.
- An authentic header specifying the auth scheme expected by the API is needed.
401 Error Examples
Here are some examples of common 401 error scenarios and how they get triggered:
Accessing Gmail without Login
Navigating directly to Gmail at https://www.google.com/gmail/ results in a 401.
Gmail is a protected resource that requires logging into Google’s servers first. The request has no credentials, so the server returns a 401 Unauthorized error.
Wrong Username or Password
When you try to log in to a site with an incorrect username or password, you get a 401.
The server checks the credentials against its user database and finds no matching account, so you are not authorized.
Expired Login Session
You log in to a website and browse around for a while. After 30 minutes of inactivity, you try to load a new page but get a 401 error.
The login session has expired after the timeout period, so you have to re-authenticate.
Invalid API Token
An API client makes requests with an expired access token and receives 401 Unauthorized errors.
The API server checks the token’s signature and expiry and finds it invalid, so the client is not authenticated.
Accessing Admin Pages
A regular user tries to access admin-only pages but lacks sufficient privileges. Even though logged in, they get 401s.
The server checks the user’s role and determines they are not authorized for admin resources.
Troubleshooting 401 Errors
Debugging 401 authentication issues generally involves:
- Repeating request with valid new credentials: Try logging in again with the proper username/password and retry accessing the protected resource.
- Checking credentials are reaching the server: Use the browser’s Network tab or an API client to inspect request headers and see if an Authorization value is sent.
- Testing all authentication paths: Try different sign-in options to isolate the problem e.g. via social auth, email login, OAuth, etc.
- Logging authentication failures: Enable failure logs on the server and check for patterns involving specific users, endpoints, tokens, etc.
- Inspecting server access rights config: Check RBAC settings that determine which user roles and privileges can access resources.
- Running API request locally: Test directly on the server instead of the remote client to detect if the issue lies with client code or CORS.
- Enabling CORS on APIs: Try adding CORS headers like Access-Control-Allow-Origin if requests are cross-origin.
- Clearing cookies and cache: Remove cookies and cached data in your browser that could be storing expired or invalid credentials.
- Checking user account status: Confirm the account is active and not disabled/locked out due to access violations.
Final Thoughts
401 Unauthorized errors indicate that the user has not authenticated properly when trying to access a protected resource.
This could be caused by a number of issues, such as missing credentials, incorrect logins, expired sessions or tokens, insufficient user privileges, account deactivation, or backend application bugs.
Supplying valid authentication details for the user is key to resolving them. 401 handling should be as user-friendly as possible.
On the server side, follow best practices for properly validating credentials, setting resource permissions, enabling CORS, etc. Proper logging and monitoring of 401 occurrences also help identify and fix the sources of these errors.
While 401 errors are annoying, the authentication and authorization checks provoking them are important protections that keep your web apps secure. Dealing with them tactfully and debugging them thoroughly leads to better user experiences overall.
Frequently Asked Questions (FAQ)
Why am I getting a 401 Unauthorized error?
The most common reasons are that you are trying to access a login-protected page when not logged in, entering incorrect login credentials, your login session expires, or your access token becomes invalid.
How is 401 different from 403 Forbidden?
401 means authentication failed, while 403 means authorization failed after successful Authentication. 401 is for unknown/unidentified users, and 403 is for known but unauthorized users.
How can I fix a 401 error?
Typically, log in with the proper credentials or get new tokens. Check that your user account is active. Make sure to send authorization headers in your requests.
Why do I keep getting 401 even after logging in?
Some possibilities are the login session expired quickly, the access token was invalid or short-lived, or a CORS issue is blocking authenticated requests.
Does 401 mean my account is hacked?
Not necessarily. 401 just means incorrect/missing credentials were provided. It could occur if you simply mistyped your password. Monitor account activity for suspicious signs.
Where does the 401 status code come from?
401 Unauthorized is defined in the HTTP RFC 7235 standard specification published by the Internet Engineering Task Force (IETF).
Is 401 an error or exception?
The 401 status code signifies an HTTP error occurred, but it is not a software exception. Rejecting unauthorized requests is normal response behavior.
Can I customize the 401 error page?
Yes, web servers can be configured to display custom 401 pages. However, browsers will not cache these pages for security reasons.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.