Difference between Secure Socket Layer (SSL) and Transport Layer Security (TLS)
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are two encryption protocols that provide security and data integrity between two communicating computer applications or servers.
The main differences between SSL vs TLS are:
- TLS is an updated, more secure version of SSL. SSL 3.0 and older versions have vulnerabilities.
- TLS 1.0, 1.1, 1.2 and 1.3 are the most common TLS protocol versions used today for secure web browsing. Most websites use TLS instead of SSL now.
- All modern browsers support TLS, while older browsers may not. Websites typically accept both TLS and SSL connections for broader compatibility.
- TLS uses more advanced encryption algorithms and key exchanges than SSL for better security. Recent TLS versions like TLS 1.3 provide forward secrecy as well.
TLS is a newer, more secure version of SSL. Most websites use TLS for encrypting sensitive web traffic instead of the older SSL standard to provide better protection and mitigate vulnerabilities. Check that your website uses an up-to-date TLS version for optimal security.
SSL vs TLS Key Takeaways
- SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols that provide secure communications over the internet.
- TLS is an evolution of SSL and was designed to be an open standard and address vulnerabilities in SSL.
- SSL usage today is only recommended for legacy systems that cannot be upgraded to use TLS.
- TLS supports newer encryption algorithms and key lengths considered more secure than SSL.
- Several vulnerabilities like POODLE and BEAST have been found in SSL but not TLS.
- TLS has extensions for functionality like SNI, ECC, and session tickets that make it more adaptable.
- For new implementations, TLS 1.2 or the latest TLS 1.3 are recommended for security best practices.
- When migrating from SSL to TLS, obtain new certificates, enable forward secrecy ciphers, enforce TLS settings, and test extensively.
- TLS provides identity verification, data encryption, and integrity checking to secure communications from tampering and eavesdropping.
Head to Head Comparison Between SSL vs TLS
| Feature | SSL | TLS |
|---|---|---|
| Initial Release | 1994 | 1999 |
| Based On | – | SSL 3.0 |
| Last Version | SSL 3.0 (1996) | TLS 1.3 (2018) |
| Encryption Protocol Support | Older (SHA-1, MD5) | Newer (AES, ECC) |
| Authentication | Server Authentication | Server and Client Authentication |
| Vulnerabilities Fixed | – | Fixes weaknesses in SSL |
| Forward Secrecy Support | Limited Support | Better Support |
| Browser & Devices Compatibility | Limited, older browsers don’t support higher SSL versions | Better – most modern browsers and devices support latest TLS versions |
| Certificate Types Used | SSL Certificates | SSL/TLS Certificates |
| Compliancy | PCI DSS Compliant | PCI DSS does not allow SSL after June 30, 2018 |
Getting Started with SSL and TLS Communication Protocols
SSL and TLS enable secure, private communication between two parties — a client and a server. This prevents third parties from reading or modifying information as it travels across the internet.
Some common applications of SSL and TLS include:
- Secure web browsing – HTTPS websites use TLS to encrypt traffic and validate the server’s identity. The padlock icon indicates a secure TLS connection.
- Email encryption – Technologies like SMTPS encrypt emails using TLS while they are in transit between mail servers.
- Virtual private network (VPN) connections – TLS secures the communication between your device and the VPN server.
- Encrypted messaging apps – Apps like WhatsApp and Signal use TLS to secure chat messages and voice/video calls.
SSL and TLS operate between the transport layer and application layer of the OSI model:
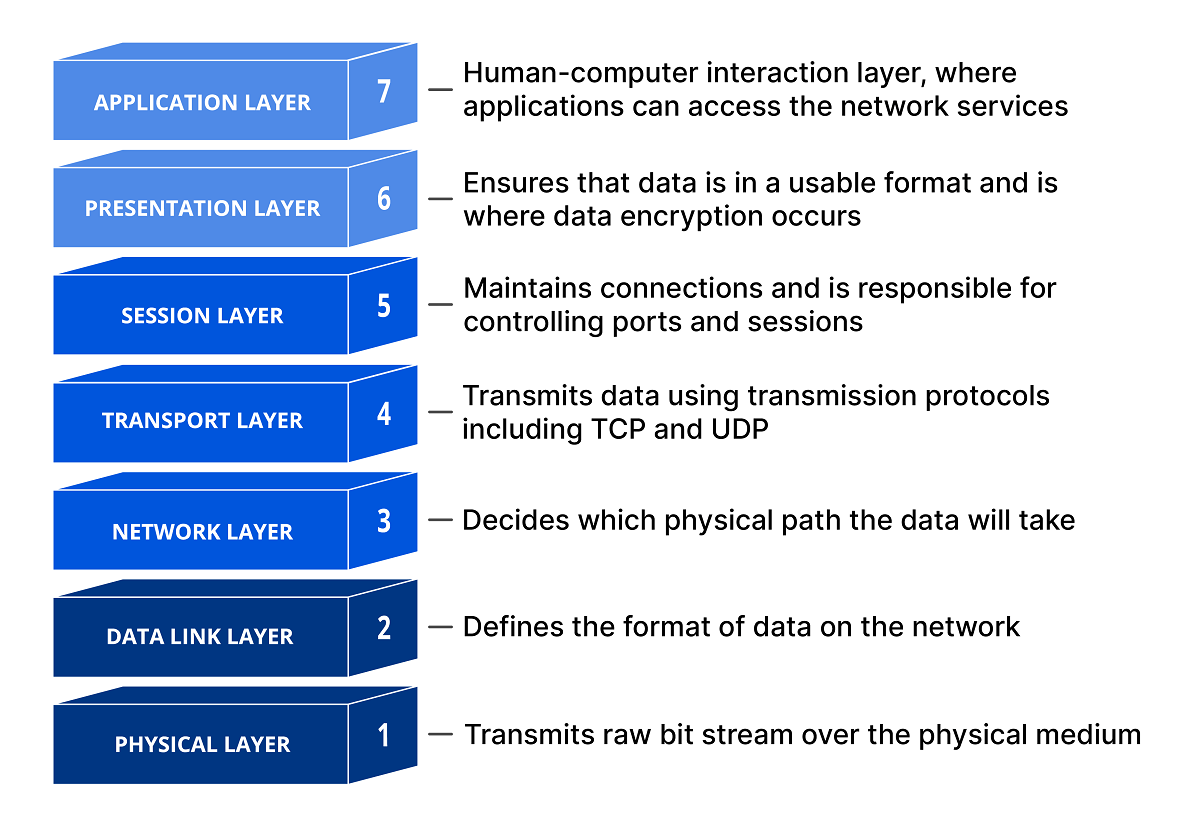
Image credit: cloudflare.com
This allows applications to establish secure connections regardless of the transport protocol being used. For example, TLS can secure TCP- and UDP-based communication.
Now let’s look at how SSL and TLS work.
How SSL and TLS Work
SSL and TLS use asymmetric (public-key) cryptography to provide identity verification, encryption, and integrity of data:
Identity Verification
- A trusted Certificate Authority (CA) issues a public key certificate for the server. This certificate binds the server’s identity to its public key.
- The client validates the server’s certificate and public key before establishing a connection. This verifies the server’s identity.
Encryption
- The server and client negotiate a symmetric encryption key to encrypt data in both directions.
- All data transmitted is encrypted using algorithms like AES or RC4 to prevent eavesdropping.
Data Integrity
- Message authentication codes (MACs) are used to detect any manipulation or corruption of data while in transit.
- It protects against man-in-the-middle attacks where an adversary attempts to intercept and alter communications.
Let’s go through the SSL/TLS handshake process step-by-step:
- Client hello– Client sends supported TLS version, ciphersuites, and other parameters. It also generates a random value.
- Server hello– Server selects TLS version and ciphersuite to use. It also generates a random value.
- Server certificate– Server sends its public key certificate to prove its identity.
- Client verifies certificate– Client validates the server’s certificate is signed by a trusted CA. This verifies the server’s identity.
- Client key exchange– Client generates a pre-master secret and encrypts it with the server’s public key. This is used later to generate a shared symmetric key.
- Change cipher spec– Client informs server subsequent communications will use the new encrypted session.
- Client finished– Client sends an encrypted handshake message to confirm parameters.
- Server change cipher spec– Server switches its side of the connection to the new encryption.
- Server finished– Server sends its own encrypted handshake message.
Main Differences Between SSL and TLS
SSL and TLS have some important differences:
- Age – SSL is older (1991 vs. 1999) and the first version (SSL 1.0) is now deprecated due to security flaws. TLS is based on SSL 3.0.
- Encryption – TLS supports newer cipher suites and cryptographic algorithms considered more secure than SSL.
- Vulnerabilities – SSL has suffered protocol level vulnerabilities like BEAST and POODLE that do not impact TLS.
- Interoperability – TLS is an IETF standard while SSL was proprietary to Netscape. TLS is more widely supported across platforms.
- Extensions – TLS supports extensions for enhanced functionality like identity verification, key shares, and encryption algorithms.
Let’s explore each of these differences in more detail.
Age and Generations
- SSL 1.0 – Released in 1991 by Netscape and quickly found to have multiple security flaws. It is now deprecated and should not be used.
- SSL 2.0 – Released in 1995 with fixes to SSL 1.0 flaws. Also deprecated due to remaining vulnerabilities.
- SSL 3.0 – Released in 1996 and was a complete redesign. Still vulnerable to attacks like POODLE that impacted legacy browsers.
- TLS 1.0 – Released in 1999 based on SSL 3.0 and designed to be an IETF standard.
- TLS 1.1 – Released in 2006 with security improvements and support for more encryption algorithms.
- TLS 1.2 – Released in 2008 and is the current recommended version for secure implementations. Fixes flaws in TLS 1.0.
- TLS 1.3 – Released in 2018 with improved encryption, performance, and security. It is slowly being adopted by web browsers and servers.
Encryption Improvements
TLS supports stronger symmetric encryption algorithms and key lengths than those available under SSL:
- AES 128/256-bit – Advanced Encryption Standard using 128 or 256-bit keys. Considered very secure.
- Camellia 128/256-bit – A Japanese encryption standard on par with AES.
- ChaCha20-Poly1305 – A high-speed cipher resistant to timing attacks. Used in TLS 1.3.
TLS has also deprecated older insecure algorithms like RC4 and export-grade encryption that were available under SSL.
Vulnerabilities in SSL
Over the years, several vulnerabilities have been discovered specifically related to SSL that do not impact TLS:
- POODLE (2014) – Exploits SSLv3 padding with predictable IVs. Does not work on TLS connections.
- BEAST (2011) – Leverages weaknesses in TLS 1.0 cipher block chaining. Mitigated in TLS 1.1.
- FREAK (2015) – Forces RSA key downgrades to export-grade 512-bit encryption.
There are also many vulnerabilities like Heartbleed, BERserk, etc that can affect implementations of both SSL and TLS. Proper configuration is always important for security.
Interoperability and Extensibility
As an IETF standard, TLS implementations must follow common profiles and extensions for guaranteed interoperability. SSL was proprietary to Netscape so different versions were not always compatible.
TLS supports extensions for:
- Server Name Indication (SNI) – Allows hosting multiple domains on one IP address.
- Elliptic Curve Cryptography (ECC) – More efficient public-key encryption than RSA.
- Session Tickets – Resume TLS sessions without full handshakes.
- Next Protocol Negotiation (NPN) – Negotiate application layer protocols like HTTP/2 over TLS.
These extensions make TLS more adaptable and secure in modern environments.
Should You Use SSL or TLS?
For new implementations, TLS is recommended since it is more secure and widely supported across all browsers and platforms.
TLS 1.2 or TLS 1.3 should be used for the best security and performance.
SSL usage is only recommended in legacy systems that require support for older clients and cannot be upgraded to use TLS.
Migrating from SSL to TLS
When migrating from SSL to TLS, here are some best practices:
- Evaluate client and application support for TLS versions. aim for 1.2 or 1.3.
- Obtain new TLS certificates signed with SHA-2 from trusted CAs. May require new CSRs.
- Enable forward secrecy cipher suites like ECDHE for better security.
- Enforce secure TLS settings like protocol version, cipher suites, and extensions.
- Change application configurations, API endpoints, and code to use TLS instead of SSL.
- Redirect HTTP to HTTPS in the application frontend and enable HSTS.
- Consider hardware acceleration if TLS encryption impacts performance.
- Test extensively!
Conclusions on SSL vs TLS
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both cryptographic protocols that provide secure communications over a computer network. TLS is actually the newer, upgraded version of SSL. The main differences between the two protocols are that TLS supports newer cryptographic algorithms, fixes vulnerabilities present in SSL, and has improved encryption methods.
People consider TLS more secure and robust than SSL. While people still use SSL, major industry players like Google, Mozilla, and Microsoft recommend that you switch to TLS if possible for better security. You should use TLS for any new application or service requiring encryption. Most modern web browsers defaultly support TLS. As computing power increases, SSL’s vulnerabilities will become more exposed over time compared to TLS. For the most up-to-date secure data protection, experts recommend TLS 1.2 or higher rather than the use of outdated SSL technology.
FAQs About SSL vs TLS Protocols
Still have questions? Here are answers to some frequently asked questions about the differences between SSL vs TLS:
Is TLS the same as SSL?
TLS is not the same as SSL, but it is the successor. TLS 1.0 was based on SSL 3.0 but with security improvements. Newer versions of TLS have evolved independently of SSL.
Is TLS more secure than SSL?
Yes, people consider TLS more secure than SSL. TLS supports newer cryptographic algorithms and extensions that SSL does not have available. Developers also designed TLS to fix vulnerabilities present in SSL.
Do I need SSL if I have TLS?
No, TLS is a complete replacement for SSL. You only need to support TLS assuming clients connecting to your server have TLS capabilities.
What is the difference between TLS 1.0, 1.1 and 1.2?
TLS 1.0 is based on SSL 3.0, TLS 1.1 added improvements like CBC protection, and TLS 1.2 added support for more ciphers and hash algorithms. Always use the latest version of your clients and server’s support.
Is TLS free?
Yes, TLS itself is an open standard that can be implemented for free. However, public key certificates from trusted CAs required to use TLS do involve fees. The protocol can use self-signed certificates for zero cost.
What ports do SSL vs TLS use?
Both SSL and TLS typically use port 443 for HTTPS traffic. SSL’s original port for HTTP traffic was 80, while TLS uses standard HTTP/HTTPS ports of 80 and 443.
What is more secure – TLS 1.2 or TLS 1.3?
TLS 1.3 is more secure. It supports improved encryption like ChaCha20/Poly1305 by default, faster handshake times, and better security against replay attacks and key compromises.
Can you use TLS without a certificate?
Technically yes, you can use TLS with self-signed certificates that don’t validate identity. However, for security best practice TLS should be used with certificates signed by trusted CAs for authentication.