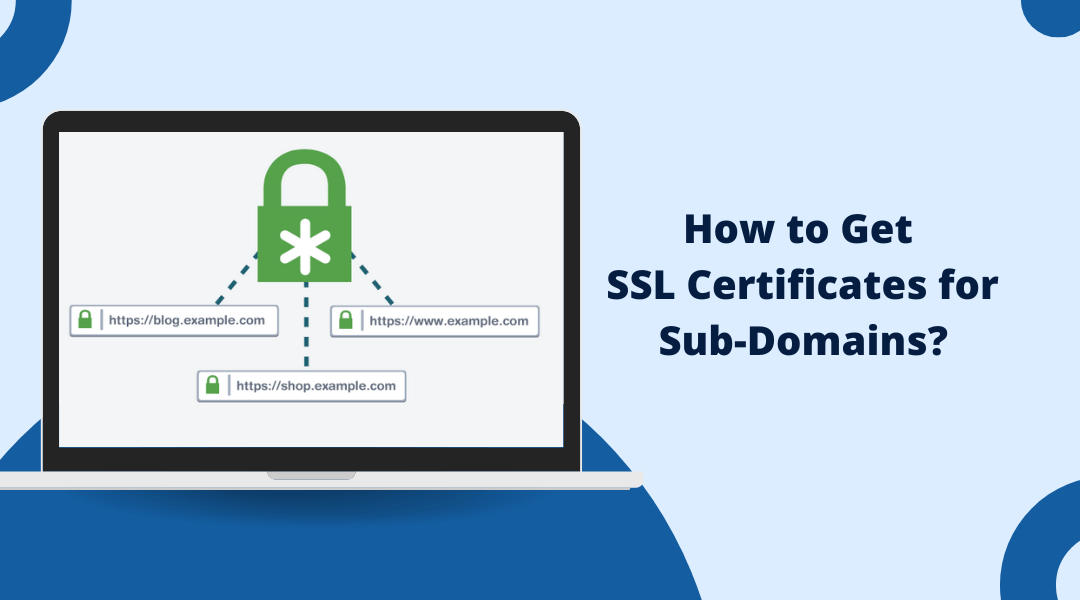
Guide to Resolve SignTool Error: "No Certificates Were Found That Met All the Given Criteria" The SignTool error "No certificates were found that met all the given criteria" can be frustrating to encounter when trying to sign an app, driver, or other executable file....