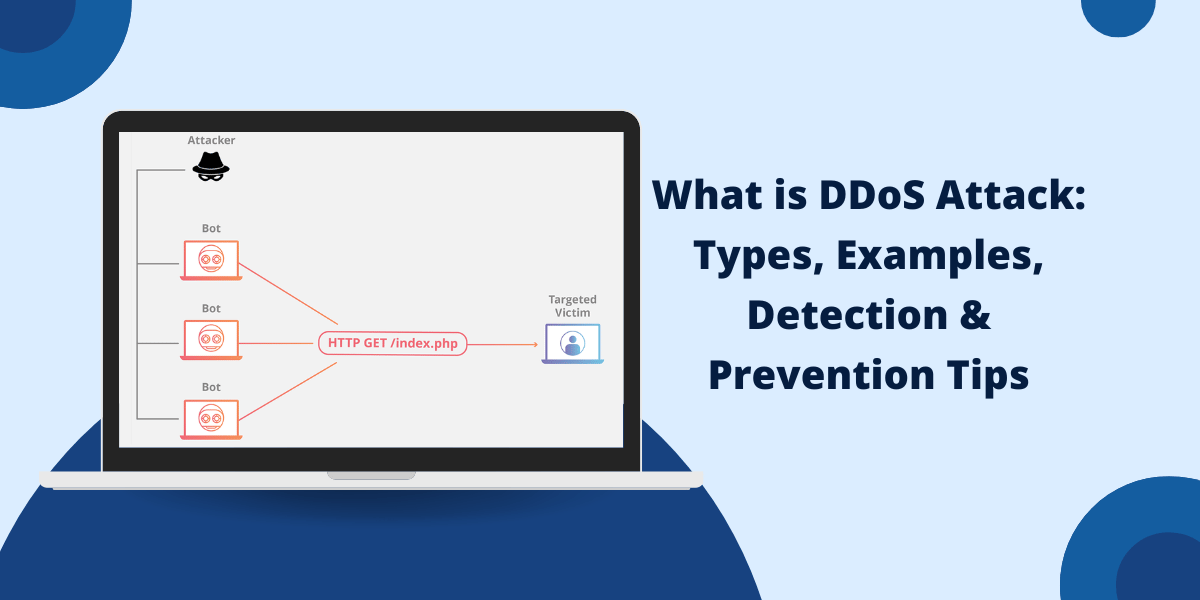
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a website or online service by overwhelming it with a flood of internet traffic. The goal is to overload the target’s servers and bandwidth capacity so that legitimate users are unable to access the service.
In a DDoS attack, the incoming traffic flooding the victim originates from many different sources. This makes it a “distributed” attack as opposed to a DoS (Denial of Service) attack, which uses one source. The attack traffic originates from a network of compromised computers, known as a botnet, which the attacker controls.
Botnets can consist of thousands or even millions of devices controlled remotely by a hacker. When the botnet is instructed to simultaneously send requests to the target website, the combined traffic can easily overwhelm the victim’s servers and bandwidth.
DDoS attacks have grown increasingly common and dangerous, disrupting business operations and costing organizations millions in damages. They have also become more complex, using a variety of tactics to circumvent protections. Defending against DDoS requires constant vigilance, planning, and adaptation.
Key Takeaways
- A DDoS attack aims to overwhelm a website or online service with traffic to make it unusable.
- Attackers use botnets of compromised devices to generate massive amounts of traffic.
- Common DDoS attack types include volumetric, protocol, and application layer attacks.
- DDoS attacks can be very difficult to defend against due to their distributed nature.
- Prevention involves maintaining infrastructure resilience, blocklisting IPs, filtering traffic, and using DDoS mitigation services.
Major DDoS Attack Types
There are three primary categories of DDoS attacks, each using different tactics to overwhelm the target:
Volumetric Attacks
Volumetric attacks aim to consume the bandwidth of the target with massive amounts of useless traffic. Common volumetric attack types include:
- UDP floods: where the attacker sends a high volume of UDP (User Datagram Protocol) packets to random ports on the victim server. The target system will become overwhelmed attempting to respond.
- ICMP floods: involving a massive amount of ICMP (Internet Control Message Protocol) echo requests (“ping”) being sent to the target.
- Amplification attacks: which use publicly accessible services to reflect and amplify a small attack into a larger one. For example, using DNS servers to flood a target with DNS response traffic.
Protocol Attacks
Protocol attacks target the network layer by consuming actual server resources or state tables. Some examples are:
- SYN floods occur when the attacker sends continuous TCP SYN requests to a server but does not complete the handshake, overwhelming resources.
- ACK floods occur when a large number of TCP ACK packets overwhelm the target and cannot be ignored.
- Fragmented packet attacks: sending a flood of illegally formatted packets that the target struggles to re-assemble.
Application Layer Attacks
Application layer attacks directly target web applications and servers by consuming excessive application resources. Tactics used include:
- HTTP flooding: barraging sites with valid HTTP GET or POST requests to overwhelm application resources.
- Low and slow attacks: submitting normal application requests at a very slow rate to gradually accumulate resource exhaustion.
- HashCollision attacks: sending specially crafted requests aimed at overwhelming a server’s hash tables, used for load balancing and compression.
How to Detect a DDoS Attack
Detecting an active DDoS attack or impending one requires looking for various indicators:
- Bandwidth Saturation: Unusually high network traffic, depleted bandwidth, interface queues rapidly filling.
- Unreachable Services: Users unable to access websites or servers offline with no apparent cause.
- Slow Performance: The website and applications are responding much slower than expected.
- Increased Error Responses: High rate of timeouts, connection resets, and failure responses.
- Anomalous Traffic Patterns: Protocols like UDP ICMP dominating instead of standard TCP port 80 or port 443. Traffic from unusual origins.
- 100% CPU Usage: Application and database servers maxing out CPUs from invalid requests.
- Above Baseline Traffic: Overall traffic volume significantly exceeds historical baselines for the time of day or day of the week.
DDoS attacks can be spotted by noticing one or two of the above indicators. However, advanced hackers use gradual ramp-up periods, short intermittent attacks, and polymorphic malware to achieve stealth. Relying solely on human monitoring will inevitably cause some attacks. Automated solutions are required for reliable detection.
How to Prevent DDoS Attacks
A concerted strategy combining technological defenses, expertise, and planning is required for optimal prevention against DDoS threats:
- Maintain internet bandwidth overprovisioning to absorb attack spikes up to a certain size.
- Deploy application layer DDoS protections like web application firewalls (WAFs), rate limiting, and load balancers.
- Enable blocklisting on perimeter firewalls and routers to block known attack IP ranges.
- Configure intrusion prevention systems and DDoS detection solutions to identify anomalies.
- Filter obviously malicious traffic like spoofed packets and proprietary protocol use.
- Enable server and application health monitoring with alerting to catch issues early.
- Implement CAPTCHAs and visitor controls to challenge abusive traffic from unverified clients.
- Maintain relationships with DDoS mitigation service providers to divert large attacks on demand.
- Follow cyber security best practices, especially for remote administration, backups, and patching.
- Develop emergency response plans and procedures in case an attack occurs.
DDoS resilience requires a layered approach for maximum protection and uptime. Lean on in-house and third-party expertise to create a robust anti-DDoS posture.
DDoS Protection Services
Specialist DDoS protection providers offer cloud scrubbing solutions to mitigate even large volume attacks:
- Cloudflare: Popular web performance and security provider offering a free plan with DDoS protection up to certain limits.
- Akamai: Major CDN vendor providing DDoS defense through traffic scrubbing centers.
- Imperva: Top DDoS mitigation vendor using scrubbing network spanning 100+ PoPs.
- Neustar: Ultra-fast scrubbing and DDoS mitigation services up to 3.5Tbps capacity.
- Radware: Full spectrum defense against the network, application, and IoT-based DDoS threats.
During an active attack, these services will reroute traffic to scrubbing centers and filter out bad traffic before passing good traffic back to the origin. This relieves the burden on internal infrastructure.
Most providers offer Always-On services that transparently clean traffic 24/7. There are also On-Demand options that only divert traffic during detected attacks to save costs.
Major DDoS Attack Tools
To perform large-scale DDoS attacks, hackers commonly make use of attack tools and botnets:
- LOIC (Low Orbit Ion Cannon): A simple open-source DDoS tool used to perform basic volumetric attacks like UDP and TCP floods.
- HOIC (High Orbit Ion Cannon): An improved version of LOIC that allows coordinating attacks from multiple sources.
- Botnets: Networks of malware-infected devices that hackers can remotely command to stage attacks. Key examples are the Mirai botnet and its variants.
- Booter/Stresser services: DDoS-for-hire services that provide easy access to botnets and attack methods for a fee.
Attackers are increasingly utilizing botnets composed of Internet of Things (IoT) devices. Their always-on connectivity and weak security make them prime targets. An IoT botnet carried out the massive 2016 Mirai botnet DDoS attack on DNS provider Dyn.
Major DDoS Attack Statistics
Some key statistics highlight the increasing frequency, scale, and impact of DDoS attacks:
- In 2020, there was a 151% increase in DDoS attacks compared to 2019, according to NETSCOUT.
- The average DDoS attack size grew from 5 Gbps in 2019 to 14 Gbps in 2020, per Kaspersky.
- The largest DDoS attack recorded was a 2.3 Tbps attack on an AWS customer in 2020, as per AWS.
- DDoS attacks cost an average of $50,000 per hour, with an average total cost of $2 million, according to Kaspersky.
- Over 80% of organizations surveyed by Neustar experienced at least one DDoS attack in 2020.
- The most targeted industries are telecoms, retail, finance, and SaaS companies.
What are DDoS Attack Stages
Launching a DDoS attack involves several discrete stages:
Compromise Phase
The attacker first builds up their botnet army by infecting vulnerable devices with malware. Targets include IoT gadgets, routers, servers, and improperly secured machines. The wide variety creates larger, more resilient botnets.
Command and Control Phase
Botnets are controlled through a C&C server. The attacker remotely issues commands via the C&C channel to directly connected bots. Advanced botnets use decentralized peer-to-peer C&C.
Attack Phase
When the attack is initiated, the botnet bombards the target with access requests as directed, overwhelming its ability to respond. Attack traffic can originate globally and attract less suspicion.
Malicious Amplification (Optional)
Attackers may exploit third-party servers and protocols to amplify volumes. Small requests elicit huge responses that converge on the victim for greater disruption.
Obfuscation (Optional)
Sophisticated hackers use techniques like IP spoofing and encryption to obfuscate and vary attack origins, making blocking traffic more difficult.
DDoS Attack Tools Evolution
DDoS tools and tactics have evolved substantially:
2000s: Initial IRC botnets could muster 100 Mbps attacks. FLOODNET performed the first known DDoS attack in 1998.
2010s: LOIC and HOIC tools emerge. Hackers utilize DNS and NTP amplification for larger attacks. Attacks routinely exceed 100 Gbps.
Now: Hacked IoT botnets carry out Tbps attacks. Attackers employ novel methods like memcached amplification and polymorphic malware. Highly complex multi-vector attacks are common.
Key drivers of increased DDoS attack prevalence and sophistication include:
- Proliferation of insecure IoT devices
- Availability of user-friendly booter/stresser services
- Refinements in IP obfuscation techniques
- Improved botnet command and control frameworks
- Increasing financial incentives for DDoS extortion
Hackers continue to innovate with new approaches and malware designed specifically to build undetectable attack botnets.
DDoS Mitigation Challenges
The inherently distributed nature of DDoS attacks creates significant challenges for mitigation:
- High volumes of traffic: Huge attack traffic volumes can easily overwhelm standard network and security infrastructure.
- Asymmetric costs: The attacker uses botnets and automation while the victim bears the cost of increased bandwidth and manual response efforts.
- Difficulty isolating attack traffic: Spoofing and the large variety of sources make precisely separating attack traffic tough. Overclocking can cause legitimate users to experience a denial of service.
- Detection difficulties: Many types of DDoS attacks resemble normal spikes in traffic, escaping early detection.
- Temporary solutions: Blacklisting IPs or filter rules applied reactively may drive away the current attack while leaving the organization still vulnerable.
- Multi-vector attacks: Tactics combining high-volume floods, protocol attacks, and application assaults in parallel are especially difficult to mitigate fully.
- One point of failure: Available resources and bandwidth at the perimeter constrain on-premise solutions.
DDoS Protection Laws and Regulations
Many nations have enhanced laws declaring DDoS attacks illegal:
- United States: It is a federal crime under the Computer Fraud and Abuse Act, which extends the definition of cyber terrorism.
- United Kingdom: The Computer Misuse Act 1990 makes it an offense to impair computer systems without authorization. The maximum prison term is up to ten years.
- Canada: Sections 342.1 and 430(1.1) of the Criminal Code outlaw damaging computer systems, and sentences can be up to 10 years in prison.
- Australia: Under the Criminal Code Act 1995, DDoS attackers can receive up to 10 years in prison.
- India: Amendment to the Information Technology Act in 2008 criminalized denial of service attacks with up to 3 years imprisonment.
While enforcement remains challenging, these laws highlight increased recognition of the damage caused by DDoS and deter casual attackers. However, organized cybercriminal groups launching large attacks are less affected by legal risks. For them, the potential profits outweigh any downsides of being caught.
Notable Major DDoS Attacks
Some historically immense DDoS attacks demonstrate how this threat has evolved:
- February 2000: Several major sites, including eBay, CNN, and Amazon, endured sustained DDoS attacks over a few days, with Amazon losing an estimated $600,000 in sales.
- October 2002: 13 DNS root servers received a massive DDoS, almost shutting down DNS globally. This “created the first real sense of threat” around DDoS.
- August 2009: Over several days, a 100 Gbps SYN flood hit financial organizations in South Korea and the United States, causing widespread disruption.
- March 2013: Anti-spam group Spamhaus suffered a 300 Gbps DNS amplification DDoS, which was said to be the largest recorded at the time.
- October 2016: DNS provider Dyn was hit by a 1.2 Tbps DDoS from the Mirai botnet, which is composed of hacked IoT devices, causing major outages.
- February 2020: A massive 2.3 Tbps DDoS tied to a ransom extortion attempt overwhelmed an AWS customer in Europe, setting a new size record.
- June 2021: New Zealand exchange operator NZX suffered a major outage after a reported 500 Gbps DDoS attack, believed to be criminal extortion.
These historic attacks illustrate the escalating power and danger hackers can now wield through DDoS techniques. Even robust enterprises and critical infrastructure can be impacted.
DDoS Attack Prevention Checklist
Use this checklist to review and enhance your protection against DDoS campaigns:
- Maintain overprovisioned internet bandwidth with at least 20% headroom during normal load.
- Implement blocklist capabilities on firewalls and routers to block known attack IPs.
- Deploy intrusion prevention and next-gen firewall systems to detect anomalies.
- Filter obviously malicious protocols like SNMP and SSDP using ACLs.
- Enable SYN cookies on servers to protect against SYN floods.
- Configure load balancers and reverse proxies to absorb and control excess traffic.
- Utilize CAPTCHAs and visitor checks to deter traffic from unverified clients.
- Monitor server health metrics and configure alerting for signs of DDoS impact.
- Validate DDoS detection solutions and ensure WAFs are up to date with the latest threats.
- Divert very large attacks off-premise using DDoS mitigation services.
- Develop and test DDoS emergency response plans regularly.
Final Thoughts
DDoS attacks pose a significant threat to online services and organizations. Understanding the different types of DDoS attacks, such as volumetric, protocol, and application-layer attacks, is crucial for effective defense. Fortunately, various detection and prevention techniques, including traffic monitoring, load balancing, and DDoS mitigation services, can help organizations protect themselves.
By implementing robust security measures and staying vigilant, businesses can minimize the risk of DDoS attacks and ensure the availability and reliability of their online services.
Frequently Asked Questions (FAQs) about DDoS Attack
What is the difference between DDoS and DoS?
The key difference is that a DDoS attack uses multiple distributed sources to overwhelm the victim, while a DoS uses a single source. This makes DDoS much harder to block based on source IP.
What are the most common motivations behind DDoS attacks?
The top motivations are cyber extortion, political/ideological hacking, and competitive disruption against business rivals. Some attacks are also perpetrated by operations testing out capabilities.
What makes IoT botnets ideal for staging large DDoS attacks?
IoT devices are numerous, powerful, rarely secured properly, and always connected, making them perfect vulnerable bots. Their global proliferation enables the assembly of massive, hard-to-trace botnets.
Which industries are the most frequent targets of DDoS attacks?
Telecoms, finance, retail, gaming, software, media, and government sites are attacked most often. Public visibility and financial motivation make them prime targets.
Is it possible to entirely prevent DDoS attacks from happening?
It is unrealistic to fully prevent all DDoS attacks, but the impact can be minimized through DDoS-specific infrastructure, scrubbing services, and effective emergency response procedures.
How long do DDoS attacks normally last?
Attack duration varies widely from a few minutes to over a week. However, most last from 30 minutes to a few hours before systems can recover and defenders can respond effectively.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.