Understanding the Common Formats of SSL Certificates
SSL (Secure Sockets Layer) file extensions refer to files that utilize SSL encryption for secure communications over the internet. Some common SSL file extensions include .pem, .crt, .cer, .p12, .pfx, and more. This article will provide an in-depth look at the most common SSL file extensions, their purpose, and how they are used.
SSL file extensions are used to designate different components involved in SSL encryption. SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are fundamental to internet security, enabling encrypted communication between a web server and browser, email server and email client, and any other client-server software applications.
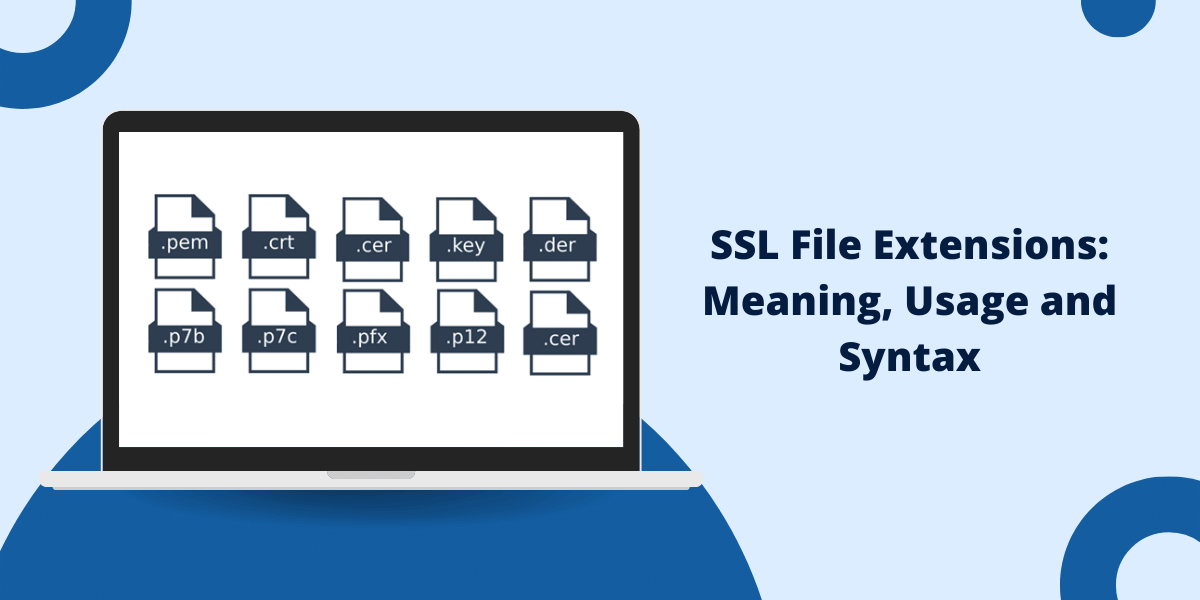
List of SSL File Extensions
- .pem
- .crt
- .cer
- .p7b
- .p12
- .csr
- .key
- .pfx
- .p7c
SSL/TLS Certificate File Formats with File Type & Description
The table below outlines the common file formats used for SSL/TLS certificates. These file formats can be distinguished by their file extensions, which indicate the type and encoding of the certificate data. Understanding these file formats is important when working with SSL/TLS certificates, as the appropriate format is required for different applications and systems.
| File Extenstion | File Type | Description |
|---|---|---|
| .crt | Text or Binary | This is a Base64-encoded X.509 certificate file, which is a common format for SSL/TLS certificates. It can be used for both root/intermediate certificates and end-entity certificates. |
| .cer | Binary | This is another extension for a Base64-encoded X.509 certificate file, similar to the .crt format. |
| .pem | Text | This is a Base64-encoded X.509 certificate file that is enclosed between “—–BEGIN CERTIFICATE—–” and “—–END CERTIFICATE—–” headers. PEM files can contain a single certificate or a bundle of certificates. |
| .der | Binary | This is a binary-encoded X.509 certificate file, as opposed to the Base64-encoded PEM format. DER files are less common but can be used in some cases. |
| .p7b, .p7c | Text | These are PKCS#7 files that can contain a single certificate or a certificate chain. They are often used for certificate enrollment and distribution. |
| .pfx, .p12 | Binary | These are PKCS#12 files that can contain a private key and its corresponding certificate, or a certificate chain. They are commonly used for client-side authentication. |
There are other file extensions used for specific applications as well like .jks for Java keystores. But the extensions listed above represent the core files necessary for enabling SSL encryption on websites, email, and other common implementations.
The rest of this guide will expand on what each file extension is for, how it is used, and why proper file formats are crucial for establishing secure SSL encrypted connections.
PEM Files (.pem)
.pem files are a container format that can contain both public certificates and private keys together or separately. PEM stands for “Privacy Enhanced Mail” and dates back to efforts in the 1990s to establish secure email through SSL/TLS encryption.
A .pem file can be generated using OpenSSL Commands or other SSL tools. Within the PEM file, the private key and public certificate are encoded in Base64 ASCII format bounded by textual headers and footers. This format encoding makes PEM files easy to transmit as text across email and other mediums.
Example of a PEM Encoded Certificate
-----BEGIN CERTIFICATE-----
MIIDdTCCAl2gAwIBAgIJAOlA5pVb6DZkMA0GCSqGSIb3DQEBCwUAMEUxCzAJBgNV
BAYTAlVTMQswCQYDVQQIDAJDQTETMBEGA1UECgwKRXhhbXBsZSwgSW5jLjEVMBMG
A1UEAwwMZXhhbXBsZS5jb20wHhcNMjMwMjE1MTIzNDA1WhcNMjQwMjE1MTIzNDA1
WjBFMQswCQYDVQQGEwJVUzELMAkGA1UECAwCQ0ExEzARBgNVBAoMCkV4YW1wbGUs
IEluYy4xFzAVBgNVBAMMDmV4YW1wbGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAu91lD6Ejb8bHdIhRtlaBPmAx2uZb1h5/h3oGFaK5tX5d7I6s
...
...
...
OqG4P8VoBvHx4+f4dZfOZ4gH6WHTctXbAV3B7xnZ+6W8SsR8YfzXcOq9JlPJhEw+
DT26+oP2Q7eOLA5BtDnH9dFo5pxc2LU7L8Z5eJ6S5onpfmeC4KzFPiQqQ9bFp/s0
3LqIcpl9Stpe2HEa5Fm9Iu1JU/3vtONsUXsxPBJ+pB8A1X5FfdCQpXr5U6QzTfSi
luZl4Uiv0k6pN+5Y9q2cGDodYn9HJ7yL5Z6LxDayeV7/T6W2I1oYbQ==
-----END CERTIFICATE-----
Using PEM Files
PEM files have several uses in establishing SSL encrypted connections:
- Secure Email: PEM files can contain public certificates for secure email exchange through S/MIME encryption. The certificate helps authenticate the sender’s identity.
- Web Server Certificates: PEM files can store the public certificate (and optionally private key) required for establishing HTTPS websites. Web server software like Apache can utilize PEM files for enabling HTTPS.
- Certificate Authority Certificates: Certificate Authorities issue certificates stored in .pem format. Web browsers and operating systems come bundled with root CA certs in .pem format that establish trust.
- Private Key Storage: Along with the public certificate, .pem files can also securely contain the private key for that certificate. This allows a single .pem file to hold all the info needed for SSL encryption.
- Converting other formats: The .pem Base64 encoding makes it easy to convert other file formats like .p12 or .pfx into .pem if needed for specific types of SSL implementations.
The wide support for PEM files across all major operating systems and web servers makes .pem a common format for exchanging and storing SSL certificates, private keys, and certificate authority certificates.
CRT Files (.crt)
The .crt file extension stands for “certificate”. This format contains just the public key certificate needed for SSL encryption. Unlike .pem files, .crt does not contain the private key.
.crt files encode the SSL certificate in a binary format instead of plain text. As part of establishing an SSL connection, the .crt public certificate file for a web server needs to be passed to the client for identity confirmation and encryption.
For example, Apache and other web servers will utilize .crt files containing the certificate bound to that domain name for serving content over HTTPS.
On the client side, .crt certificate files help the client validate the server’s identity based on the certificate signature from a trusted Certificate Authority. Operating systems and browsers come pre-installed with dozens of root CA .crt files from authorities like Comodo, Symantec, GoDaddy, etc.
Example of a .CRT File
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIEbJy1MjANBgkqhkiG9w0BAQUFADBvMQswCQYDVQQGEwJV
...
EwHxY0S2y5+3VqyH5B0+jxM=
-----END CERTIFICATE-----
Using CRT Files
.crt certificate files are used in the following manner for SSL encryption:
- Web Servers: The .crt file for a domain is installed onto the web server hosting that domain to enable HTTPS connections. The certificate binds the domain identity to the cryptographic public key.
- Client Verification: The client receives the .crt certificate file from the server to validate the server’s identity and establish the SSL encrypted session.
- Certificate Authorities: .crt files from root CAs allow clients to automatically trust certificates signed by those authorities without manual installation.
- Browsers: Web browsers come bundled with trusted root CA .crt files so they can verify certificates from trusted CAs without manual installation by the user.
- Converting: .crt files can be exported from .pfx or .p12 certificate bundles. And .crt files can be converted to .pem format if needed.
The .crt file extension is very commonly used for public SSL certificates on the web. It provides a compact and portable certificate format supported across all major browsers and operating systems.
CER Files (.cer)
.cer files also contain public key certificates like .crt files. The .cer file extension stands for “certificate”. These are encoded in the same binary format as .crt files.
.cer and .crt files are technically interchangeable. Both contain just the public key SSL certificate without the private key. Most web servers and other software accept either .crt or .cer file extensions.
The .cer file format is used commonly by Microsoft Windows environments while .crt is frequently used on Linux and Unix systems. But again, both .cer and .crt files serve the same public certificate purpose for SSL encryption.
Example of a CER Encoded Certificate
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIEbJyQmDANBgkqhkiG9w0BAQsFADBoMQswCQYDVQQGEwJV
UzELMAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNhbiBGcmFuY2lzY28xFDASBgNVBAoT
C09wZW5BSSBFeGFtcGxlMR0wGwYDVQQDExRvcGVuYWkuZXhhbXBsZS5jb20gQ0Ew
HhcNMjMwMTAxMDAwMDAwWhcNMjQwMTAxMDAwMDAwWjB8MQswCQYDVQQGEwJVUzEL
MAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNhbiBGcmFuY2lzY28xFDASBgNVBAoTC09w
ZW5BSSBFeGFtcGxlMRwwGgYDVQQDExN3d3cub3BlbmFpLmV4YW1wbGUuY29tMIIB
IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAt0p9zgMkM5a5n/eS8YRGJ1zF
...
...
...
0TwJaMEBw/yXKekuHUfQR+J2Y1ZJU5Qb5sZfccn6UhXzyr6jS3im5TW6WI9K+P5I
9z2S3SfJ4yoG7RQ0z/7c4nEZjeyEd5E7IUTc4zHJ2GkCaw5U+9KcN9EaX0/yFGUG
DQIDAQABo4IBHTCCARkwHQYDVR0OBBYEFK2k2G/mIPbE9Z0NzO3/5E+/wajBMAsG
A1UdDwQEAwIE8DCBhQYDVR0jBH4wfIAUrpTYb+Yg9sT1nQ3M7f/kT7/BqMEuoWyk
YzBhMQswCQYDVQQGEwJVUzELMAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNhbiBGcmFu
Y2lzY28xFDASBgNVBAoTC09wZW5BSSBFeGFtcGxlMR0wGwYDVQQDExRvcGVuYWku
ZXhhbXBsZS5jb20gQ0GCCQGsnpCYMA4GA1UdDwEB/wQEAwIFoDATBgNVHSUEDDAK
BggrBgEFBQcDATAVBgNVHSAEDjAMMAoGCCsGAQUFBwMBMA0GCSqGSIb3DQEBCwUA
A4IBAQBGEM6oLgYhJhUKKvI5Yiyt2/7HnL5q4iO5aUkoFjUuBz0VnPL6/G6qVqj2
...
...
...
nUO8f+OZv2k1R0aBL6KCq9GYY0h+NO8m2O3GmPoWeWJL6PRfMfVLbIDjSYxEghsK
mF92x2V0KihPAtFtGNdd9HGJsb2ffRbE
-----END CERTIFICATE-----
Using CER Files
.cer files serve the same purpose as .crt files in containing solely the public certificate for SSL encryption. The .cer file extension represents “certificate”.
.cer and .crt files are technically interchangeable in practice. But here are some specifics on how .cer public key certificate files are utilized:
- Web Servers: Web servers like Apache or Nginx can use .cer files for SSL/TLS encryption. The .cer file for a domain contains the public certificate presented to clients.
- Client Verification: On the client side, browsers and operating systems verify the .cer file from the server to authenticate the connection.
- Certificate Conversion: .cer files can be exported from .pfx certificate bundles or converted from .pem certificate files if needed.
- Code Signing: Code signing certificates authenticate developers and software. These exist as .cer files bundled with installers.
- CA Certificates: Certificate Authorities issue .cer files for root and intermediate certificates to establish trust chains.
- Microsoft Environments: Microsoft products like Windows Server prefer .cer over .crt for individual certificate files.
P7B Files (.p7b)
.p7b files contain PKCS#7 formatted certificate chains. The “p7b” extension stands for PKCS#7 Binary. This file format can bundle multiple certificates down a chain.
Certificate chains establish a chain of trust from a peer certificate all the way up to a root CA certificate. Chains allow a client to verify that a certificate is signed by a trusted CA.
Here is an example certificate chain contained in a .p7b file:
- Peer Certificate: The site or server certificate issued to that domain. Signed by an intermediate CA.
- Intermediate CA Certificate: The certificate of the intermediate CA that issued the peer certificate. Signed by the root CA.
- Root CA Certificate: The self-signed certificate of the root Certificate Authority. Automatically trusted by clients.
By bundling the chain into a single .p7b file, it makes the chain easily portable and transmittable when installing certificates.
Example of P7B Files
-----BEGIN PKCS7-----
MIIDyjCCArKgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBCwUAMIGcMQswCQYD
VQQGEwJVUzELMAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNhbiBGcmFuY2lzY28xFzAV
BgNVBAoTDlZlcmkgU2lnbiwgSW5jLjEfMB0GA1UECxMWVmVyaSBTaWduIFRydXN0
IE5ldHdvcmsxHzAdBgNVBAMTFlZlcmkgU2lnbiBDbGFzcyAzIENBIDIzMB4XDTEx
MDYwNzAwMDAwMFoXDTE0MDYwNzIzNTk1OVowgZwxCzAJBgNVBAYTAlVTMQswCQYD
VQQIEwJDQTEXMBUGA1UEBxMOU2FuIEZyYW5jaXNjbzEXMBUGA1UEChMOVmVyaSBT
aWduLCBJbmMuMR8wHQYDVQQLExZWZXJpIFNpZ24gVHJ1c3QgTmV0d29yazEfMB0G
A1UEAxMWVmVyaSBTaWduIENsYXNzIDMgQ0EgMjMwggEiMA0GCSqGSIb3DQEBAQUA
A4IBDwAwggEKAoIBAQC3hJFJ6sIhVt+YK34RgL8kQlC0srytZbJ8jxV6kF4AdaWg
qKyr6GoSe2QxIuNlYQ7KkMx2WdQmZ59q2+IbqK3VpLaTCRAlpxpRErjT1eKsLm3L
...
-----END PKCS7-----
Using P7B Files
.p7b certificate chain files are used in these key ways:
- CA Chain Downloads: CAs often provide .p7b chain files to download that contain the full chain up to their root certificate. This eases installation.
- Chained Certificates: Servers can install the .p7b file containing the certificate chain along with the site certificate for establishing trust.
- Root CA Trust: Operating systems, browsers, and devices install root CA .p7b files so all certificates chained to those roots are automatically trusted.
- Intermediate CA Certs: Chained .p7b files allow linking peer certs to intermediate if the root CA is already trusted locally.
- PKCS#7 Support: Nearly all modern clients and servers support importing or exporting .p7b files as PKCS#7 formatted certificate chains.
The .p7b file format provides an efficient way to bundle the certificate chain for distribution and establish the full chain of trust in SSL encryption.
P12 Files (.p12)
The .p12 or .pfx file extension represents a PKCS#12 formatted certificate bundle. Unlike .pem, .crt, and .cer files, .p12 files can contain both the public key and private key together in a single encrypted file.
“PFX” stands for Personal Information Exchange, a legacy format. The newer .p12 extension signifies PKCS#12, an industry standard for storing private keys and certificates. PKCS#12 uses strong encryption to protect the bundle.
Here is what a typical .p12 file contains:
- Public Certificate: The public certificate issued by the CA for the site or domain. Used to verify identity.
- Private Key: The private key paired with the public certificate that enables the SSL encryption.
- CA Certificates: Potentially any intermediate or root CA certificates if needed to establish the chain.
- Encryption: The contents are encrypted via password protection for secure portability.
Having both the public and private components in a single .p12 file makes the bundle very portable and simplifies installation. The encryption provides strong protection.
Example of P12 Files
openssl pkcs12 -in mycert.pfx -out mycert.pem -nodes
Using P12 Files
.p12 or .pfx files are utilized in the following core ways:
- Server Certificates: Web servers and other services install the .p12 for the domain containing the keypair needed for SSL encryption.
- Client Authentication: Clients can authenticate with their own .p12 identity certificate bundle containing their keypair.
- CA Certificate Chains: CAs often provide .p12 chained certificate bundles that include all certificates in the chain.
- Import/Export: Browsers and operating systems support importing or exporting .p12 files with full certificate+key bundles.
- Backup: The encryption enables .p12 bundles to be safely backed up or transferred maintaining privacy of the keys.
The .p12 file extension provides a universal standard through PKCS#12 for bundling private keys with certificates protected by encryption. This makes implementation much easier.
CSR Files (.csr)
.csr files contain certificate signing requests. When applying for an SSL certificate for a domain, the applicant generates a .csr file containing the certificate application info which is submitted to the Certificate Authority.
The .csr file contains:
- Public key: This will be included in the final certificate. The private key is kept secret.
- Domain + company info: Identifying information for the certificate.
- Digital signature: Signed using the private key to verify identity.
Once the CA verifies the application information, the SSL certificate for that domain is issued containing the public key from the .csr file.
On Linux/Unix systems, .csr files are encoded in PEM format. On Windows, they are encoded as PKCS#10 Certificate Signing Requests. But all major CAs and platforms support standard .csr files.
Example of CSR Files
-----BEGIN CERTIFICATE REQUEST-----
MIIC2DCCAcACAQAwgYgxCzAJBgNVBAYTAlVTMQswCQYDVQQIDAJDQTEXMBUGA1UE
...
-----END CERTIFICATE REQUEST-----
Using CSR Files
Here is how .csr certificate signing requests are utilized in practice:
- Certificate Applications: The .csr file is generated by the applicant and submitted to a CA like Comodo or Digicert when applying for an SSL certificate.
- Identity Verification: By signing the CSR with the private key, it proves the applicant’s identity and they hold the associated private key.
- Public Key Delivery: The CA issuing the certificate includes the public key from the .csr in the final SSL certificate.
- Request Generation: The .csr can be generated through tools like OpenSSL or Keychain Access on macOS.
- Automation Support: APIs allow for automated generation, submission, and approval of .csr files for certificate issuance.
The .csr file format provides an automated way for public key delivery during certificate application and issuance for SSL encryption.
KEY Files (.key)
.key files in SSL encryption contain the private key for a public/private keypair. Private keys are kept highly secure as they are one of the core components that enables SSL encryption, used to both decrypt and sign messages.
The contents of a .key file are the private key generated for a specific SSL certificate. Private keys are encoded in different formats:
- RSA private keys are encoded as PKCS#1.
- EC private keys use SEC1 encodings.
In addition to encrypting SSL connections, private keys also digitally sign messages and transactions to prove identity. Possessing the .key file for a certificate is equivalent to possessing the identity tied to that certificate.
Example of KEY Files
-----BEGIN PRIVATE KEY-----
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCx...
...
-----END PRIVATE KEY-----
Using KEY files
Private key .key files are used to enable SSL encryption in the following ways:
- Web Servers: Installing the .key file for a certificate onto a web server allows it to encrypt HTTPS connections using that certificate.
- RSA Key Exchange: The server’s private key enables generating the symmetric keys used in the RSA key exchange to establish the SSL encrypted session.
- ECDSA Signing: ECDSA certificates use the private key for signing the hash of transactions to create digital signatures verifying identity.
- Client Authentication: Private keys allow clients to authenticate servers or services by creating signatures only possible by possession of the private key.
- Securing Keys: Private keys are only distributed in secure methods like .pfx or .p12 bundles. Otherwise .key files stay closely protected.
Private keys must be carefully handled as they represent control over the identity in the respective certificate. The .key file extension provides convenient storage and transferability.
PFX Files (.pfx)
The .pfx file extension is essentially equivalent to .p12 certificates. It similarly represents a PKCS#12 formatted archive that bundles private keys with public key certificates protected by encryption.
Some minor technical differences exist in how .p12 vs .pfx implements PKCS#12. But for all practical purposes, .pfx behaves identically to .p12 files for certificate bundles.
Like .p12 files, .pfx bundles work across all major platforms and browsers with ubiquitous support. The encryption password helps securely transfer keys for installation while preventing unauthorized access.
Example of PFX Files
openssl pkcs12 -in mycert.pfx -out mycert.pem -nodes
Using PFX Files
.pfx certificate bundles are used in the following core ways:
- SSL Server Certificates: Servers install the .pfx file containing the keypair for enabling HTTPS encryption on that domain.
- Client Authentication: Clients can authenticate to servers using a .pfx identity bundle containing their certificate+private key.
- Secure Backup: Encryption allows backing up .pfx files as a secure means of storing certificates and private keys.
- Bundling Certificates: Multiple certificates like intermediates and roots can be optionally bundled within the .pfx archive.
- Legacy Support: Some older systems expect .pfx over .p12 for PKCS#12 certificate+key bundles.
The .pfx extension represents the same PKCS#12 standard as .p12 files while maintaining support on legacy applications that still require .pfx.
P7C Files (.p7c)
The .p7c file extension also indicates a PKCS#7 formatted certificate chain file. It behaves identically to .p7b files for bundling multiple certificates in the chain.
Like .p7b, .p7c files can contain the end-entity certificate along with additional intermediate and root CA certificates for establishing the chain of trust.
The “p7c” extension stands for PKCS#7 Cryptographic Message Syntax. This is very similar to how .p7b indicates PKCS#7 Binary.
Some Windows applications more commonly use .p7c for certificate chains while .p7b is used on Linux and macOS. Otherwise, .p7c and .p7b can be used interchangeably.
Example of P7C Files
-----BEGIN CERTIFICATE-----
MIID2jCCAsKgAwIBAgIJAIdl1V1MOtZnMA0GCSqGSIb3DQEBCwUAMCMxITAfBgNV
...
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIEFzCCAv+gAwIBAgIQDqiqV9bG0O8MFRHYPqE6dzANBgkqhkiG9w0BAQsFADCB
...
-----END CERTIFICATE-----
Final Words
Knowing the meaning behind SSL file extensions provides insight into how certificates, private keys, and other components come together to implement SSL encryption through HTTPS, email security, VPNs, and other protocols.
Using the proper file formats and extensions ensures certificates function correctly for establishing encrypted, trusted connections. Relying on the right files for their intended purpose allows SSL technology to deliver reliable security.
The file extensions above represent the mainstream certificates and key files for enabling SSL across web servers, clients, email, devices, and networks. As new standards emerge, additional extensions may gain adoption.
But the core .pem, .crt, .key, and .p12/.pfx files outlined here form the backbone of SSL certificate management all key stakeholders should understand. With this knowledge, individuals and organizations can properly utilize SSL file extensions within their encryption implementations.