Guide to Sign an Unsigned Driver with Microsoft SignTool
Ensuring the security of your Windows system is paramount, and one way to achieve this is by properly managing your device drivers. Installing unsigned or unverified device drivers can leave your system vulnerable to potential security risks. To address this concern, Microsoft has introduced a robust solution called SignTool, which allows developers to digitally sign their drivers. The process of Sign Unsigned Driver with Microsoft SignTool is essential, as unsigned drivers have not been verified for authenticity.
Without a digital signature, Windows cannot confirm the legitimacy of the driver, leading to potential security vulnerabilities. By utilizing SignTool, developers can obtain a code signing certificate, which they can then use to digitally sign their drivers before distribution.
When you attempt to install an unsigned driver, Windows will block the installation process as a protective measure. This safeguard is in place to prevent the installation of potentially malicious drivers, ensuring the integrity of your system. By adhering to the requirement of digital signing, you can rest assured that the drivers you install are from trusted sources and have been thoroughly vetted.
Microsoft provides a tool called SignTool that can be used to manually sign unsigned driver packages to allow installation on 64-bit versions of Windows Vista and later. This guides you through the steps to use SignTool to securely sign an unsigned driver yourself so it can be installed and loaded on your Windows system.
Key Takeaways
- Unsigned drivers can pose security risks and are blocked from installation on 64-bit Windows.
- Microsoft SignTool allows you to manually sign unsigned driver packages with a code signing certificate.
- SignTool provides more flexibility for loading unsigned drivers needed for testing or new hardware support.
- Properly signing unsigned drivers hardens security by enabling driver authentication.
- Signing requires access to a code signing certificate matching your Windows user account type.
Prerequisites for Signing Unsigned Drivers
Before you can sign an unsigned driver, you need to ensure you have the following:
- An unsigned driver package: These are the .inf and .sys files for the driver you want to sign. Make sure you have the latest unsigned driver files from the vendor.
- Windows 10 64-bit or Windows Server 2016/2019: SignTool driver signing is only supported on 64-bit versions of Windows.
- Administrator access: You need to run SignTool and install signed drivers with admin privileges.
- Code signing certificate: A valid code signing certificate issued to your organization or user account is required. Self-signed certificates cannot be used with SignTool.
- SignTool.exe: Microsoft SignTool is included in the Windows 10 SDK or can be downloaded separately.
4 Easy Steps to Sign Unsigned Drivers with Microsoft SignTool
- Extract the Driver Files from the Installer
- Locate Your Code Signing Certificate
- Use SignTool to Sign the Driver
- Install the Signed Driver Package
Step 1: Extract the Driver Files from the Installer
Most unsigned driver packages are distributed as executable installation files. To access the actual driver files to sign, you first need to extract them from the installer.
This can be done using one of two methods:
Method 1:
- Right-click the installer EXE and select ‘Extract files…’.
- Choose a location to extract the files and click Extract.
- Navigate to the extraction location to find the driver files (typically .inf, .sys, and .cat files).
Method 2:
- Create a new, empty folder.
- Open an administrative command prompt.
- Run the installer executable with the /Extract switch, specifying the empty folder path.
- For example: UnsignedDriverInstaller.exe /Extract C:\UnsignedDriver\
- Navigate to the extraction folder to find the extracted files.
Step 2: Locate Your Code Signing Certificate
The next step is locating a valid code signing certificate (CSC) installed on your computer that matches your Windows user account type.
You can find installed certificates using the Certificate Manager in Windows:
- Open certlm.msc to launch the Certificate Manager.
- Navigate to Certificates: Current User\\Personal\\Certificates or Certificates: Local Computer\\Personal\\Certificates to view certificates for your user account or local computer.
- Look for any code signing certificates issued by a trusted certificate authority (CA) to your organization or user account. The name should indicate it is for code/driver signing.
- If you don’t have a suitable CSC installed, request one from your organization’s IT department or purchase one from a public CA like DigiCert, Comodo, etc.
- Take note of the issuer’s name and certificate thumbprint, which you’ll need later.
Alternatively, you can list certificates from the command line using PowerShell commands like Get-ChildItem Cert:\CurrentUser\My or Get-ChildItem Cert:\LocalMachine\My.
Once you have a code signing certificate ready, make note of its location and identifying details before moving to the next step.
Step 3: Use SignTool to Sign the Driver
With your unsigned driver files and valid code signing certificate ready, you can now sign the driver using the Microsoft SignTool utility.
Here are the steps to sign an unsigned driver using SignTool:
- Launch an elevated command prompt as Administrator.
- Navigate to the folder with your extracted driver files.
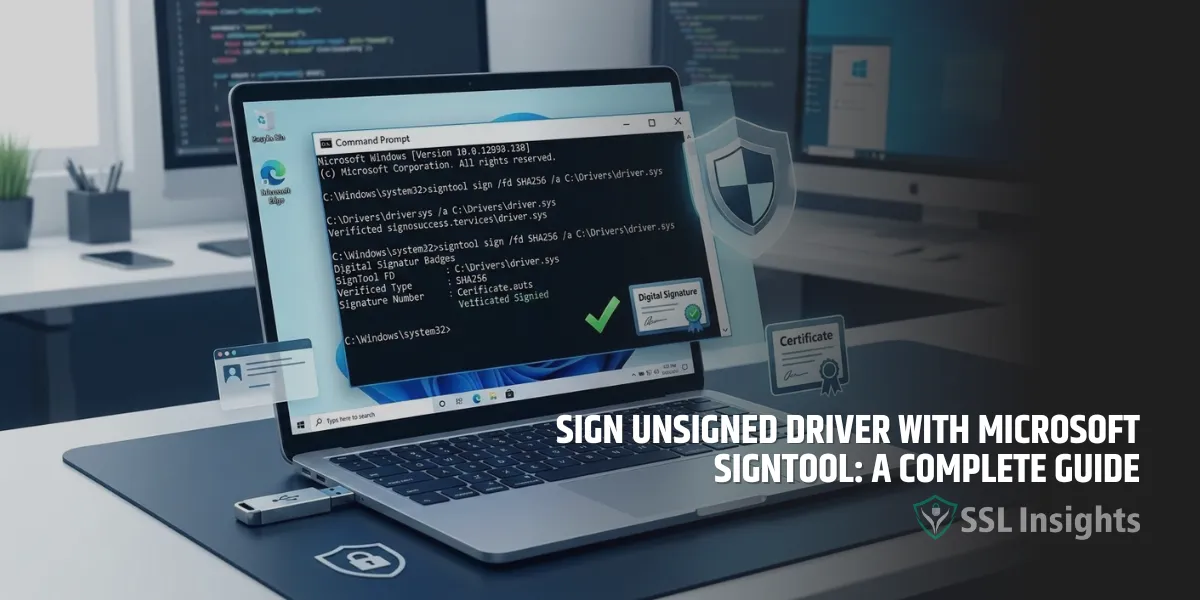
- Run the SignTool command with the following parameters:
SignTool sign /v /ac <CertificateName> /fd SHA256 /tr http://timestamp.digicert.com /td SHA256 <DriverFileName.sys>
- sign: Tells SignTool to sign the file.
- /v: Verbose output. Displays additional status messages.
- /ac: Specifies the code signing certificate to use by its subject name.
- /fd: Sets the file digest algorithm to SHA256.
- /tr: URL of the timestamp server to timestamp the signature.
- /td: Sets the timestamp digest algorithm to SHA256.
- <DriverFileName.sys>: Path to the driver file (.sys) to be signed.
SignTool sign /v /ac "Contoso Code Signing" /fd SHA256 /tr http://timestamp.digicert.com /td SHA256 C:\Drivers\MyDriver.sys
- If successful, SignTool will respond with a Successfully signed and timestamped file.
- You can repeat the SignTool command on any additional .sys driver files in the package.
- Next, use SignTool to sign the .cat catalog file, which stores the hash of the sys file:
SignTool sign /v /ac "Contoso Code Signing" /fd SHA256 /tr http://timestamp.digicert.com /td SHA256 /as /Catalog <DriverCatalogFileName.cat>
- Finally, sign the overall .inf package file:
SignTool sign /v /ac "Contoso Code Signing" /fd SHA256 /tr http://timestamp.digicert.com /td SHA256 /as /f <DriverPackageFileName.inf>
After running SignTool on the .sys, .cat, and .inf files, your unsigned driver package is now properly signed and ready for installation.
Step 4: Install the Signed Driver Package
With the driver package files now signed, you can enable installation and loading of the driver on your 64-bit Windows system.
- Open Device Manager in Windows.
- Right-click on the device requiring the driver and select ‘Update driver.’
- Select ‘Browse my computer for driver software.’
- Click ‘Let me pick from a list of available drivers on my computer.’
- Click ‘Have Disk…’ and point to the folder containing your signed .inf driver package.
- Select your driver from the list and click ‘Next’ to install it.
Windows will verify the driver’s digital signature and allow it to be installed once confirmed as signed. You can check for any installation errors in Device Manager and the driver signing details under the driver’s properties.
Verifying the Driver Signature with SigVerif
To validate that your driver package was properly signed by SignTool, you can use the SigVerif command line utility.
To verify signature validity:
- Open an elevated command prompt as Administrator.
- Navigate to the folder containing your signed driver files.
- Run the command:
SigVerif -v -d <DriverPackageName.inf>
- SigVerif will check the embedded signature and output VERIFIED if the signature is valid.
This confirms that SignTool successfully applied an authenticated code signature to your unsigned driver package.
How to Remove an Unsigned Driver from Windows
If you have an unsigned driver already installed on your Windows system that needs to be uninstalled, follow these steps:
- Open the Device Manager utility in Windows. You can access this by right-clicking the Start menu and selecting “Device Manager.”
- Expand the node for the device whose unsigned driver you want to remove. Right-click on the device driver and select Uninstall.
- In the confirmation dialog, check the option to “Delete the driver software for this device.” This will fully remove the unsigned driver files.
- Click Uninstall to confirm removal of the unsigned driver.
- Restart your computer when prompted to fully clear the unsigned driver from memory. The restart ensures complete removal.
- After restarting, return to Device Manager and click “Scan for hardware changes” so Windows can redetect the device and potentially install a new signed driver automatically.
- If a valid signed driver is not found automatically, you may need to manually install the latest signed driver package obtained from the device manufacturer.
- Verify the new driver has a verified publisher in its properties to confirm the unsigned driver was successfully removed and replaced.
Troubleshooting Driver Signing Issues
Sometimes, issues can arise during the driver signing process that prevents the unsigned driver from installing properly. Here are some common driver signing errors and fixes.
Error: “Windows can’t verify the publisher of this driver software.”
This error indicates that Windows is still detecting the driver as unsigned, even though you signed it using SignTool. Some potential fixes:
- Make sure you signed the .sys, .cat, and .inf files using the correct command line structure in SignTool.
- Verify your code signing certificate is valid and matches your Windows user account type (user vs machine certificate).
- Confirm the certificate’s private key is accessible on your system. You may need to install the matching .pfx file.
- Your system clock must be synchronized for proper signature validation. Use time sync tools if needed.
Error: “Signature verification failed for this driver package.”
Troubleshooting steps for this signature validation error:
- Double-check the driver package using SigVerif to verify that the files were signed properly.
- Use the /td switch in SignTool to specify SHA256 as the timestamp hash algorithm. Some systems require SHA256.
- Make sure your system can access the timestamp server URL used when originally signing the files.
Error: “Windows encountered an error installing the driver software.”
Generic installation errors after signing drivers can have different causes:
- Ensure you are installing the signed driver following the correct device driver update steps for your Windows version.
- Confirm the driver package matches the hardware ID for the device you are trying to update.
- Try installing it on a different Windows machine to determine if the issue is system-specific.
- Check for corrupt or incomplete driver files in the package. Extract a fresh, unsigned package.
Error: “Access denied” when running SignTool
- SignTool must be run elevated as Administrator to access certificates or sign drivers. Make sure to open your command prompt with admin rights.
- Your user account must have read access to the code signing certificate’s private key as well as the driver files being signed.
Final Thoughts
Installing unsigned drivers on 64-bit Windows can reduce system security due to a lack of authentication. However, Microsoft SignTool provides a flexible solution to digitally sign any unsigned drivers you need to use.
By following the steps to properly sign the sys, cat, and inf files with a trusted code signing certificate, you can securely install unsigned drivers while still validating their integrity. Just be sure to only use unsigned drivers when absolutely required since signed ones are always preferable from a security standpoint.
Frequently Asked Questions
Can I use an enterprise code signing certificate to sign drivers?
Yes, as long as it is valid for code signing and matches your Windows user type. Enterprise CSCs issued from your internal PKI can sign drivers if imported correctly.
Do self-signed certificates work with SignTool for driver signing?
No, Microsoft does not allow using self-signed certs with SignTool. You need a certificate issued from a trusted external CA.
Can I renew an expiring code signing certificate used to sign drivers?
Yes, you can renew an expiring code signing certificate and resign your drivers with the renewed certificate using SignTool to maintain validity.
What are the risks of installing an unsigned driver?
Unsigned drivers bypass security checks and could potentially contain malware, making your system more vulnerable to cyberattacks. Only install unsigned drivers if absolutely necessary.
Can I sign drivers for Windows 7 or 32-bit versions?
No, SignTool driver signing is only supported on 64-bit versions of Windows, starting with Windows Vista SP1. Other OSes require different signing methods.
Where can I get a code signing certificate for driver signing?
Major CAs like DigiCert, Comodo, and Sectigo all issue code-signing certificates that are valid for driver packages. Compare costs and validation levels.
What is the benefit of timestamping my signed driver files?
Timestamping the signature extends the validity period so it doesn’t expire if the signing certificate later expires or is revoked.
Does my signing certificate need extended Validation (EV) or Organization Validation (OV)?
Standard Domain Validation (DV) certificates are sufficient for signing drivers as long as they are valid for code signing use.
Can I back up and reuse a signed driver on multiple systems?
Yes, you can reuse a properly signed driver package on other systems. Just make sure it matches the required hardware ID and OS version.
Can I sign drivers for my devices remotely?
Yes, tools like PsExec allow you to remotely execute SignTool on other systems to sign drivers if you have admin access and a valid signing certificate.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.