What is the Difference Between Encryption and Hashing?
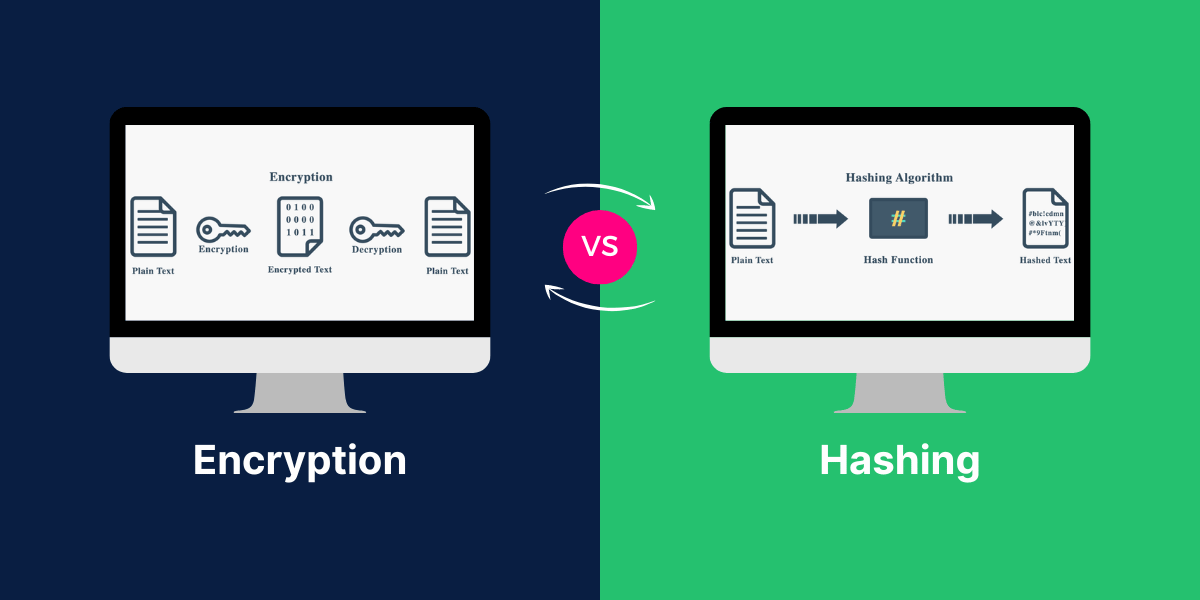
Encryption and hashing are two crucial techniques in the field of cybersecurity, and the differences between “Encryption vs Hashing” are paramount in ensuring the protection of sensitive data. Encryption is the process of transforming information into a coded format, accessible only to authorized individuals with the correct decryption key.
On the other hand, hashing is the irreversible process of converting data into a unique, fixed-length code known as a hash value. While encryption ensures the confidentiality of data, hashing provides a way to verify the integrity of information by detecting any unauthorized changes.
Understanding the nuances between these two methods is essential for implementing robust security measures in various applications, from secure communications to data storage and authentication.
As technology continues to advance, the dynamic interplay between encryption and hashing remains a vital aspect of safeguarding digital assets in an increasingly interconnected world.
Key Takeaways
- Encryption scrambles data using a secret key, allowing authorized parties to reverse the process and read the information. Hashing creates a fingerprint from data that cannot be reversed.
- Encryption provides confidentiality by hiding message contents. Hashing ensures integrity by detecting unauthorized changes to data.
- Encryption can be broken if the secret key is compromised. A hashed value gives no clues to reconstruct the original data.
- Encryption is better for securely transmitting or storing sensitive messages that need to be readable later. Hashing excels at verifying data integrity and creating digital fingerprints.
- Hashing algorithms are generally more resilient against attacks compared to many encryption methods. However, both techniques serve vital purposes in security systems.
Head to Head Comparison Between Encryption vs Hashing
Encryption and hashing serve complementary purposes. Their key differences include:
|
Encryption |
Hashing |
|
Scrambles data in a reversible way |
Creates a fingerprint from data that cannot be reversed |
|
Requires a secret key to decrypt |
Does not use a key |
|
Primarily provides confidentiality |
Mainly ensures integrity |
|
Bidirectional process – encrypt and decrypt |
One-way function from data to hash |
|
Output is the same size as input data |
Output has fixed size regardless of input data size |
|
Broken if attacker obtains key |
Hash cannot be reversed to find original data |
|
Slower performance |
Faster performance |
A Basic Overview of Encryption
Encryption algorithms use mathematical formulas to scramble plaintext data like messages, files, or passwords into an unreadable ciphertext form.
Authorized recipients can decrypt the ciphertext back into usable plaintext if they possess the secret encryption key. This allows sensitive information to be stored and transmitted securely, even over insecure networks.
Some examples of popular encryption methods include:
- AES (Advanced Encryption Standard): A symmetric algorithm using the same key for encryption and decryption.
- RSA: An asymmetric (public-key) algorithm using a public key to encrypt and a private key to decrypt.
- Blowfish, RC4, DES: Other symmetric ciphers.
- PGP, GPG: Encryption programs implementing various algorithms.
The security of encrypted data depends entirely on protecting the secret key. If an attacker obtains the key, they can easily decrypt the ciphertext, making key management a critical concern for encryption systems.
Overall, encryption provides the vital service of confidentiality by hiding message contents. It allows secure communication over untrusted mediums.
A Basic Overview of Hashing
Hashing is the process of converting any data into a fixed-size string of text called a hash value, hash, or digest. It is created by running the data through a hashing algorithm or hash function.
Some examples include:
- MD5: Produces a 128-bit hash
- SHA256: Outputs a 256-bit hash
- Bcrypt: Designed for hashing passwords based on the blowfish cipher
The hash value represents a fingerprint or summary of the original data. Hashing is a one-way function, meaning the data cannot be retrieved from the hash. Slight changes to the input data should drastically change the hash.
Hashes play an important role in verifying data integrity and providing digital fingerprints. Common uses include:
- File integrity checks: Matching hash values can verify file contents have not changed.
- Password storage: Storing hashed passwords instead of plaintext improves security.
- Digital signatures: Document hashes signed with a private key prove authenticity.
- Blockchain ledgers: Transactions are identified by their hash.
Unlike encryption, hashing does not require a key. The security lies in the irreversible one-way nature of hashing algorithms. Hashing provides integrity rather than confidentiality.
Is Hashing More Secure Than Encryption?
Hashing is considered more resilient against attacks compared to some encryption methods. For example:
- There are no keys that can be stolen or compromised with hashing. The one-way nature means hashes cannot be reversed or decrypted.
- Minor changes in input data produce completely different hash values, making it difficult to cause hash collisions or find data that matches a given hash.
- Hashing algorithms like SHA256 have no known vulnerabilities. In contrast, encryption methods like DES and RC4 have been cracked over time.
- The fixed hash length minimizes patterns that could help attackers. Variable encryption ciphertext provides more clues for cryptanalysis.
However, encryption and hashing cannot be definitively ranked as one being more secure than the other. Their different purposes make comparing security meaningless in many cases.
Encryption provides confidentiality for transmitted or stored data according to the encryption strength. Hashing cannot provide confidentiality whatsoever.
Meanwhile, hashing creates integrity checks and digital fingerprints that encryption cannot replicate. Unlike hashing, encryption validity depends entirely on key security.
Should You Encrypt or Hash Data?
Whether to encrypt or hash data depends on your specific goals:
Encrypt data if you want to:
- Securely transmit messages over networks
- Store sensitive data in encrypted form
- Retrieve the original plaintext later
- Provide confidentiality against unauthorized access
Hash data if you want to:
- Verify data integrity
- Check files or passwords without storing plaintext
- Generate file fingerprints for identification
- Create digital signatures on documents
- Enable tamper evidence and proof of knowledge
Use both encryption and hashing when:
- Transmitting hashed data that also requires confidentiality
- Storing encrypted data that needs integrity checks
- Encrypting files where you must verify contents without decrypting
- Adding an integrity check layer to any encrypted data
Examples of Encryption and Hashing Use Cases
Encryption Use Cases
- Email encryption (PGP, S/MIME) allows private communications over email.
- Full disk encryption (BitLocker, VeraCrypt, FileVault)scrambles hard drive data on devices.
- SSL/TLS secures web traffic using encryption between browsers and servers.
- VPNs (OpenVPN, Wireguard) create encrypted tunnels for secure remote access.
- Messaging apps (Signal, WhatsApp) use end-to-end encryption for private conversations.
- Password manager apps encrypt stored website credentials.
Hashing Use Cases
- File integrity checking matches file hashes to detect changes.
- Storing password hashes instead of plaintext passwords improves security.
- Bitcoin and blockchain use hashes to identify transactions.
- Git version control calculates commit hashes to track repository changes.
- Digital signatures validate document authenticity by signing the hash.
- Anti-tamper systems verify firmware hashes on devices.
- Virus scanners identify malware via blacklist hashes.
Hashing Algorithms and Examples
There are many hashing algorithms available, each with different characteristics and purposes:
MD5
MD5 (Message-Digest algorithm 5) is a widely used hashing function that produces a 128-bit hash value. It is fast to compute but is considered cryptographically broken and unsuitable for security use.
MD5(“Hello world”) = fc5e038d38a57032085441e7fe7010b0
SHA1
SHA1 (Secure Hash Algorithm) generates a 160-bit hash. It was designed for speed but suffers from vulnerabilities. Hashing algorithms with larger outputs, like SHA256, are now recommended instead.
SHA1(“Hello world”) = 7b502c3a1f48c8609ae212cdfb639dee39673f5e
SHA256
SHA256 outputs a 256-bit hash and is commonly used for security applications today. Along with SHA512, it offers strong protection against attacks.
SHA256(“Hello world”) = b94d27b9934d3e08a52e52d7da7dabfac484efe37a5380ee9088f7ace2efcde9
Bcrypt
Bcrypt is an adaptive hashing algorithm designed to store passwords securely. It uses key stretching to make brute-force attacks more difficult.
Unlike fast hashes like MD5, bcrypt is intentionally slow by design. A unique salt is also added to each password before hashing to create unique hashes for the same password.
Bcrypt(“password123”) = $2b$12$exbVQ0d38Mrffj6vkiPpd.Xbl51IjSHOiBo1TviNmiCci7kaqPinm
The hashed result contains the algorithm, cost factor, salt, and hashed password. The iterative computation makes decrypting bcrypt hashes orders of magnitude slower than faster hashes like MD5.
Blake2b
Blake2b is a cryptographic hash function optimized for 64-bit platforms. It is highly efficient in software and hardware implementations.
The Blake2 family was created as an alternative to SHA2 and SHA3 to address weaknesses while providing similar security levels.
Blake2b(“Hello world”) = 356a192b7913b04c54574d18c28d46e6395428ab
Scrypt
Like bcrypt, scrypt is an alternative hashing algorithm designed for passwords. It also uses a computationally intensive process to make brute-force attacks impractical.
Scrypt achieves this by using not only CPU cycles but also large memory requirements to slow the calculation.
Scrypt(“password123”) = 10240:8:8:96:f7d1a020692a31f8:12558a686ceff81d4ef1eba3d177e3e78a04cc6ec05afc1b0da1154d248a0644
The parameters in the scrypt hash specify the computational cost and memory usage. This memory hardness protects against hardware brute-force attacks.
Hashing Passwords for Security
Storing user passwords as plaintext in databases is extremely insecure. Hashed passwords provide much better protection.
When users sign up or log in, their passwords are hashed, and only the resulting hash, not the plaintext password, is saved in the database.
To verify later logins, the entered password is hashed again, and the hashes are compared. Matching hashes indicate the correct password without storing it in retrievable form.
Secure password hashing involves:
- Using cryptographic hashing algorithms like bcrypt. Avoid fast hashes like MD5 and SHA1.
- Adding saltunique to each password before hashing to prevent identical hashes for the same password.
- Setting an appropriate cost factor or work factor to make brute forcing expensive.
- Storing the salt alongside the final hash in the database.
Proper password hashing protocols significantly increase the difficulty and cost for attackers. Secure password hashing can slow billions of login attempts per second to just hundreds, providing concrete protection to user accounts and passwords.
Digital Signatures with Hashing
Digital signatures allow messages, documents, and communications to be digitally signed using cryptography. This proves authenticity and prevents tampering.
Hashing is an integral part of creating digital signatures:
- The document contents are hashed to create a message digest hash.
- The hash is then encrypted with the sender’s private key.
- The encrypted hash comprises the digital signature transmitted with the message.
The recipient can verify authenticity by:
- Decrypting the digital signature with the public key to retrieve the original hash.
- Hashing the received document will generate the message digest.
- Comparing the decrypted hash and message digest. If they match exactly, the document’s authenticity and integrity are confirmed.
This scheme proves that the private key owner signed the document and that it was not modified. It relies on hash matching to check integrity.
Final Thoughts
Encryption and hashing are fundamental concepts in data security that serve distinct but complementary purposes. Encryption provides reversible protection and confidentiality through scrambling data with keys. Hashing creates non-reversible fingerprints for integrity checks using one-way functions.
While hashing algorithms are considered more resilient against vulnerabilities, encryption and hashing work hand-in-hand in layered security models. Using both techniques together results in robust protection for data transmission, storage, and verification.
Understanding the different applications of encryption and hashing enables the building of secure systems that leverage their unique strengths.
FAQs About Encryption and Hashing
Is encryption reversible while hashing is not?
Yes, this is one of the main differences. Encryption is a two-way function that scrambles and unscrambles data using a key. Hashing is a one-way function that cannot reverse the data back from the hash.
Can you decrypt a hash?
No, cryptographic hash functions are designed to be impossible to reverse. Hashes do not contain enough data to reconstruct the original plaintext.
Is a hash a checksum?
Yes, cryptographic hashes can be viewed as types of checksums. Checksums are calculated values that verify data integrity. Hashes serve this purpose to detect any changes to data.
How are salts used in password hashing?
Salts are random strings added to each password before hashing. This ensures identical passwords generate unique hashes, preventing dictionary attacks. Salts are stored with the final hash.
Are hashes unique?
With cryptographic hashing algorithms, the chance of two different inputs generating the same hash value is extremely small. Hash collisions are rare but can occur for long data sets.
Is SHA256 better than SHA1?
Yes, SHA256 is considered more secure and less vulnerable to attacks compared to SHA1. SHA256 produces a longer 256-bit hash versus SHA1’s 160-bit hash.
What’s the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same secret key to encrypt and decrypt. Asymmetric encryption uses a public-private keypair where one key encrypts and the other decrypts.
Should you hash or encrypt data for storage?
Sensitive data is typically encrypted for storage to provide confidentiality. Hashing can protect integrity but does not encrypt contents. Using both together is the most secure.
How does blockchain use hashing?
Blockchains like Bitcoin use hashes extensively as transaction identifiers. Block data is hashed to generate identifiers that link blocks sequentially in the chain.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.