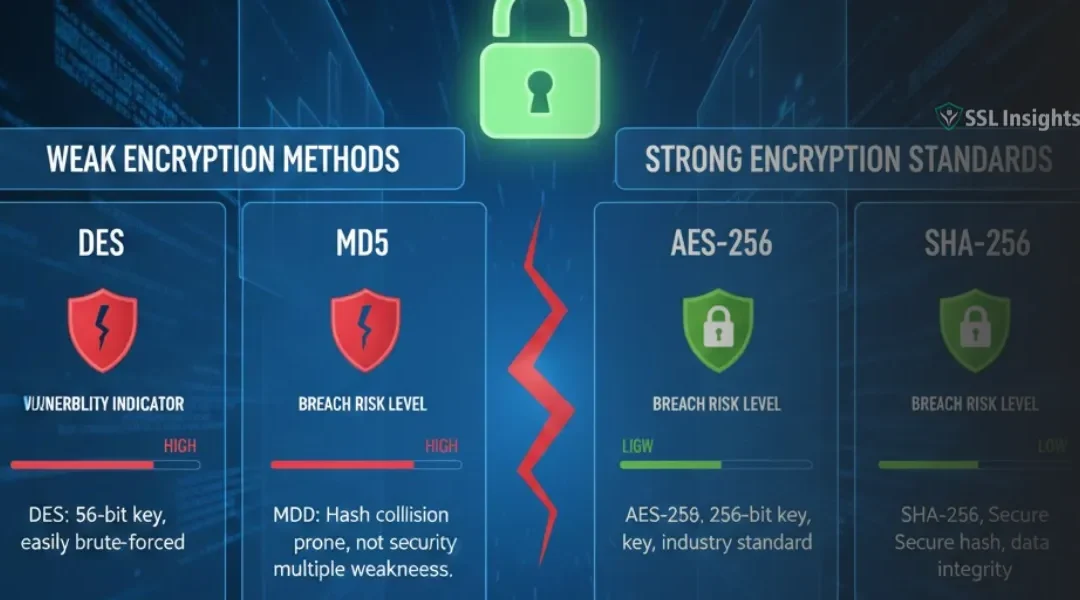
Starting March 15, 2026, the maximum lifespan of public SSL/TLS certificates drops from 398 days to 200 days - and by March 2029, that window shrinks to just 47 days. The CA/Browser Forum passed Ballot SC-081v3 on April 11, 2025, with 29 votes in favor and zero...
![How to Prepare for 47-Day SSL/TLS Certificates: Step-by-Step Transition Guide [2026–2029]](https://sslinsights.com/wp-content/uploads/2026/02/prepare-for-47-day-ssl-tls-certificates-guide-1080x600.webp)