What is Port 80 in TCP?
TCP port 80 is the HTTP (Hypertext Transfer Protocol) port, and it is the most common port number on the World Wide Web. It is used for communicating unsecured web traffic and is used by browsers to make requests to and receive data from servers. You can imagine it as the door your browser knocks on to get to the website.
Port 80 has been around for a number of years, and it has been an essential part of the early Internet to enable the passage of text, images and other information on the web. Although, there are newer and more secure protocols that have been identified, Port 80 is still very much in use especially in legacy systems and low risk applications.
Port 80 Definition
Port 80 is a specific TCP/IP communication port. It runs on the Transport Layer of the OSI model, which is Layer 4, and it helps to support the transmission of data between a client and a server, specifically between a browser and a website. By default, if you don’t assign a port number to a URL when requesting it from a browser, the request is made to Port 80 for HTTP.
What Is Port 80 Used For?
The following are the major applications of Port 80:
- Website Hosting: The common web servers like Apache and Nginx use port 80 to serve the content to the web. For instance, when you decide to read the news your browser communicates with the news site’s server through port 80 in order to request the page you intend to read.
- IoT Devices: There are many types of devices such as security cameras and smart thermostats that use port 80 as a way to talk to and control. This allows the user to navigate and change settings of the device through a web interface.
- Legacy Systems: Some of the applications and systems are built to employ Port 80. For example, some of the current enterprise applications still employ HTTP to talk with other applications.
- Development and Testing: Programmers use port 80 to preview the site locally before releasing it. This guarantees that the site will be ready for the real world once it is launched.
How Does Port 80 Work?
The following is a step by step explanation of how Port 80 works:
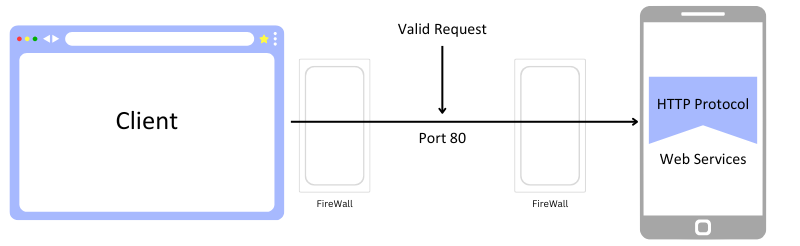
- Client Request: When you type a URL in your search bar, your browser makes an HTTP request to the server on port 80. For instance, if you enter http://example.com, you are requesting the server that hosts that site.
- Server Response: It then receives the request and processes it and then returns the webpage that was requested to be shown to the client. It may contain HTML and images or any other kind of resource.
- Data Transfer: The information is sent across port 80 to your browser, which then does the work of presenting the page to you in its proper format and you are able to see it.
What are the Common Uses of Port 80 in Networking?
This paper focuses on the various uses of Port 80 in different networks. Some of the most common applications include the following:
- Web Servers: It is port 80 that is used in the hosting of websites and other applications we use the internet for.
- Content Delivery Networks (CDNs): CDNs employ port 80 to help shift web content effectively to reduce the time that users spend waiting.
- IoT Communication: Smart devices, including home automation systems, employ port 80 to send and receive information from and to users and other devices.
- Local Development: The port 80 is used by developers in order to test the website in a controlled environment before releasing it to the public.
Why Use Port 80?
Though HTTPS (Port 443) are becoming more popular, there are still some reasons to use Port 80:
- Simplicity: The setup of Port 80 is simple and involves minimal configuration. This makes it very useful for situations that require a quick setup.
- Compatibility: Port 80 is understood by all web browsers and servers without any hassle, making it easily accessible to everyone.
- Low Overhead: Unencrypted data is transferred faster through Port 80 and with less system resources than encrypted traffic.
- Legacy Support: There are still many very old systems and appliances out there that run on Port 80, so it is important to maintain compatibility.
The Pros of Using Port 80
Advantages of Using Port 80 Explanation of the Key Benefits of Port 80:
- Universal Access: The user doesn’t have to do anything special in order to be able to use the websites. This makes it so that anyone can connect to a server without having to install some special client application.
- Speed: The unencrypted data transfer is faster than the encrypted traffic, so Port 80 is suitable for low risk applications.
- Cost Effective: SSL/TLS certificates are not required for Port 80 based servers, it is a cost effective way of hosting publicly accessible information.
- Flexibility: Port 80 is for internal and public use websites and can be used in any way.
The Cons of Using Port 80
However, there are some disadvantages of Port 80 that cannot be ignored.
- Lack of Encryption: In plain text, data is transmitted over Port 80, making it easily interceptible by an attacker.
- Security Risks: HTTP is more secure than HTTP and is prone to attacks like eavesdropping and data manipulation that may result in the disclosure of sensitive data.
- Obsolescence: As more and more sites migrate to HTTPS, Port 80 is becoming irrelevant for many security conscious modern applications.
How to Enable Port 80 on Windows?
The following is the procedure on how to enable Port 80 on Windows operating system:
- Step 1: Open the Windows Firewall settings.
- Go to Control Panel > System and Security > Windows Defender Firewall.
- Step 2: Click on Advanced Settings.
- Step 3: In the left pane, click on Inbound Rules.
- Step 4: Click New Rule in the right pane.
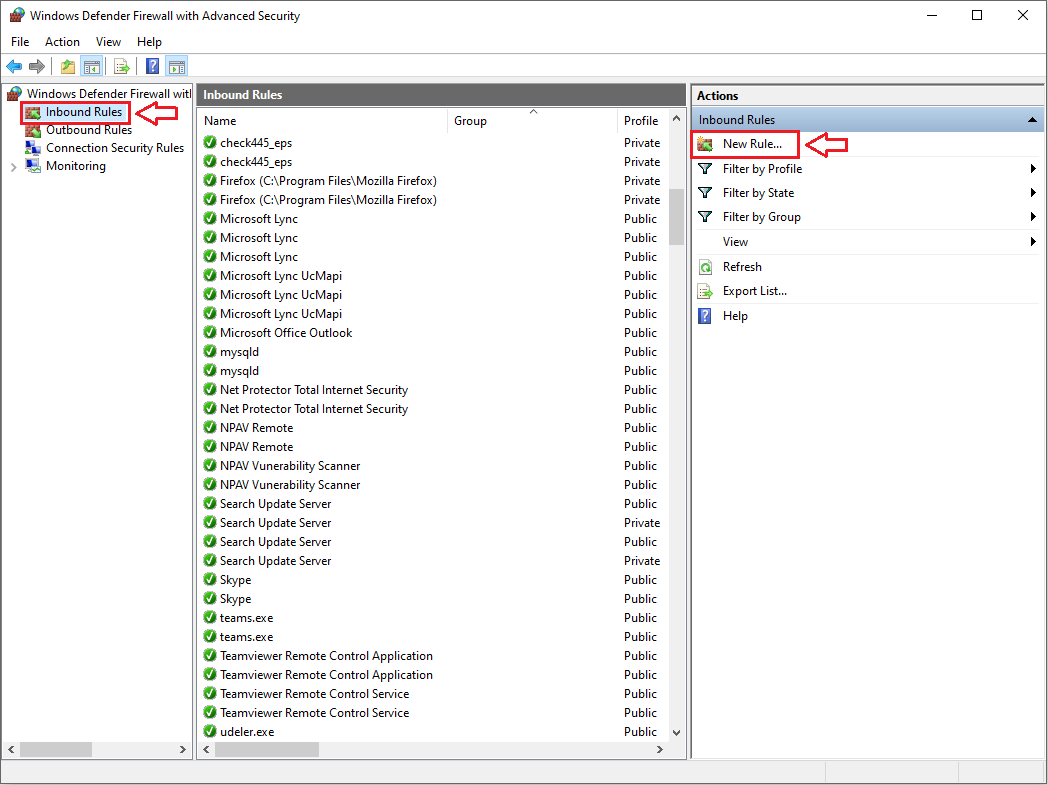
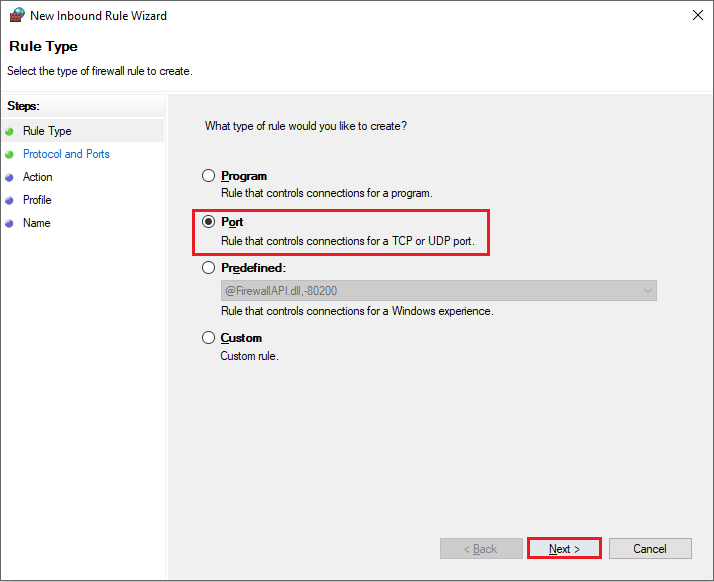
- Step 5: Select Port and click Next.
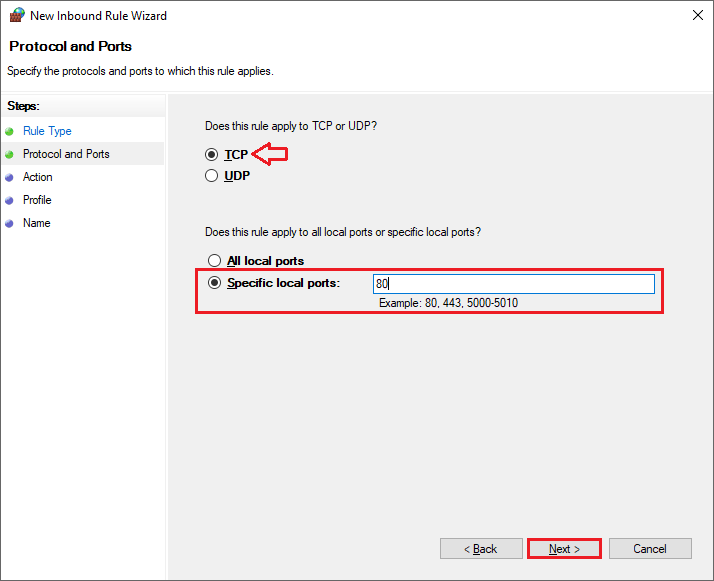
- Step 6: Choose TCP, specify 80 under Specific local ports, and click Next.
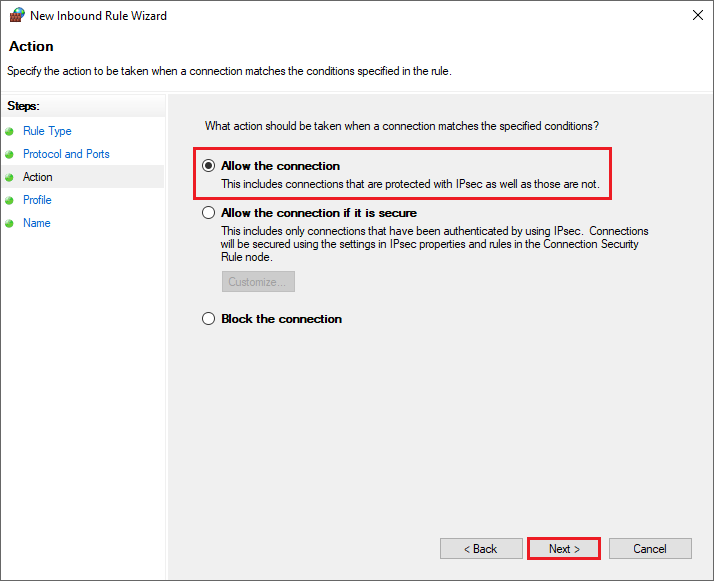
- Step 7: Select Allow the connection and click Next.
- Step 8: Choose the network type (Domain, Private, Public) and click Next.
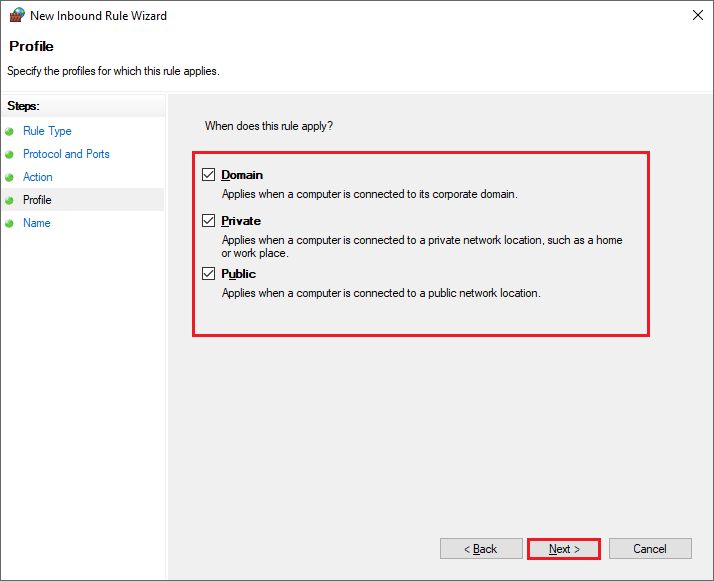
- Step 9: Name the rule (e.g., “HTTP Port 80”) and click Finish.
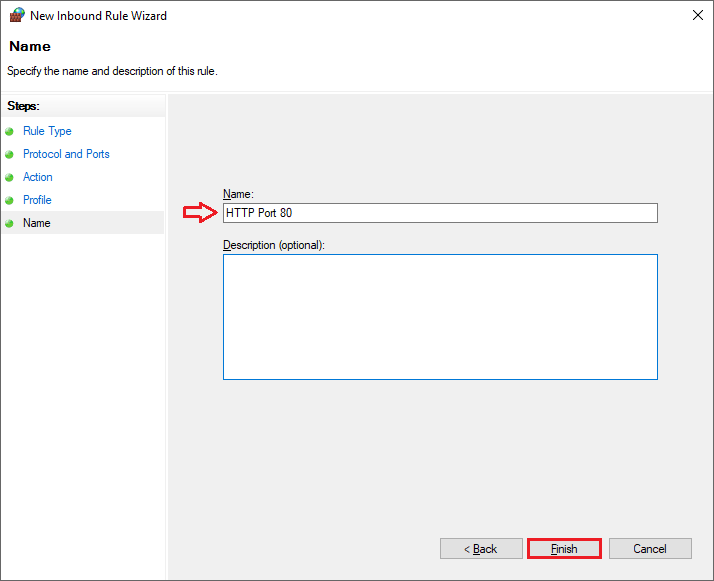
Steps to Enable Port 80 on Mac
The step-by-step guide on how to enable Port 80 on MAC operating system:
- Step 1: Open Terminal.
- Step 2: Check if Port 80 is open:
sudo lsof -i :80
- Step 3: If Port 80 is blocked, allow it using pfctl:
- Edit the packet filter configuration file:
sudo nano /etc/pf.conf
- Add the following line:
pass in inet proto tcp from any to any port 80
- Reload the firewall rules:
sudo pfctl -f /etc/pf.conf
sudo pfctl -e
How to Enable Port 80 on Linux?
Follow the steps to enable Port 80 on Linux operating system:
- Step 1: Open the terminal.
- Step 2: Check if Port 80 is open:
sudo netstat -tuln | grep :80
- Step 3: If the port is blocked, allow it using iptables:
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
- Step 4: Save the iptables rules:
sudo iptables-save
How to Enable Port 80 on Ubuntu?
Follow the step-by-step guide to enable Port 80 on Ubuntu operating system:
- Step 1: Open the terminal.
- Step 2: Use ufw (Uncomplicated Firewall) to allow Port 80:
sudo ufw allow 80/tcp
- Step 3: Reload the firewall:
sudo ufw reload
How to Enable Port 80 on CentOS?
The following is the procedure on how to enable Port 80 on CentOS operating system:
- Step 1: Open the terminal.
- Step 2: Use firewalld to allow Port 80:
sudo firewall-cmd --zone=public --add-port=80/tcp --permanent
- Step 3: Reload the firewall:
sudo firewall-cmd --reload
What are the Security Aspects of Port 80?
The major security risks of Port 80 are:
- Eavesdropping:It exposes the client to exposing of sensitive information like passwords.
- Man-in-the-Middle (MITM) Attacks:This is where a hacker can launch an attack and alter the data in real time or even steal data.
- Data Tampering:This means that sensitive data can be altered or grabbed, resulting in data breaches and legal consequences.
Why Is Port 80 Security Important?
It is very important to secure Port 80 in order to secure confidential data, build and preserve the users’ confidence and to meet the legal requirements of GDPR and HIPAA. Unprotected Port 80 can cause data leakage, financial losses, and harm to the image of the company.
For instance, if an ecommerce site has been taken over by hackers and it uses Port 80 then it can reveal the customers’ credit card details to attackers which may lead to legal and financial consequences.
How to Protect Against Port 80 Attacks?
Below are a set of guidelines on how to secure Port 80 and their explanations:
- Use HTTPS: This is done by forwarding all the HTTP requests to the HTTPS (Port 443) in order to secure the traffic and make it encrypted.
- Implement Firewalls: They are used to deny access to Port 80 and only permit certain IP addresses to access it.
- Regular Updates: This is because servers should be up to date to address vulnerabilities that could be exploited by attackers.
- Monitor Traffic: This means that network traffic can be analyzed in real time for signs of unauthorized activity and blocked.
Is Port 80 Encrypted?
No, Port 80 is not encrypted. It uses HTTP which transfers unencrypted text. To encrypt, HTTPS (Port 443) is needed. For example, when you log in to a website, the username and password you enter are encrypted with HTTPS to protect them from being intercepted.
Is TCP Port 80 (HTTP) Vulnerable?
Yes, several threats exist that affect TCP Port 80, including:
- Eavesdropping: Unencrypted data can be intercepted, that is, eavesdropped.
- DDoS attacks: Port 80 can be flooded with traffic to disrupt service.
- Malware: Exploits can be used to infect systems with malicious software through insecure HTTP connections.
Are Port 80 and 443 the Same?
No, they are not the same. Both are used for web traffic but Port 80 is unencrypted HTTP and Port 443 is encrypted HTTPS. Secure communication prefers port 443 for regular internet traffic and is crucial for secure transactions like online banking or e-commerce.
What Happens If Port 80 is Closed?
If port 80 is explicitly closed in the firewall, websites and applications using regular HTTP will fail to load or be accessible.
Some common scenarios when port 80 gets blocked or closed include:
- Organization security policies restrict access to non-essential ports.
- Local network firewalls block unauthorized internet traffic.
- Cloud providers disable port 80 for their infrastructure by default.
- iptables rules in Linux close off port 80.
- HTTP traffic is denied intentionally to force use of HTTPS.
When port 80 is blocked, users will get timeout errors and be unable to connect via HTTP. But HTTPS sites on port 443 will still work normally.
Admins can reopen port 80 if needed for HTTP services. Though it’s often recommended to use HTTPS and close port 80 for improved security on production systems.
Can You Use Both HTTP (Port 80) and HTTPS (Port 443) on the Same Site?
It is possible to configure a web server or application to listen for requests on both port 80 (HTTP) and 443 (HTTPS) at the same time. This allows supporting both unencrypted and encrypted traffic for the same domain.
Some common use cases for running HTTP and HTTPS parallel on a website include:
- Redirecting all port 80 traffic to HTTPS on port 443. This helps force encryption and improves SEO rankings.
- Serving static assets like images over HTTP while the main site uses HTTPS encryption.
- Allowing legacy or incompatible systems to still access the site in plaintext over HTTP.
- Progressively migrating HTTP pages and content to HTTPS over time.
Common Tools for Managing and Monitoring Port 80
There are many useful tools, both built-in and third-party, for managing port 80 network traffic:
netstat
The netstat command-line tool shows current TCP/IP connections and port status for networking services. It can be used to verify HTTP is listening on port 80.
Telnet
Telnet can directly connect to a port to test if it’s open. For example, “telnet www.domain.com 80” checks if port 80 is accessible on a web server.
curl
The curl program makes HTTP requests from the command-line. It’s useful for testing endpoints and connectivity to port 80 on a server.
Wireshark
Wireshark is a network packet analyzer that does deep inspection of traffic. It can monitor and filter specifically for port 80 packets.
Built-in Firewalls
Most operating systems come with firewalls that can open or close specific ports like 80 based on defined rules.
Web Server Logs
Web server access logs record all requests made. Errors related to port connectivity may show up here for investigation.
Port Scanners like Nmap
Network scanning tools like Nmap check for open ports across IP address ranges. They can identify systems listening on port 80.
Intrusion Detection Systems
IDS/IPS appliances can detect anomalous traffic patterns on port 80 that could signal an attack or unauthorized access attempt.
Final Thoughts
Port 80 has been a part of the internet for many years and it has helped in the movement of web content in a smooth manner. However, because it is not encrypted, it is not as suitable for current, security oriented applications.
This port 80 guide provides a conceptual framework that can be used to help decide between the uses, advantages, and vulnerabilities of Port 80 to enable informed decisions on when and how to use Port 80. Therefore, for secure communication, it is strongly advised to move to HTTPS (Port 443).
Whether you are handling a website, setting up a server, or securing a network, this guide will help you understand how to work in the Port 80 world.
Frequently Asked Questions About Port 80
What is the main use for port 80?
Port 80 is primarily used for unencrypted HTTP web traffic. It allows communication between web browsers and servers via the HTTP protocol.
Is port 80 secure?
No, by default HTTP communication over port 80 is unsecured and transmitted in plaintext. Traffic can be intercepted, and data stolen.
Should port 80 be open or closed?
It depends on the specific requirements. Port 80 should be closed for servers and systems not explicitly needing to serve HTTP content over port 80.
Does port 80 use TCP or UDP?
Port 80 uses TCP as the transport layer protocol. HTTP relies on the reliable delivery and error checking provided by TCP.
Can I run HTTPS on port 80 instead of 443?
This is possible but not recommended as it defies conventions and may cause client-side errors. HTTPS should run on the standard port 443 whenever possible.
What happens if I block port 80?
Blocking port 80 will break access to any sites or services using unencrypted HTTP protocol. Users will encounter connection errors until port 80 is reopened.
Is changing default HTTP port 80 safe?
Changing the default HTTP port can cause compatibility issues and is generally not recommended. Use other solutions like port forwarding or HTTP tunneling instead.
What are alternatives if port 80 is not available?
If port 80 is unavailable, common alternatives include redirecting traffic to HTTPS on 443, using a different port for HTTP via tunneling or port forwarding, or finding other communication channels.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.