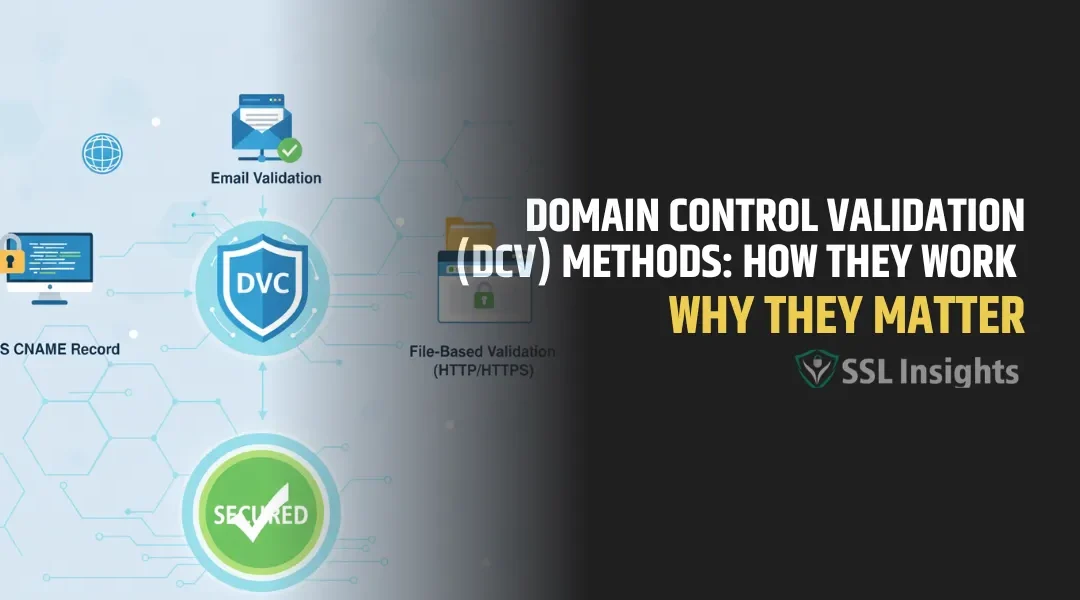
The Sectigo Public Root CA migration requires all active SSL/TLS certificates chaining to Sectigo's older AddTrust External CA Root and USERTrust RSA roots to be reissued under the newer Sectigo root hierarchy before browser and OS trust stores complete their...




![How to Prepare for 47-Day SSL/TLS Certificates: Step-by-Step Transition Guide [2026–2029]](https://sslinsights.com/wp-content/uploads/2026/02/prepare-for-47-day-ssl-tls-certificates-guide-1080x600.webp)