What Does ERROR_SSL_UNEXPECTED_MESSAGE Mean?
The ERROR_SSL_UNEXPECTED_MESSAGE error is a common SSL/TLS issue that can occur in various applications and services that use SSL/TLS encryption for secure connections. This error indicates there was an unexpected issue during the SSL/TLS handshake process that prevented the connection from being established securely.
The good news is this error can often be resolved by making some configuration changes or updating software. Here are some troubleshooting steps to try fixing the ERROR_SSL_UNEXPECTED_MESSAGE error:
Key Takeaways
- The ERROR_SSL_UNEXPECTED_MESSAGE error occurs during the SSL/TLS handshake process and prevents a secure connection from being made.
- Potential causes include expired/invalid certificates, certificate name mismatches, protocol version incompatibility, and more.
- Solutions involve updating certificates, adjusting protocol/cipher settings, installing missing root certificates, and general SSL/TLS troubleshooting.
- Verify certificate validity, match certificate names exactly, enable newer TLS versions like 1.2, and turn off vulnerable cipher suites.
- Clear the SSL state of web browsers, disable proxy/VPN connections, check for malware, and uninstall/reinstall the browser.
- On servers, verify certificate chains, check configuration files, restart related services, and confirm the error occurs across multiple clients.
Steps to Fix ERROR_SSL_UNEXPECTED_MESSAGE
- Verify Certificate Validity
- Match Certificate Names Exactly
- Enable Newer TLS Versions
- Disable Vulnerable Cipher Suites
- Clear Browser SSL State
- Disable Proxy Connections and VPNs
- Check for Malware on Your System
- Uninstall and Reinstall the Browser
- Validate Proper Certificate Chains
- Confirm Configuration Files
- Restart Related Services
- Test From Multiple Clients (Cont.)
- Use SSL Diagnostic Tools
- Contact Certificate Authority
- Consult Your Platform Vendor
Verify Certificate Validity
One of the most common reasons for the ERROR_SSL_UNEXPECTED_MESSAGE error is an expired or otherwise invalid SSL/TLS certificate on the server. Use these steps to check your certificates:
For public certificates, verify that the expiration date has not passed and that the certificate is signed by a trusted certificate authority (CA). Use a free tool like SSL Checker to inspect and validate your certificate.
For private/self-signed certificates, confirm the certificate is not expired and matches the domain name it is assigned to. Ensure the certificate is signed correctly and the root CA is trusted.
Renew soon-to-expire certificates to prevent the error from occurring when they lapse. Generate a new certificate signing request and obtain an updated certificate from your CA.
If your certificate is revoked or untrusted, you will need to obtain a new valid certificate and install it to resolve the issue.
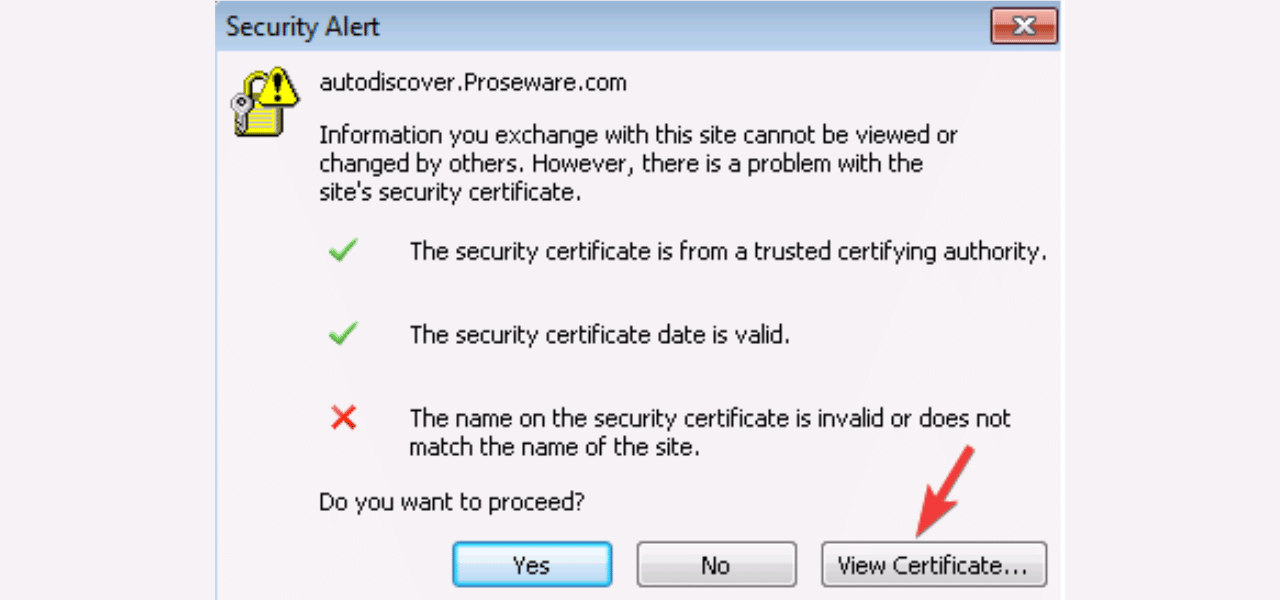
Match Certificate Names Exactly
Another common trigger is a mismatch between the domain name and the SSL/TLS certificate name, also called the common name (CN). Always ensure these names match precisely:
- On the server, verify the domain name (like www.example.com) matches the CN listed on the certificate, including subdomains.
- For clients, check that the domain accessed matches the certificate CN. Clear your DNS cache to eliminate any cached domain name mismatches.
- If the names don’t match, generate a new certificate with the correct CN or domain name. You may need to create a certificate with multiple subject alternate names.
- For internal servers using private certificates, make sure hostnames and IPs accessed match the subjects on the certificate.
Enable Newer TLS Versions
Some applications attempt to establish connections by default using older SSL/TLS versions, which can trigger the error. Try enabling newer TLS versions like 1.2 or 1.3:
- For web servers, update configuration files to enable TLS 1.2 and 1.3 and turn off outdated versions like TLS 1.0/1.1, which are now insecure. Restart the server.
- On clients, check security settings to make sure TLS 1.2 is enabled as a minimum version. Browsers and OS settings may still have older SSL versions enabled.
- Verify both the client and server support at least one standard TLS version, or connections may fail. Check vendor documentation for supported versions.
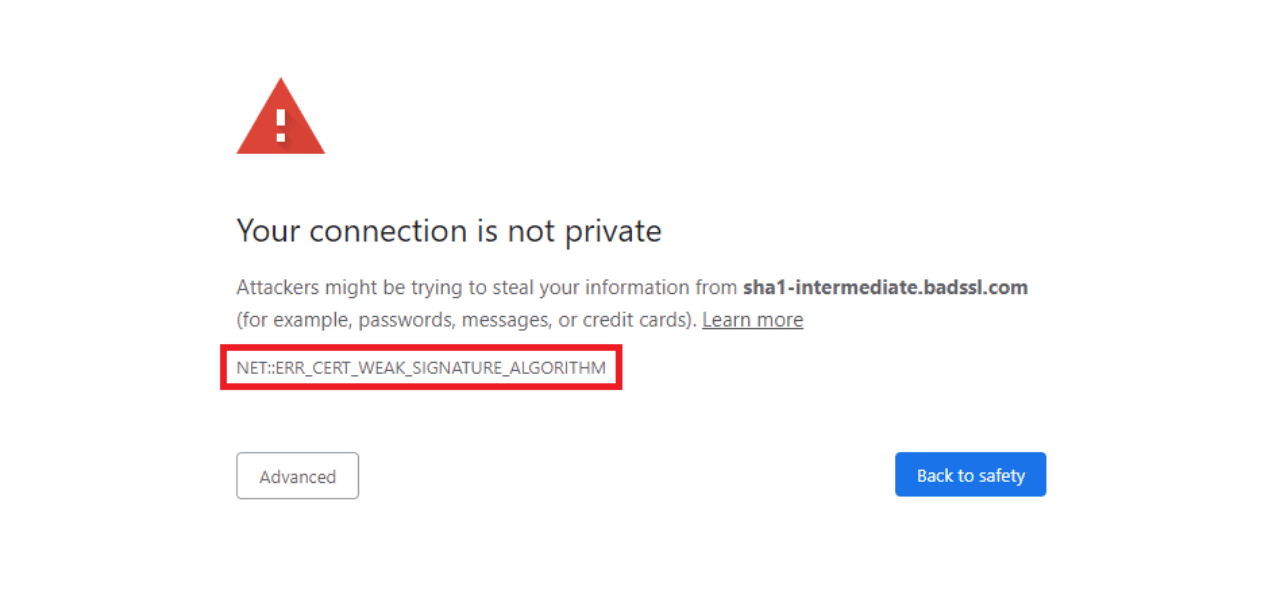
Disable Vulnerable Cipher Suites
Using weak encryption ciphers for the SSL/TLS session can also lead to unexpected errors in establishing secure connections.
- On servers, disable deprecated cipher suites like RC4, 3DES, MD5, and SHA1. Use only strong modern ciphers like AES-128/256 and and SHA256+. Restart services to apply changes.
- For clients, upgrade the software to remove support for vulnerable ciphers – Toggle security options to use only secure cipher suites when available.
- Consider implementing TLS 1.3, which deprecates many insecure ciphers. Enable ECDHE key exchange for PFS.
- Test server/client connections using a tool like the SSL Server Test to confirm only strong ciphers are selected.
Clear Browser SSL State
For errors occurring in web browsers, try clearing your SSL/TLS state to eliminate any problems with cached certificates or settings:
- In Chrome, go to Settings, Privacy and Security, Clear Browsing Data, and select cached images/files, cookies, etc. Restart browser.
- In Firefox, go to Options, Privacy, and Security; scroll down to Clear SSL Form Session & Cookies, and click Clear.
- In Safari, go to Preferences, Privacy, Manage Website Data, and Remove All. Restart Safari.
- In IE, go to Internet Options in the Advanced tab. Click Delete under the Security section. Restart IE.
- On mobile browsers, try Settings, Privacy, Clear History, and Website Data. Toggle on Cookies, Cached Images, etc.
Disable Proxy Connections and VPNs
Browser proxy connections and VPN clients can sometimes interfere with SSL/TLS sessions, causing errors. Try turning off these services temporarily:
- Turn off any browser proxy extensions precisely and manually configure the proxy configuration settings.
- If enabled, disable ‘Use a proxy server’ in browser connection settings. Then, test accessing sites directly without a proxy.
- Disable or uninstall any VPN clients and ensure the VPN connection is disconnected before accessing sites.
- Turn off antivirus or firewall tools that may use SSL/TLS inspection or interfere with secure connections.
Check for Malware on Your System
Malware like viruses, spyware, or rootkits can modify SSL/TLS configurations and cause problems with establishing secure sessions. Scan your system:
- Run a full antivirus scan to check for any infections. Quarantine/remove any malware found.
- If issues persist, try scanning with additional dedicated malware removal tools like Malwarebytes, ADWCleaner, etc.
- Check for any unauthorized root certificates installed on your system and remove them. These may be used to intercept SSL traffic.
- Monitor system processes and network traffic for any suspicious activities indicating compromise or SSL/TLS interception.
Uninstall and Reinstall the Browser
If all else fails, completely uninstalling and reinstalling the browser can reset all SSL/TLS settings and certificates to default and potentially fix the error:
- Backup bookmarks first, then uninstall and delete all browser files/folders. Restart system.
- Download the latest browser installer from the official site and reinstall it freshly. Test error again.
- Check for any pending browser updates and install them if available. Keep the browser up to date.
- If an error persists in multiple browsers, the issue is likely on the server/site rather than the client browser configuration.
Validate Proper Certificate Chains
For errors on the server side, first, verify your certificates are valid and appropriately chained:
- Check that your server certificate is signed and chained to a trusted root CA certificate properly.
- Ensure any intermediate certificates are installed on the server. Open certificate and validate chain.
- A certificate decoder, like an SSL Decoder, can be used to inspect certificate details and the chain of trust.
- Renew soon-to-expired root or intermediate certificates if needed to maintain trust in the chain.
Confirm Configuration Files
Check the server’s SSL/TLS configuration files for any issues with protocols, cipher suites, or certificate paths:
- For Apache servers, verify settings in the SSL.conf file against the SSL/TLS deployment best practices.
- For Nginx, check the configuration in the .conf files under /etc/nginx/conf.d/ against Nginx SSL guidelines.
- For IIS, examine the system.webServer section in the server Configuration Editor for any SSL/TLS misconfigurations.
- Ensure valid certificate paths and proper keys are referenced. Double-check domain names and expiration dates.
Restart Related Services
If you made any configuration changes related to SSL/TLS settings, certificates, or protocols, make sure to restart the associated services to apply changes:
- Restart web servers like Apache and Nginx after ssl.conf or .conf file changes to load new settings.
- For IIS resets, either restart the IIS service or recycle the app pool associated with the site/application.
- For application servers like Exchange or SQL, restart related services like IIS, SMTP, MSSQLSERVER, etc, to reload new certs or protocol settings.
- Stop and start networking services like WinHTTP Web Proxy Auto-Discovery Service if modified.
Test From Multiple Clients (Cont.)
To confirm the issue is on the server side, verify you get the same error when trying to connect from multiple client systems and browsers:
- Test from different physical computers and devices. Try connecting from a mobile device on cellular data instead of your local WiFi.
- Attempt to use alternate web browsers like Firefox, Chrome, Edge, etc. Check both on desktop and mobile platforms.
- If the error persists across different devices, browsers, and networks, the issue is likely server-side.
- Compare behavior for multiple sites on the same server. If one domain fails but others connect fine, the issue may be specific to that site or certificate.
- For intermittent errors, monitor server logs as various clients attempt to identify any patterns.
Use SSL Diagnostic Tools
Specialized tools can provide diagnostics to pinpoint problems in SSL/TLS connections and certificate issues:
- Use online tools like the SSL Checker tool to grade your server config and identify vulnerabilities.
- For deeper inspection, install utilities like OpenSSL, which can directly connect to servers and debug SSL/TLS sessions at a protocol level to uncover issues.
- You can view your server’s encrypted traffic in real-time using a packet analyzer like Wireshark to find anomalies in the SSL exchange.
- Check for certificate issues using a linter like the SSLyze Python tool and confirm compatibility across different clients.
Contact Certificate Authority
If you are having issues with a certificate provided by a public certificate authority, reach out to their technical support, especially if the problem started after a recent renewal:
- Most CAs, such as Comodo, DigiCert, GlobalSign, etc., provide 24/7 technical support and troubleshooting for certificate problems.
- They can help diagnose issues like missing intermediate certificates in the chain, key mismatches, or installation issues on multiple servers.
- Depending on the problem, they may be able to provide a revised certificate to fix it. Have your current certificate details handy when contacting support.
- For verification issues, they can assist with proving domain control and reissuing trusted certificates for your sites using the appropriate validation level.
Consult Your Platform Vendor
For errors limited to a specific app, system, or platform, check with the vendor or developer for SSL/TLS troubleshooting advice or updates:
- Your server OS, database, web server software, programming language platform, etc., may provide guidance on diagnosing difficult SSL issues through forums, docs, or support.
- The vendor may offer updates or patches to address buggy SSL implementations or improve debug logging during SSL sessions.
- For custom apps and systems, the vendor/developer can tailor TLS settings, add exception handling for transient errors, or provide a new client library.
- They may also have workarounds for platform-specific quirks in SSL/TLS compatibility until a permanent fix is available.
By methodically working through these troubleshooting techniques, you should be able to resolve most instances of the pesky ERROR_SSL_UNEXPECTED_MESSAGE preventing secure connections. Failing that, you may need to dig deeper into the specific application architecture, configurations, and SSL/TLS implementation details to isolate and correct the issue.
Frequently Asked Questions (FAQ)
Here are some common questions about the ERROR_SSL_UNEXPECTED_MESSAGE:
Why am I suddenly getting the ERROR_SSL_UNEXPECTED_MESSAGE error?
Common reasons include expired certificates, hidden certificate expirations like intermediates or roots, changes in software updating SSL/TLS libraries, or new security policies turning off old TLS versions or weak ciphers on servers.
What are some common causes of the ERROR_SSL_UNEXPECTED_MESSAGE error?
Invalid, expired, or mismatched certificates, mixed/incompatible SSL/TLS protocol versions, vulnerable cipher suites, malware interference, out-of-date software libraries, invalid certificate chains, and configuration issues.
How can I tell if the error is on the server side or client side?
Try connecting from multiple client devices and browsers. If the error persists on all of them, it likely indicates a server-side issue. Compare access across multiple sites on the same server.
Should I ignore the ERROR_SSL_UNEXPECTED_MESSAGE error?
No, it would help if you addressed it, as it means your connections are not secure and could be compromised by attackers. The error prevents valid encryption and integrity checks.
How do I check if an SSL/TLS certificate is valid?
Use a certificate decoder to inspect expiration dates, chains of trust, and domain matching. Online tools like SSL Server Test can validate your implementation. If needed, contact the certificate authority.
Can antivirus or VPN software cause the ERROR_SSL_UNEXPECTED_MESSAGE error?
Yes, security products that inspect SSL/TLS traffic can sometimes interfere with connections. Try temporarily disabling them and reinstalling them if needed.
Is the ERROR_SSL_UNEXPECTED_MESSAGE error the same across all platforms and apps?
The exact error message may vary across programming languages and platforms but generally indicates the same core SSL/TLS session issue.
Should I revoke my current SSL certificate if I can’t fix the error?
Not necessarily initially. First, try generating a new CSR and obtaining an updated certificate. Revoke only if you confirm the current certificate is irreparably misconfigured.
How do I backup and remove all SSL certificates and settings from a browser?
Each major browser has a “Reset SSL state” or similar option to wipe SSL data. Alternatively, thoroughly uninstall and then reinstall the browser.
Where can I find detailed log files to debug SSL/TLS errors further?
Web servers, load balancers, reverse proxies, and application logs may contain SSL session details. Packet captures also help.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.