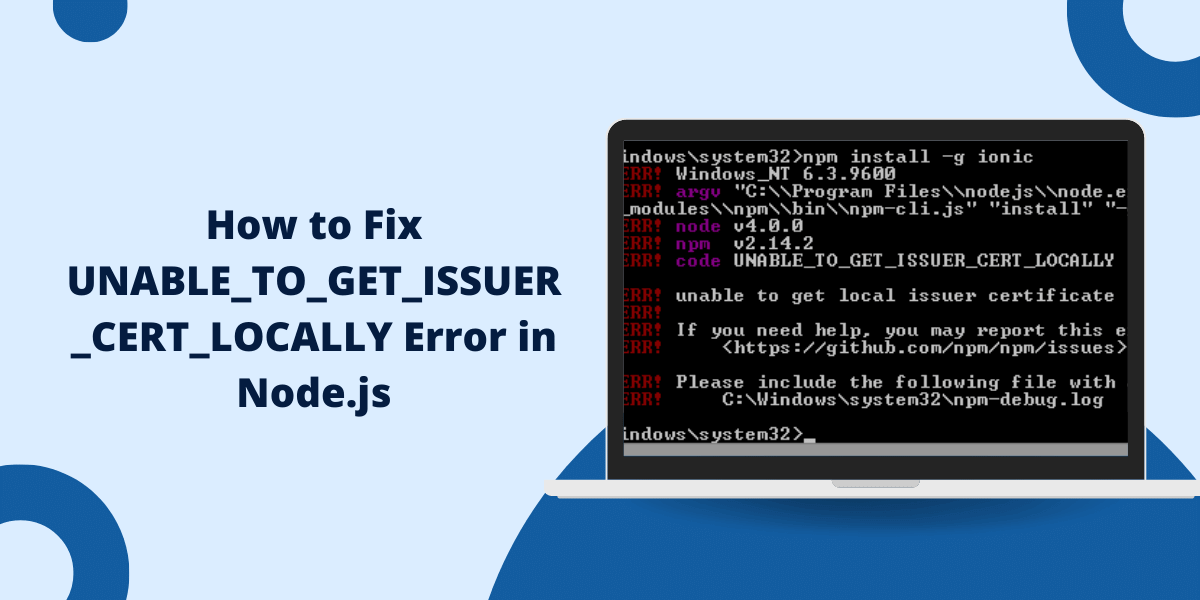
What is the UNABLE_TO_GET_ISSUER_CERT_LOCALLY Error?
UNABLE_TO_GET_ISSUER_CERT_LOCALLY Error is related to SSL/TLS. This error occurs when Node.js or npm fails to validate the certificate chain of a remote server. You will usually see errors such as:
- npm ERR! code UNABLE_TO_GET_ISSUER_CERT_LOCALLY
- npm ERR! errno UNABLE_TO_GET_ISSUER_CERT_LOCALLY
- unable_to_get_issuer_cert: unable to get issuer certificate
- ssl error: unable_to_get_issuer_cert_locally
This is a common error to encounter when writing echo ‘⚠️’; code that makes HTTPS requests, when working with npm packages, or when interacting with most APIs that use SSL/TLS encryption in general. It typically means your local machine does not have the necessary root or intermediate (aka chain) certificates to verify the server’s certificate.
What are Some Common Causes of the UNABLE_TO_GET_ISSUER_CERT_LOCALLY Error
Before we go over the solutions, it’s important to know what’s causing this error in the first place:
- Missing Root or Intermediate Certificates: Your system might not have the required certificates needed to validate the server’s SSL/TLS certificate.
- Self-Signed Certificates: js doesn’t recognize the server as authorized if it is using self-signed certificate which is default.
- Corporate Proxy or Firewall: In some cases, corporate networks intercept SSL traffic which causes certificate validation issues.
- Outdated CA Certificates: Your system’s Certificate Authority (CA) certificates may be outdated, or it might be corrupted.
Step-by-Step Solutions to Fix the UNABLE_TO_GET_ISSUER_CERT_LOCALLY Error
Below are the most effective methods to resolve the unable_to_get_issuer_cert_locally npm or unable_to_get_issuer_cert_locally node js error.
- Update npm and Node.js
- Install Missing CA Certificates
- Disable SSL Verification (Not Recommended for Production)
- Add the Self-Signed Certificate to Your Trusted Certificates
- Configure npm to Use a Custom CA Certificate
- Use the NODE_EXTRA_CA_CERTS Environment Variable
- Check Your Network Configuration
1. Update npm and Node.js
Ensure you’re using the latest versions of npm and Node.js, as updates often include fixes for SSL/TLS issues.
npm install -g npm
nvm install --lts
2. Install Missing CA Certificates
If your system is missing the necessary certificates, you can install them manually. On Linux, use the following commands:
sudo apt-get install --reinstall ca-certificates sudo update-ca-certificates
brew install ca-certificates
3. Disable SSL Verification (Not Recommended for Production)
If you’re in a development environment and need a quick fix, you can disable SSL verification. However, this is not recommended for production as it compromises security.
For npm, set the strict-ssl option to false:
npm config set strict-ssl false
const https = require('https');
const options = {
hostname: 'example.com',
port: 443,
path: '/',
method: 'GET',
rejectUnauthorized: false // Bypass SSL verification
};
const req = https.request(options, (res) => {
console.log('statusCode:', res.statusCode);
res.on('data', (d) => {
process.stdout.write(d);
});
});
req.end();4. Add the Self-Signed Certificate to Your Trusted Certificates
If you’re working with a self-signed certificate, you can add it to your system’s trusted certificates.
- Download the certificate (e.g., server.crt).
- On Linux or macOS, add it to the CA certificates directory:
sudo cp server.crt /usr/local/share/ca-certificates/
sudo update-ca-certificates
- On Windows, import the certificate using the Certificate Manager.
5. Configure npm to Use a Custom CA Certificate
If you’re behind a corporate proxy, you may need to configure npm to use a custom CA certificate.
- Obtain the CA certificate from your network administrator.
- Set the cafile configuration in npm:
npm config set cafile /path/to/your/ca.crt
6. Use the NODE_EXTRA_CA_CERTS Environment Variable
Node.js allows you to specify additional CA certificates using the NODE_EXTRA_CA_CERTS environment variable. This is useful if you don’t want to modify the system’s certificate store.
- Export the environment variable:
export NODE_EXTRA_CA_CERTS=/path/to/your/ca.crt
- Restart your Node.js application or npm process.
7. Check Your Network Configuration
If you’re behind a proxy or firewall, ensure that your network settings are correctly configured. You may need to set the proxy and https-proxy settings in npm:
npm config set proxy http://your-proxy-url:port
npm config set https-proxy http://your-proxy-url:port
How to Avoid the unable to get local issuer certificate nodejs Error in the Future?
To ensure that you do not run into this error again, please adhere to the following best practices:
- Update your system’s CA certificates at regular intervals.
- Do not use untrusted SSL certificates in your servers.
- Do not disable SSL verification in the production environment.
Final Thoughts
The unable to get the issuer’s certificate from the local region can be a problem, but it can be easily solved as explained above. Whether you are facing the npm err! code unable_to_get_issuer_cert_locally or ssl error: unable_to_get_issuer_cert_locally, the solutions given above should be helpful in resolving the problem. Please, always secure your production environments as this is one of the most critical measures that should be taken.
As a result of this guide, you will be in a position to easily tackle the unable_to_get_issuer_cert_locally npm or unable_to_get_issuer_cert_locally node js error and make your development processes more efficient.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.