What Does DLG_FLAGS_SEC_CERT_CN_INVALID Error Mean?
The error code DLG_FLAGS_SEC_CERT_CN_INVALID indicates that there is an issue with the security certificate common name validation when trying to establish a secure TLS connection. This error typically occurs when connecting to a website or web service that uses TLS encryption. Some common causes and fixes for this error are:
Understanding the Error DLG_FLAGS_SEC_CERT_CN_INVALID
The DLG_FLAGS_SEC_CERT_CN_INVALID error occurs when the common name (CN) field of the website’s security certificate does not match the domain name you are trying to connect to. The CN field should contain the domain name (e.g. www.example.com) to ensure you are connecting to the authentic site and not an imposter.
When your system attempts to validate the certificate CN against the domain name you requested, it determines the names do not match. This causes the certificate validation to fail and the error to be returned.
Some common reasons why the CN may not match the domain include:
- The website configuration is outdated and points the CN to an old domain name.
- The certificate is a wildcard certificate meant to secure multiple subdomains, but the CN does not match your request.
- There is a man-in-the-middle attack intercepting the connection and presenting an invalid certificate.
Step-by-Step Guide to Fix DLG_FLAGS_SEC_CERT_CN_INVALID Error
Fixing this error depends on the specific cause. Here are some troubleshooting steps to resolve common issues:
- Checking the Website Domain and Certificate
- Fixing Domain Mismatch Issues
- Checking for TLS Interception
- Updating Security Software Configurations
- Adding Security Exceptions
- Replacing Certificates
Checking the Website Domain and Certificate
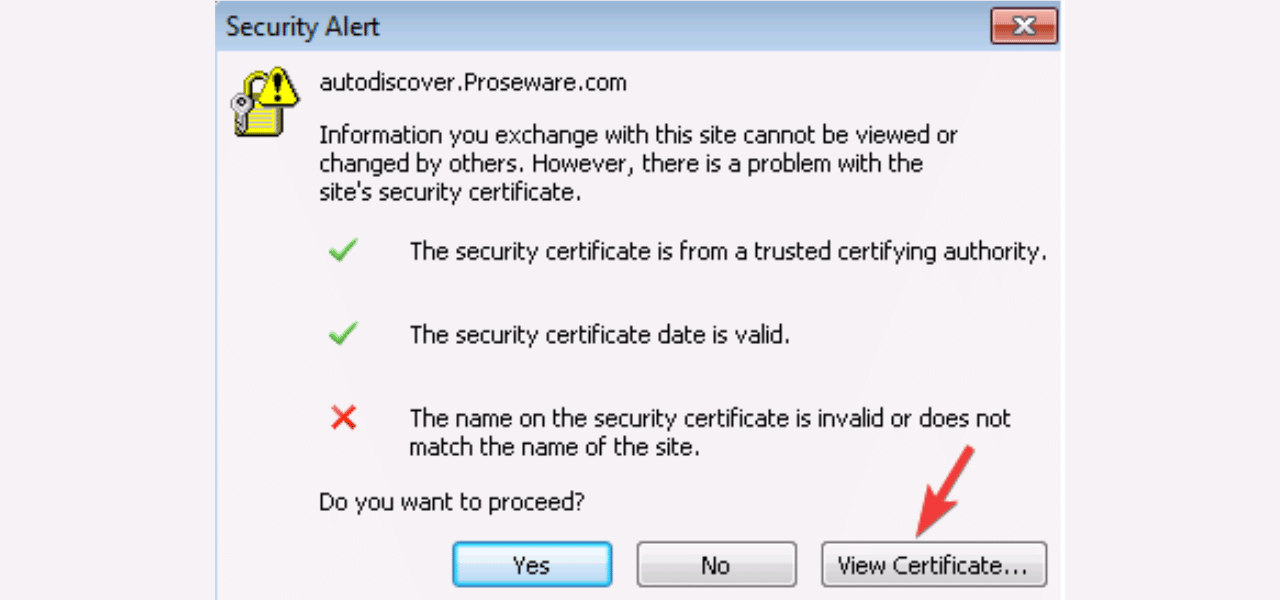
When you encounter the DLG_FLAGS_SEC_CERT_CN_INVALID error, first double check that the website domain you are attempting to connect to is correct and matches the valid CN for that site’s certificate.
You can inspect the certificate CN by either:
- Using an online SSL checker tool to view the certificate.
- Using OpenSSL commands to connect to the site via command line and view the cert details.
- Checking on the server itself if you have backend access.
- This will confirm if there is simply a domain/CN mismatch or if the server certificate itself is misconfigured or invalid.
Fixing Domain Mismatch Issues
If you confirm the domain you are attempting to access is valid and the certificate CN is different, try these steps:
- Clear your DNS cache and flush DNS to ensure you don’t have an outdated DNS record.
- Try accessing the site by IP address instead of domain in case there is a DNS resolution issue.
- Contact the site owner to inform them of the invalid CN on their certificate. They will need to update it.
- Add an exception for that specific domain if the CN mismatch is due to a wildcard cert issue.
These steps will validate where the domain resolution issue occurs and determine if it’s client-side or requires the server owner to update their configurations.
Checking for TLS Interception
Another cause of CN mismatches is if there is TLS inspection or man-in-the-middle interception occurring on your network. This could be due to:
- A firewall, VPN, or proxy intercepting TLS traffic and presenting its own certificate.
- Malware or virus that has infected your system and hijacks traffic.
To identify if this type of interception is the issue:
- Connect from another network or device and see if error still occurs.
- Check security software settings and disables TLS/SSL scanning features.
- Run antivirus scans to check for malware.
- Use a packet sniffer to inspect traffic for anomalies.
This will help determine if there is something intercepting the connection and causing the invalid certificate error.
Updating Security Software Configurations
In some cases, the DLG_FLAGS_SEC_CERT_CN_INVALID error may occur if security software such as antivirus or firewall has outdated root certificates or certificate validation rules.
Try updating these applications to their latest versions and resetting configurations to reinstall root certificates:
- Update antivirus/internet security software to latest version.
- Reset web filtering and TLS inspection rules.
- Clear and reinstall root certificates on the system.
- Disable any proxy auto-configuration scripts temporarily.
Once updated, the security software should be able to validate the certificate correctly without error.
Adding Security Exceptions
If the certificate CN mismatch is due to a legitimate reason like a wildcard certificate or redirected domain, you can add a security exception to allow the connection:
- In web browsers, find the certificate error options and choose to add a permanent exception.
- On Linux/Unix systems use the curl utility with the -k flag to accept insecure certificates.
- For other applications, look for trust store or certificate management options to add exceptions.
This will essentially bypass the CN validation error and allow you to connect to the site. However, exceptions should only be used after verifying there isn’t a man-in-the-middle issue occurring.
Replacing Certificates
In some situations, the DLG_FLAGS_SEC_CERT_CN_INVALID error may persist even after troubleshooting steps if the certificate is invalid, corrupt, or misconfigured. In this case, it may be necessary to reissue or replace the certificate entirely.
On the server side, this would involve:
- Generating a new certificate signing request (CSR).
- Submitting the CSR to a certificate authority (CA) to issue a new trusted certificate.
- Installing the new certificate and updating services to use it.
For client-side issues, solutions include:
- Installing a new trusted root certificate bundle.
- Importing a new CA root certificate.
- Updating software to recognize an updated public CA certificate.
By replacing the certificates, it essentially creates new trust between the client and server which should resolve validation errors.
Final Thoughts
The DLG_FLAGS_SEC_CERT_CN_INVALID error indicates an issue with the common name validation when establishing a TLS connection. Misconfigurations, malware, TLS interception or invalid certificates are common causes. By checking for domain and CN mismatches, updating software, replacing certificates, and adding exceptions, you can resolve this error and restore secure access. Proper diagnosis and caution when adding exceptions is key to avoiding potential security risks.
FAQs
What causes the DLG_FLAGS_SEC_CERT_CN_INVALID error?
This error is caused by a mismatch between the common name (CN) field of the security certificate presented and the domain name you are attempting to connect to. This results in a failed certificate validation.
What are common names (CN) mismatches?
CN mismatches happen when the CN record in the certificate does not match the domain you are accessing. This is often due to misconfigurations, wildcard certificates, or interception proxies.
How do I view a certificate’s CN value?
You can use online tools, OpenSSL, or view it on the web server itself to inspect the CN value in the certificate. This allows you to compare it to the domain you are accessing.
Can I prevent the error by adding an exception?
In some cases, you can add a security exception to bypass the CN validation. However, this reduces security, so only do this after verifying no MITM attacks are occurring.
When do I need to reissue or replace a certificate?
If troubleshooting steps don’t resolve the issue, it may be necessary to reissue the certificate or install a new one to fix the DLG_FLAGS_SEC_CERT_CN_INVALID error.
Is the error caused by malware or viruses?
Sometimes malware and viruses can intercept SSL connections, causing CN mismatches. Antivirus scans and connecting from other devices can help identify this issue.
How do I confirm the domain I’m connecting to?
Check your requested domain against WHOIS records, DNS entries, and any access logs to confirm the exact valid domain and CN needed to connect securely.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.