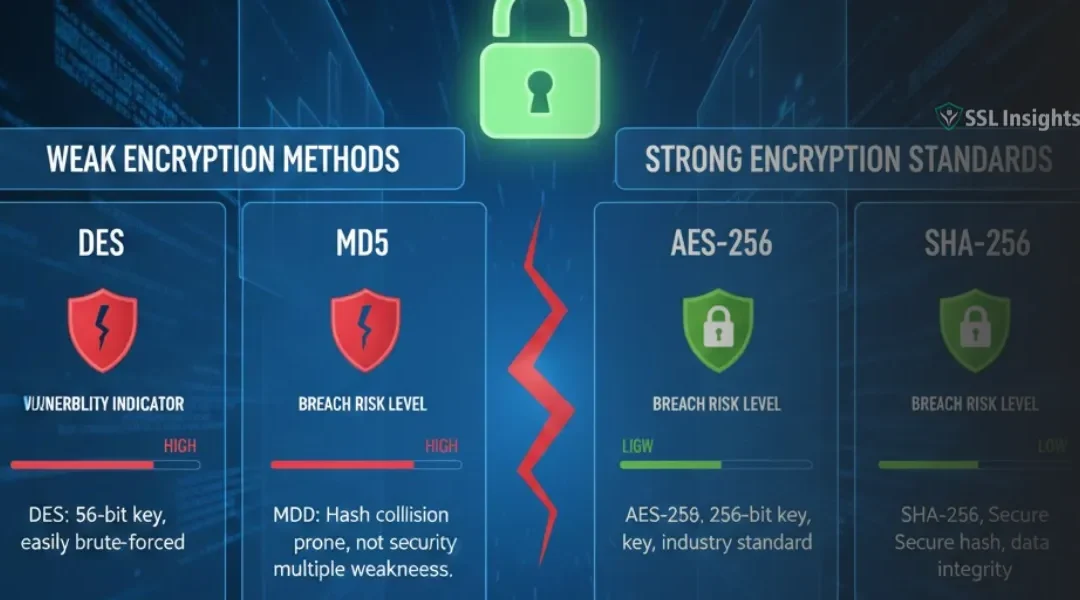
Weak encryption exposes your data to interception, theft, and manipulation by attackers who can break outdated security protocols. Organizations using algorithms like DES or MD5 face regulatory penalties, reputational damage, and financial losses from breaches that...