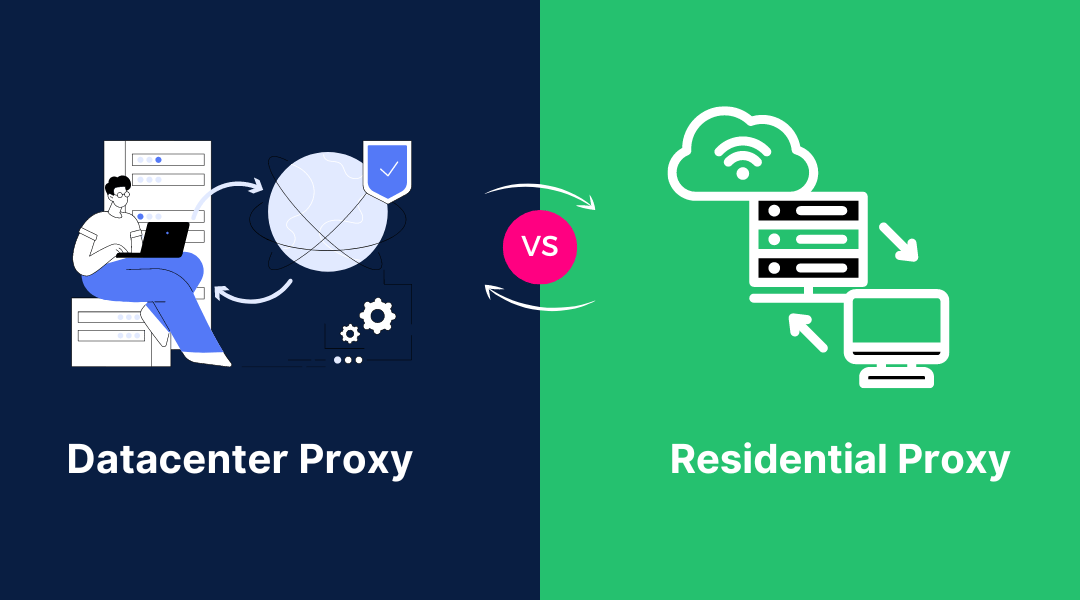
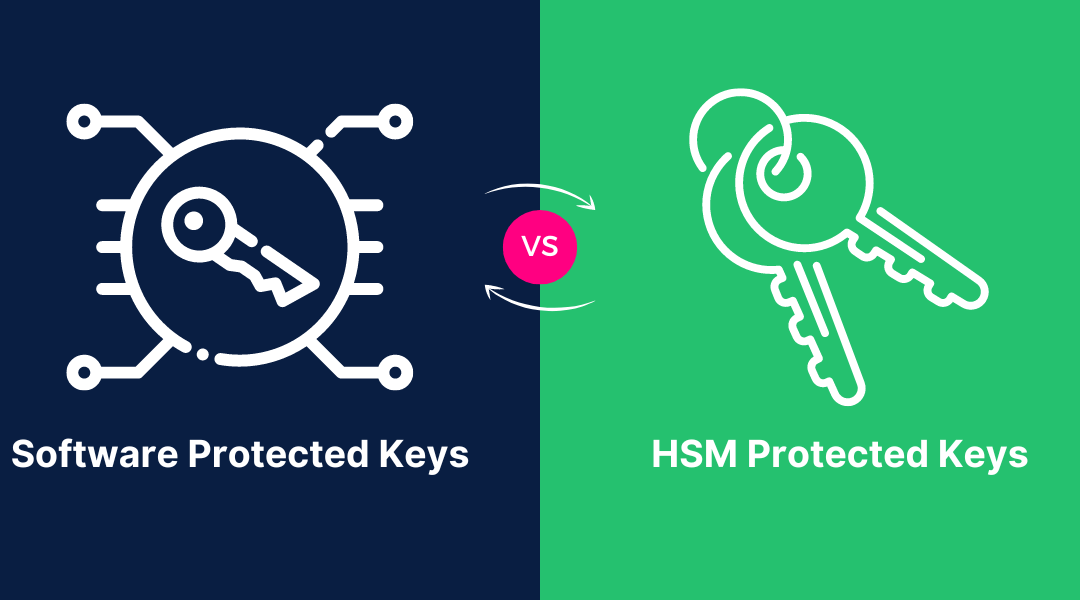
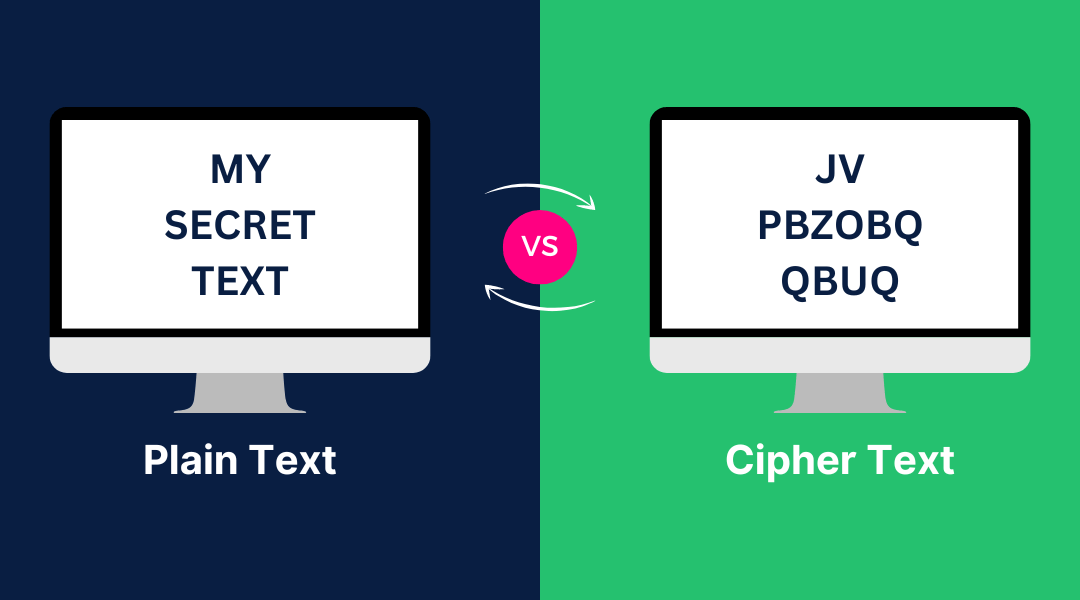
Know the Difference Between Datacenter Proxy and Residential Proxy Proxies are an essential tool for many online activities. They provide anonymity and bypass access restrictions. The two main types of proxies are data center proxies and residential proxies, which...