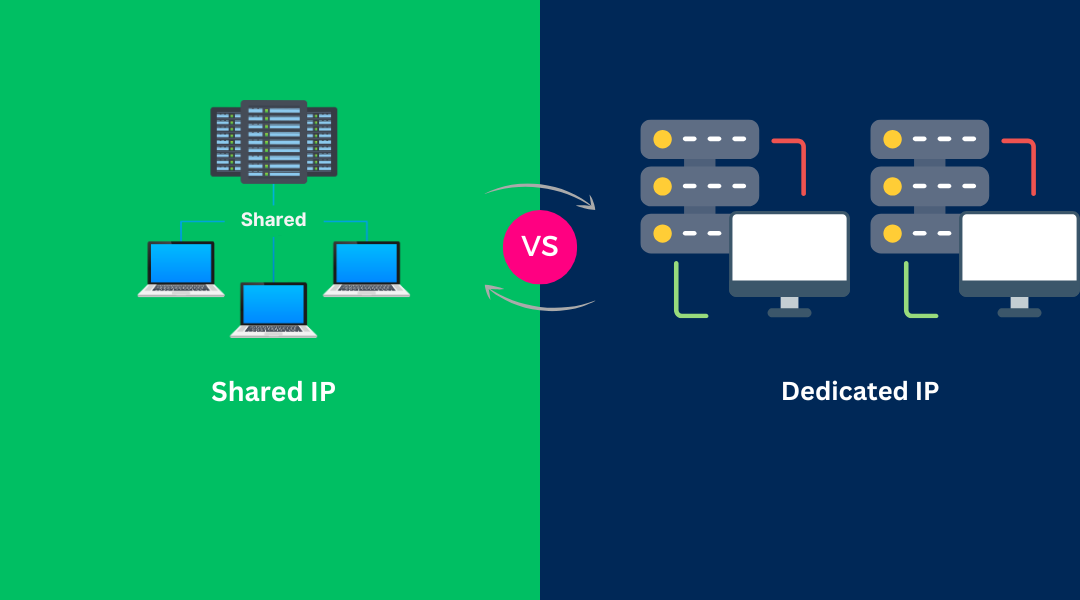
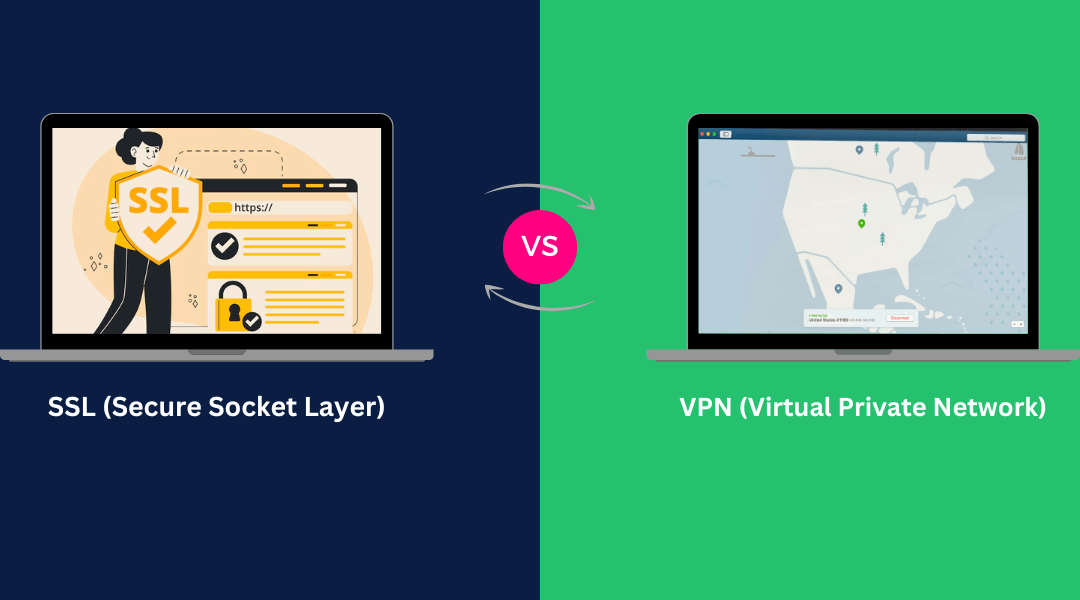
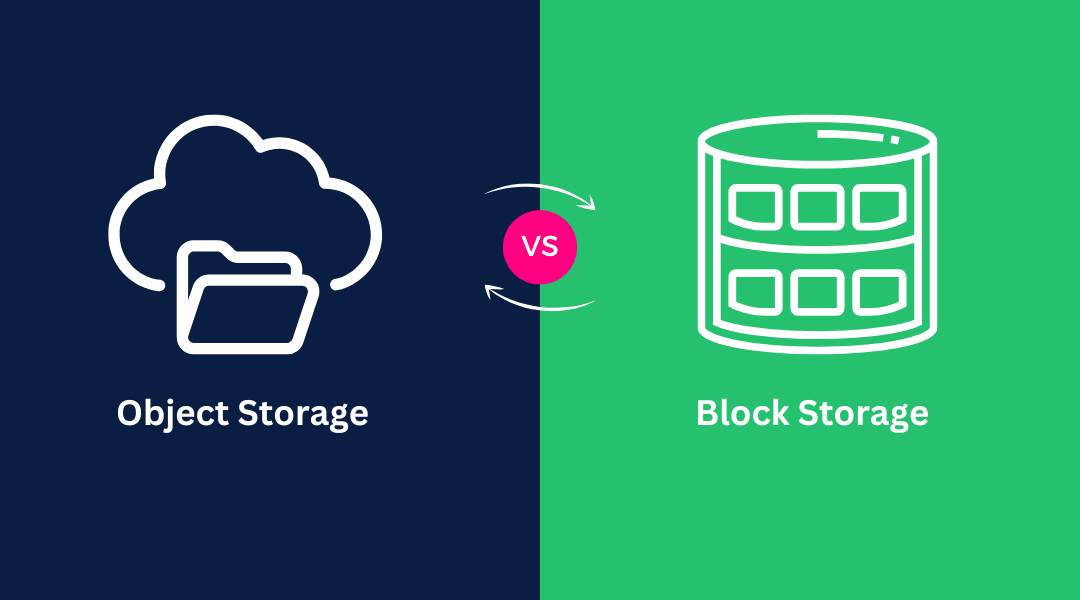
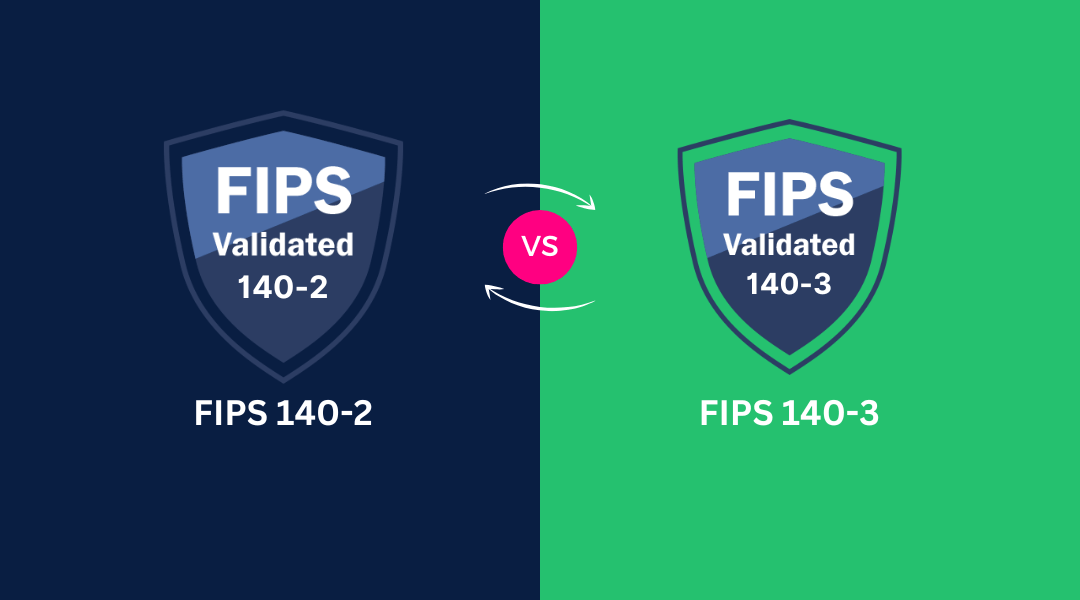
What's the Difference Between Port 80 and Port 22 The two computer networking ports function differently from each other. The default port for HTTP traffic is Port 80, which enables standard web browsing and unencrypted data exchange between web servers and clients....