What is SSL Inspection?
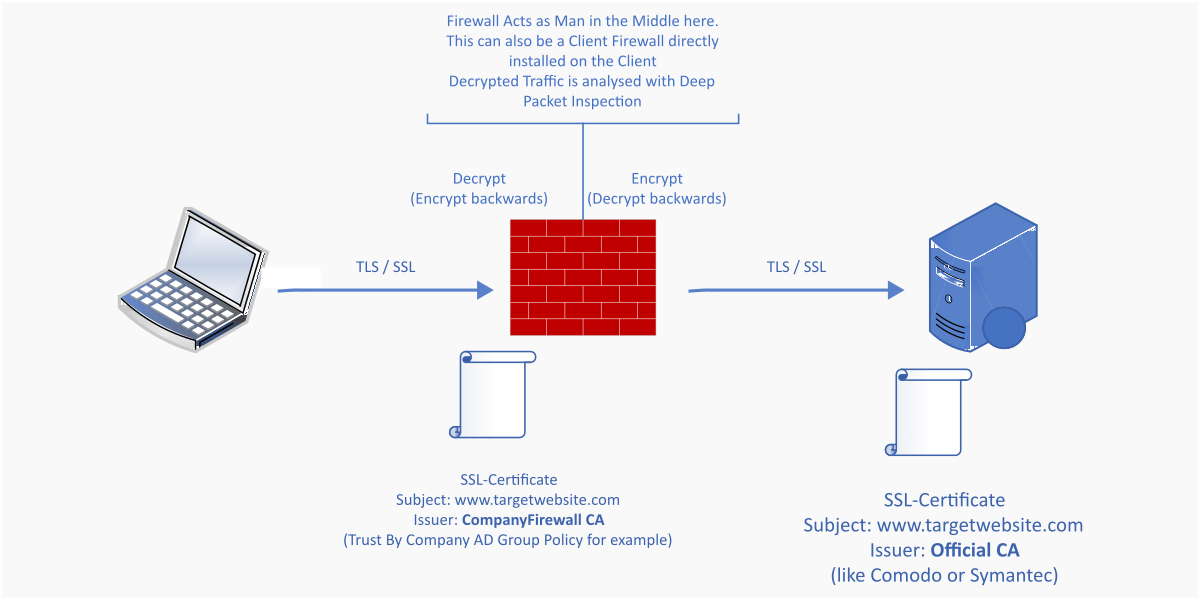
SSL inspection is the process of intercepting encrypted SSL/TLS traffic, decrypting it to inspect the content, then re-encrypting and forwarding the traffic to the intended recipient. It gives security tools visibility into encrypted connections to detect and block threats like malware, data exfiltration, command, and control communications, and more.
By peering into encrypted traffic, SSL inspection can provide:
- Threat prevention: Identify and block malware, viruses, ransomware, or command-and-control activity trying to hide in SSL connections. Prevent attacks from reaching users.
- Data loss prevention: Detect and filter sensitive information being transmitted over secure protocols and channels. This helps comply with regulations.
- URL/content filtering: Block access to websites, applications, or content deemed inappropriate or unproductive. Enforce acceptable use policies.
- Compliance enforcement: Meet regulatory requirements for inspection and logging of encrypted traffic. Support audits and investigations.
- User awareness: Provide visibility into how the network is being used. Identify high-risk employees through their browsing patterns.
Without decrypting and inspecting SSL traffic, organizations face blind spots that threats can exploit using encryption to bypass defenses. SSL inspection removes that advantage.
Key Takeaways
- SSL inspection allows organizations to decrypt and inspect encrypted SSL/TLS traffic for threats, data loss, compliance violations, etc. It works by installing a trusted SSL certificate on users’ devices and acting as a man-in-the-middle to decrypt and re-encrypt traffic.
- SSL inspection enables visibility into encrypted traffic and protection against threats hidden in SSL/TLS connections. However, if not implemented correctly, it can raise security, privacy, and legal concerns.
- To use SSL inspection, organizations need to install a trusted certificate authority on endpoints and route SSL traffic through a proxy or firewall that can decrypt, inspect, and re-encrypt the traffic before sending it to the destination server.
- Deploying SSL inspection requires planning to distribute root certificates, handle certificate warnings, exclude trusted traffic, and comply with privacy regulations. Limiting inspection to high-risk traffic helps address potential drawbacks.
- Next-generation firewalls and secure web gateways often include SSL inspection capabilities. Organizations can also use dedicated SSL inspection appliances or services for comprehensive coverage across all ports and protocols.
How Does SSL Inspection Work?
SSL inspection works by intercepting traffic at the network perimeter and establishing a man-in-the-middle architecture to decrypt, inspect, and re-encrypt packets before forwarding them to their destination.
- Install root certificate: The organization pushes out a trusted root certificate from the inspection device to endpoint devices on the network.
- Traffic interception: A proxy or firewall intercepts outbound SSL connections and terminates them. The server certificate is replaced with an inspection certificate.
- Decryption: Using the inspection certificate and private key, the inspection device decrypts the traffic.
- Inspection: With the traffic decrypted, security tools scan for threats, filter content, log activity, etc.
- Re-encryption: After inspection, the proxy re-encrypts the traffic with a certificate signed by the root certificate that was installed on the endpoint.
- Forward to destination: The connection is forwarded to the original destination server.
This allows the inspection device to decrypt and read the plaintext content for inspection while still maintaining end-to-end encryption between the client and server.
Traffic can be decrypted and inspected in one direction (outbound from clients) or bidirectionally to inspect inbound server responses.
Where Does SSL Inspection Take Place?
SSL inspection is typically implemented by routing traffic through a proxy, next-generation firewall, secure web gateway, or dedicated SSL inspection appliance deployed at network egress points.
Common deployment locations include:
- Network perimeter: Inspect all outbound traffic heading to the internet to gain visibility into communications leaving the network.
- Internal segments: Inspect traffic within or between trusted zones inside the network, such as between departments.
- Remote locations: Inspect traffic from remote offices, retail stores, or other places.
- Mobile endpoints: Inspect mobile and BYOD traffic by routing it through proxies.
The inspected traffic can originate directly from user devices or internal servers accessing external websites and services.
SSL Inspection Use Cases
Here are some examples of how organizations commonly use SSL inspection:
- Financial firms inspect SSL traffic to prevent data loss of sensitive customer information such as social security numbers, bank account details, and credit card numbers.
- Healthcare providers inspect encrypted traffic to help enforce HIPAA compliance by preventing leakage of patient health records.
- Retailers implement SSL inspection to filter access to inappropriate websites and detect attackers trying to exfiltrate customer credit card data with malware.
- Educational institutions decrypt SSL connections to block students from accessing non-educational sites and detect threats targeting their networks.
- Government agencies inspect encrypted traffic to detect threats, meet regulatory requirements, and monitor employees accessing unauthorized services.
- Manufacturers inspect SSL to prevent LOSS of intellectual property, such as proprietary design documents, from being leaked to competitors.
- SMBs use inspection to get visibility into SSL-based threats and control employee internet use with granular policies.
Pros and Cons of SSL Inspection
While SSL inspection provides significant security and oversight benefits, it also introduces potential drawbacks around trust, privacy, performance, and legal compliance.
Benefits of SSL Inspection
- Enhanced threat protection: Inspecting SSL encrypted traffic for malware, viruses, command and control activity, data exfiltration, and more reduces the attack surface.
- URL/content filtering: Decrypting SSL allows granular filtering of websites, applications, and content to enforce acceptable use policies.
- Data loss prevention: Detecting sensitive data being exfiltrated over encrypted tunnels helps prevent breaches and comply with regulations.
- User oversight: Tracking web activity provides visibility into high-risk users and insider threats. Supports forensics.
- Compliance: Meeting regulatory requirements for inspecting and logging encrypted traffic avoids fines and sanctions.
- Troubleshooting: Decrypting SSL makes it easier to detect and troubleshoot network issues impacting encrypted traffic.
Potential Drawbacks
- Certificate warnings: Root certificate installation triggers warnings that trained users to ignore, making them more vulnerable to man-in-the-middle attacks.
- Performance impact: Inspecting all SSL traffic reduces network speeds and increases latency due to decryption/re-encryption.
- Encryption overhead: The extra encryption steps increase processor and memory utilization on inspection devices.
- Legal compliance: Does not comply with regulations prohibiting inspection of specific traffic in some regions unless excluded.
- User distrust: Employees may feel their personal information and privacy are being invaded if inspection is not disclosed or scoped correctly.
- Security risks: Improper deployment can open the door for attackers to intercept sensitive communications if encryption keys are compromised.
How to Implement SSL Inspection
Deploying SSL inspection across an enterprise requires careful planning and configuration to maximize security while minimizing drawbacks.
Selecting an SSL Inspection Solution
Purpose-built SSL inspection appliances provide out-of-the-box capabilities but can be expensive and lack flexibility.
Network security devices like next-generation firewalls and secure web gateways integrate inspection functions alongside other security protections. This consolidated approach simplifies management but may require tradeoffs.
Proxy servers can be configured to inspect SSL traffic but add latency and complexity. Proxies may not support advanced threat detection of complete firewalls.
Once a solution is selected, the following steps involve planning the deployment.
Install a Trusted Certificate Authority
The inspection device generates its own root CA certificate, which must be installed on endpoint devices to avoid SSL certificate warnings.
For managed devices, the root certificate can be pushed out via the corporate PKI infrastructure, MDM/EMM platforms, or GPO scripts.
Installing on BYOD or home systems is more challenging. Options include emailing the certificate for user installation, directing users to download it through an internal portal, or installing it if devices connect via VPN or by visiting a provisioning site.
Certificate acceptance should be coupled with a user education campaign around the purpose of inspection.
Configure Inspection Rules
Specify which traffic to decrypt using a default-deny approach:
- Only decrypt high-risk traffic: Limiting inspection to unknown sites, questionable categories, high-bandwidth streams, etc., reduces performance impact and privacy concerns. Exceptions can be made for trusted sites.
- Decrypt application traffic: Specify applications like social media, webmail, or FTP for inspection to enforce policies.
- Control by user group: Adjust decryption rules based on user risk level, role, and privileges.
- Exclude trusted traffic: Avoid decrypting critical services like banking, healthcare, and government sites to maintain performance and comply with regulations.
- Drop unnecessary traffic: Discard traffic immediately after inspecting rather than re-encrypting to reduce overhead.
Distribute Computational Load
SSL decryption is CPU intensive. Distributing them across multiple firewalls or appliances prevents bottlenecks.
Load balancers can be used to scale inspection and distribute traffic across devices. Parallel processing on GPUs and hardware encryption acceleration help improve performance.
Handle Traffic Inspection
With rules in place, configure connected security devices to perform scanning, filtering, and malware analysis of the decrypted traffic as per the organization’s policies.
Logging of inspection data also needs to comply with data privacy regulations in applicable jurisdictions.
Troubleshoot and Optimize
Monitor CPU usage on the inspection device during initial deployment and adjust rules to minimize overhead.
Verify inspection blocking through reports or alerts of dropped traffic and fine-tune rules to reduce false positives.
Test security oversight to ensure traffic is no longer invisible and compliance requirements are being met.
SSL Inspection Best Practices
Following best practices helps balance the benefits of SSL inspection against potential drawbacks:
- Limit inspection only to high-risk traffic, when possible, to reduce visibility into employee activities.
- Exempt traffic to trusted sites like banking, healthcare, and government to maintain performance and comply with laws.
- Disclose and educate employees about SSL inspection to maintain transparency and trust. Clarify it does not intercept all of their web activity.
- Use a firewall rule rather than a web proxy to inspect traffic to avoid increased latency.
- Distribute load across multiple devices to handle the performance impact of decryption.
- Strictly limit access to decrypted data to maintain security. Digitally sign logs to ensure integrity.
- Consult legal counsel to ensure inspection practices adhere to privacy laws and regulations.
- Continuously patch and update SSL inspection devices to prevent compromise of certificate keys.
- Automate issuance and rotation of short-lived inspection certificates to minimize risks.
Summary
SSL inspection enables organizations to decrypt and peer into encrypted traffic to block threats, enforce policies, and meet compliance requirements. However, it also introduces overheads and risks if not carefully deployed. Limiting inspection to high-risk traffic, distributing load, exempting trusted sites, and securing private keys helps balance the tradeoffs. When appropriately implemented, SSL inspection can remove blind spots and provide oversight without excessively impacting users or network performance. In the future, encryption will continue increasing, making inspection an essential component of enterprise security stacks.
Frequently Asked Questions About SSL Inspection
What is the difference between SSL inspection and TLS inspection?
SSL inspection and TLS inspection refer to the same process of decrypting encrypted traffic, just with different versions of the encryption protocol. SSL is the older Secure Sockets Layer protocol. TLS, or Transport Layer Security, is the newer updated standard. The terms SSL inspection and TLS inspection are often used interchangeably since the decryption process is identical.
Does SSL inspection allow spying on users?
SSL inspection raises concerns about user privacy since it involves actively intercepting and decrypting secure traffic. However, inspection does not necessarily mean all user activity is tracked. Organizations should limit inspection only to high-risk traffic, which is required to enforce security policies. Disclosing the use of SSL inspection and precisely what is being monitored helps maintain user trust.
Can users bypass SSL inspection?
SSL inspection relies on users trusting the certificate authority of the inspection device. Savvy users could manually install their trusted certificates on their devices or avoid routes and ports that are inspected. Organizations can mitigate bypassing by routing all traffic through proxies, blocking alternate protocols, and monitoring for unscanned traffic.
Does SSL inspection impact network performance?
SSL inspection can degrade network performance since it adds processing overhead for decryption/encryption, especially when decrypting all traffic. Limiting inspection scope, distributing load, and hardware acceleration helps minimize impact. Latency is increased but can be mitigated by routing through firewalls instead of proxies.
Is SSL inspection legal?
The legality of SSL inspection depends on local laws. Broad inspection of all traffic may violate privacy rights in some regions. Organizations should consult legal counsel to ensure inspection complies with regulations like GDPR. Limiting inspection to high-risk traffic and excluding protected categories helps maintain compliance.
Can SSL inspection detect threats in HTTPS traffic?
Yes, decrypting HTTPS traffic allows devices to detect malware, command and control activity, data exfiltration, and other threats hiding within encrypted connections. This prevents attackers from bypassing security through encryption. Inspection should be used alongside other protections like next-gen AV, IPS, and sandboxing.
What SSL inspection solutions are available?
Next-generation firewalls and secure web gateways from top vendors include integrated SSL inspection capabilities. There are also dedicated SSL inspection appliances and services available, offering advanced decryption options. Some proxy servers also support inspecting SSL traffic after configuration.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.