Understanding Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping. These flaws allow attackers to execute scripts in the victim’s browser, which can hijack user sessions, deface websites, insert hostile content, conduct phishing attacks, and take over the user’s browser.
Key Takeaways
- XSS flaws allow attackers to inject malicious scripts into web pages viewed by other users.
- There are three main types of XSS: reflected, stored, and DOM-based XSS.
- Reflected XSS involves injecting scripts into URLs that are reflected back in the application’s response.
- Stored XSS is more dangerous as the injected script is permanently stored on the target server.
- DOM-based XSS exploits the DOM environment rather than the server.
- Typical XSS attacks include session hijacking, defacing websites, phishing, and malware injection.
- To prevent XSS, developers should escape untrusted data, enable CSRF protection, implement a Content Security Policy, and sanitize user inputs.
- Detection methods involve manual code review, automated scanners, runtime protections, and monitoring production traffic.
What is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a code injection attack that allows an attacker to execute malicious JavaScript in another user’s browser. XSS vulnerabilities enable attackers to bypass access controls and impersonate users. According to OWASP, XSS flaws are amongst the top ten web application security risks.
XSS attacks exploit the browser’s trust in content received from web servers. When a user visits a website, the browser trusts that the server will not deliver malicious code. However, if the website has an XSS vulnerability, an attacker can craft malicious scripts and inject them into otherwise benign and trusted web pages. The end user’s browser has no way to know that the script should not be trusted and will execute the script because it came from a trusted source.
XSS attacks target web applications that generate pages dynamically. For example, if a site allows users to submit comments that are displayed on another page, an attacker could submit a comment with malicious JavaScript. When other users visit the page, the script will execute in their browsers with the same permissions as the vulnerable website.
There are three main types of cross-site scripting:
- Reflected XSS: The malicious script is injected into another webpage via a malicious link. Users are tricked into clicking the link and executing the script in their own browser.
- Stored XSS: The malicious script is permanently stored on the target server, such as in a database or forum. The script executes whenever normal users later load the affected page.
- DOM-based XSS: The vulnerability exists in client-side code rather than server-side. The malicious script is executed as a result of modifying the DOM environment in the victim’s browser.
How Does Cross-Site Scripting Work?
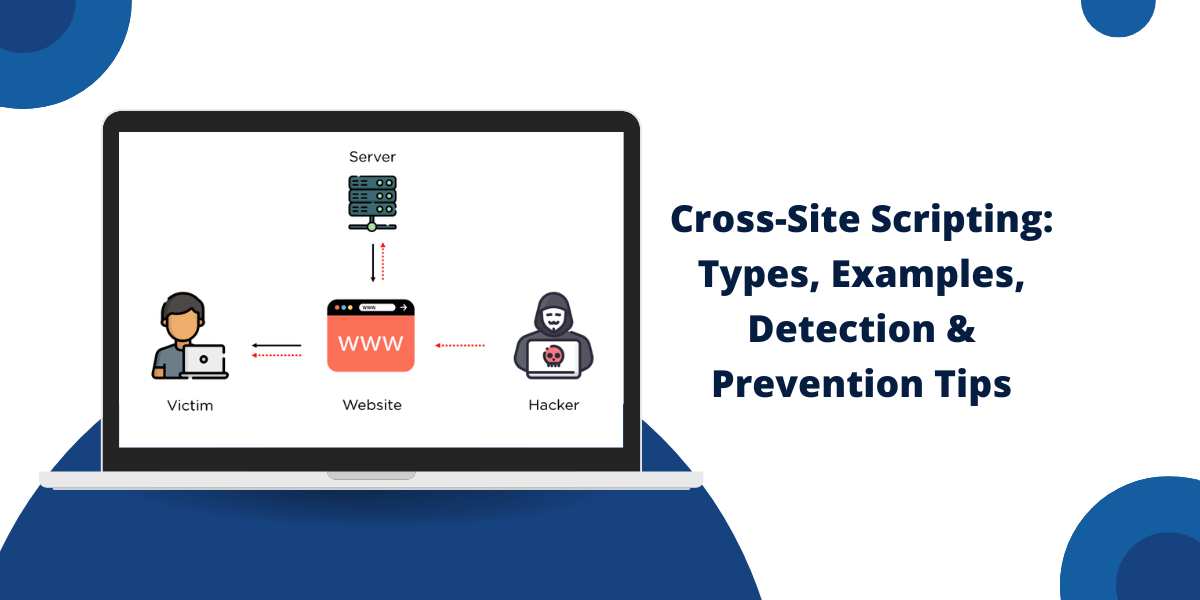
Cross-site scripting works by manipulating the DOM environment of the victim’s browser to execute malicious scripts. The attack involves three parties:
The Victim
The victim is the end user targeted by the XSS attack. They visit a trusted but vulnerable website that does not properly validate or encode user-contributed data.
The Website
The vulnerable website unintentionally assists in the attack by reflecting malicious scripts from the attacker back to the victim’s browser. Alternatively, the site permanently stores the malicious script, which is later retrieved by the victim’s browser.
The Attacker
The attacker discovers an XSS vulnerability on the target website. They then craft a malicious script and inject it into the website for execution by the victim’s browser.
When the victim visits the vulnerable page, the malicious script will execute in their browser with the same access privileges as the vulnerable website. The script can transmit session cookies, tokens, or other sensitive information back to the attacker. It can also rewrite the vulnerable page’s HTML to trick the user.
XSS Attack Examples
Some examples of how XSS vulnerabilities can be leveraged include:
- Session hijacking: The script steals the victim’s session cookie and allows the attacker to impersonate the user.
- Defacing the website: The injected script can rewrite the vulnerable page’s HTML and insert offensive images, content, etc.
- Phishing: The script creates fake login pages or password prompts to steal the victim’s credentials.
- Malware injection: The script could invoke malware downloads onto the victim’s computer for further exploitation.
- Browser exploitation: Advanced attackers can sometimes leverage XSS to exploit vulnerabilities in the browser itself and gain additional privileges.
Types of Cross-Site Scripting
There are three primary types of XSS attacks:
Reflected XSS
Reflected XSS involves injecting malicious scripts into the victim’s web requests. The term “reflected” refers to the script being bounced off the web server and executed by the victim’s browser.
In a reflected XSS attack, the attacker crafts a malicious URL and tricks the victim into clicking it. The URL contains malicious code as part of the request parameters. When the vulnerable website displays the URL back to the victim, it unwittingly includes the malicious script, which then executes in the victim’s browser.
For example, a URL may contain code like:
http://vulnerablesite.com/search.php?q=<script>/* malicious code */</script>
When the victim visits this link, the search page will reflect the script back as part of the response. The victim’s browser will then execute it in the context of the vulnerable site.
Stored XSS
Stored XSS (also called persistent XSS) is more devastating than reflected XSS. With stored XSS, the malicious script is permanently stored on the vulnerable server, usually in a database. The script then executes whenever normal users later load the affected page.
For example, an online forum that allows users to submit comments may be vulnerable to stored XSS. An attacker can submit a comment containing malicious JavaScript code. Then, whenever any user views that comment thread, the script will execute in their browser. Since the script is saved on the server, the attack can persist and affect many more victims.
Stored XSS vulnerabilities often occur when user-contributed data is improperly sanitized. Dangerous characters like < and > should be escaped prior to outputting data back to the browser.
DOM-Based XSS
DOM-based XSS stems from JavaScript code and operations that directly manipulate the DOM environment rather than relying on the server. The vulnerability exists in client-side code instead of server-side.
For example, if a JavaScript function takes user input and uses it to dynamically generate HTML on the client-side, an attacker could submit malicious code to inject their own HTML and scripts. Since this code runs solely on the client-side, a vulnerable website may have difficulty detecting and preventing it.
DOM-based XSS can be more challenging to detect and prevent compared to reflected or stored XSS flaws. Typical security defenses like input validation and output encoding on servers are ineffective against DOM-based XSS originating from the client side.
Real-World XSS Examples
Some notable examples of XSS attacks against major websites include:
- MySpace Samy worm (2005): Samy Kamkar discovered a stored XSS vulnerability and created a worm that infected over 1 million MySpace profiles by automatically making Samy a “friend.” Each infected profile then spread the worm further.
- Hackers use XSS on Hotmail and Gmail (2006): A stored XSS flaw on Microsoft’s Soapbox site enabled attackers to hijack Hotmail and Gmail accounts by stealing session cookies.
- Stuxnet (2009): This cyberweapon against Iranian nuclear facilities exploited multiple zero-day flaws, including an IE6 XSS vulnerability.
- XSS worm hits Facebook (2011): A young hacker created an XSS worm that infected hundreds of thousands Facebook users by spreading a malicious link.
- Persistent XSS to Remote Code Execution on Twitter (2014): Attackers leveraged a DOM-based XSS to eventually achieve remote code execution on twitter.com servers.
- XSS in YouTube (2018): Stored XSS vulnerabilities in YouTube enabled comments to inject malicious code into video pages.
How to Prevent XSS Attacks
Here are some key methods to prevent cross-site scripting vulnerabilities:
Validate and Escape Untrusted Data
Scrutinize any untrusted data before outputting it to the browser. Use whitelist validation to only allow safe characters and blacklist filtering to detect dangerous characters like < and >. Encode special characters using escaping functions applicable to your platform.
Enable CSRF Protection
Enable cross-site request forgery (CSRF) protections. CSRF tokens can prevent forged requests and protect forms from submitting malicious input.
Implement a Content Security Policy
Implementing a Content Security Policy (CSP) can minimize XSS risks by whitelisting trusted sources of content and scripts. This will block untrusted scripts from executing.
Sanitize User Input
Aggressively sanitize all user inputs on both the client side and server side. Strip out any HTML tags, JavaScript code, and other unnecessary characters from data submitted by users.
Disable Inline Code Execution
Disable any features that dynamically execute user-supplied scripts or code snippets. Only allow execution of scripts from trusted and controlled sources.
Use Appropriate HTTP Headers
Set the X-XSS-Protection and X-Content-Type-Options headers to prevent plugins from running unauthorized content.
How to Detect XSS Vulnerabilities
Some useful methods to detect XSS flaws include:
Manual Code Review
Manually review all points in the code where untrusted data enters the application. Verify that proper validation and encoding occur before data reaches the browser.
Automated Scanners
Use black box and grey box scanners to crawl sites for reflected and stored XSS vulnerabilities. This scales better than a purely manual review.
Runtime Protections
Enable runtime services like Web Application Firewalls (WAFs) to monitor and block real attacks against production traffic. WAF rules can detect attack payloads and known XSS patterns.
Monitor Production Traffic
Analyze production logs and audit trails to detect attempted XSS attacks, such as suspicious requests containing <script> tags and other common vectors.
Bug Bounty Programs
Bug bounties incentivize external security researchers to find flaws like XSS. Large programs often discover issues that are missed in internal reviews.
Final Thoughts
XSS flaws remain highly prevalent and dangerous vulnerabilities in modern web applications. Attackers can exploit XSS to hijack user sessions, deface websites, steal sensitive data, and distribute malware. This highlights the importance of secure coding practices and proactive monitoring to detect and mitigate XSS risks.
Developers should assume all user-contributed data is untrusted and properly validate, sanitize, and escape it before display. With precautions and continuous testing, organizations can avoid damaging XSS incidents against their web applications.
Frequently Asked Questions
What is the difference between XSS and CSRF?
XSS involves injecting malicious scripts into web pages viewed by victims. CSRF tricks victims into submitting forged requests to websites where they’re already authenticated.
What’s the difference between stored and reflected XSS?
Reflected XSS bounces the malicious script off the server to attack victims. Stored XSS permanently embeds the script in website content and databases.
Can XSS vulnerabilities lead to remote code execution?
In some cases, XSS flaws can be chained with other exploits to ultimately achieve arbitrary remote code execution on the server.
Is XSS a client-side or server-side vulnerability?
XSS generally originates from server-side weaknesses but exploits the client by targeting browsers. However, DOM-based XSS is specific to client-side JavaScript code.
What are common locations for XSS vulnerabilities?
Reflected XSS often appears in search forms, URL parameters, etc. Stored XSS occurs in databases, comment systems, CMS apps, and anywhere user-supplied data is displayed.
How can I prevent XSS as a developer?
Key prevention measures include validating untrusted data, escaping special characters, enabling CSRF tokens, implementing CSP, sanitizing user input, disabling inline code execution, and using appropriate security headers.
What are examples of XSS attack payloads?
Common XSS attack vectors include embedding <script>, <img>, <iframe>, and other tags that allow script injection and arbitrary HTML/CSS.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.