What are Application Security Tools?
Application Security Tools are software programs that protect applications from cyber threats and vulnerabilities. These tools scan code, monitor systems, and identify security risks in software applications. Security teams use these tools to find and fix weaknesses before attackers can exploit them. Common features include vulnerability scanning, penetration testing, and code analysis.
The tools work during development and after deployment to maintain application safety. They detect issues like SQL injection, cross-site scripting, and authentication problems. Modern security tools also provide automated testing, real-time monitoring, and compliance checking to keep applications secure throughout their lifecycle.
What are the Main Purposes of Application Security Tools
- Identifying vulnerabilities: Discover security flaws in code, like injection attacks, authentication bypasses, and misconfigurations.
- Prioritizing remediation: Understand the risk level associated with findings to focus on high-priority fixes first.
- Verification testing: Confirm vulnerabilities have been successfully resolved after remediation efforts.
- Reporting: Provide reports to demonstrate overall app security posture and compliance with policies or regulations.
- Protection: Actively protect against attacks targeting known weaknesses in real time.
Using the right app security testing tools during development can significantly reduce costs compared to fixing vulnerabilities post-deployment. Building security into the software development lifecycle (SDLC) is essential for minimizing risk.
Types of Application Security Tools
There are several types of application security tools, each using different methods for analyzing source code, binaries, and running applications:
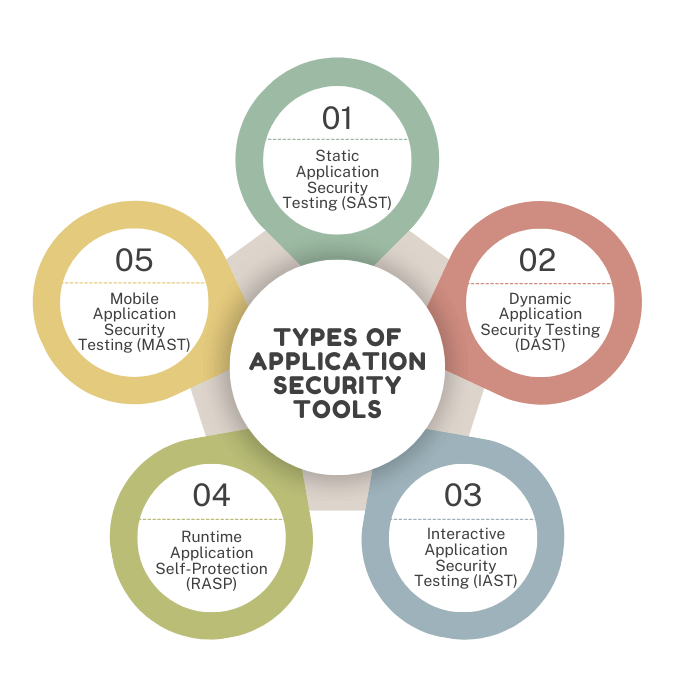
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Interactive Application Security Testing (IAST)
- Runtime Application Self-Protection (RASP)
- Mobile Application Security Testing (MAST)
Static Application Security Testing (SAST)
SAST tools scan application source code or binaries for security issues without executing the code itself. This allows SAST to find vulnerabilities that could lead to exploits like buffer overflows, SQL injection, and cross-site scripting.
The benefits of static testing include finding risks early in development, broad vulnerability coverage, and no impact on runtime performance. The limitations are that SAST cannot detect issues dependent on data or application state.
Dynamic Application Security Testing (DAST)
DAST analyzes applications while they are running, typically using crawling and fuzzing techniques. This enables the detection of vulnerabilities like authentication problems, access control issues, and API abuses. Well-known platforms such as Pentest-Tools.com highlight how combining DAST with contextual vulnerability analysis helps teams prioritize real-world risks rather than treating all findings equally.
DAST’s benefits include finding logic flaws and risks that require applications to be running. Drawbacks include limited coverage and potential impact on performance.
Interactive Application Security Testing (IAST)
IAST instruments and monitors code while applications execute to combine the strengths of static and dynamic testing. IAST can verify exploitable risks uncovered by SAST scanners and find logic flaws missed by static analysis.
The benefits include exploiting vulnerabilities to confirm risk, minimizing performance impact, and comprehensive coverage. The main downside is the complexity associated with instrumentation.
Runtime Application Self-Protection (RASP)
RASP uses embedded sensors within running applications to detect and block attacks targeting known vulnerabilities in real time. This provides active protection against injection attacks, data leakage, and account takeovers.
The benefits of RASP include real-time threat protection and easy integration. The drawbacks focus on limited coverage and the potential for false positives.
Mobile Application Security Testing (MAST)
MAST tools specialized for analyzing mobile apps can find risks across networks, platforms, and data layers. This includes weaknesses in communication protocols, client-side code, and back-end APIs.
The benefits of mobile app testing include identifying device: and connectivity-specific flaws. Limitations center around limited coverage of hybrid and native app technologies.
Key Factors for Choosing Application Security Tools
With different types of app sec tools available, focus on these key considerations when evaluating options:
- Vulnerability coverage: The breadth of weaknesses the tool can identify should align with your specific risk environment.
- Accuracy: Balancing high detection rates with low false positives optimizes remediation workflows.
- Integration: Choose tools that integrate with your development infrastructure and workflows.
- Automation: Automated scanning, reporting, and testing increase efficiency over manual processes.
- Support: Vendor provided technical support and access to vulnerability databases are important.
- On-premise vs. SaaS: On-premise offers customization, while SaaS reduces infrastructure demands.
- Budget: Application security tools range from free open-source to expensive enterprise-scale platforms.
Prioritizing your unique needs and environment will help determine the right solutions or combination of app sec tool categories.
Why Application Security Tools Are Crucial
Here are some key reasons why utilizing application security tools should be a priority:
- Prevent data breaches: Application vulnerabilities are directly tied to data compromise and loss. Appsec tools find weaknesses that, if left undetected, can lead to exploitation.
- Meet compliance requirements: Many regulations and standards like PCI DSS explicitly require application security testing.
- Reduce costs: Fixing vulnerabilities during development is significantly cheaper than post-deployment remediation. Automated tools scale efficiently across large applications.
- Improve quality: Discovering flaws early improves overall application robustness and reliability for end users.
- Protect reputation: App sec protects customer trust and brand reputation by preventing high-profile breaches.
- Promote DevSecOps: App sec tool integration creates shared responsibility between developers and security teams.
Integrating Application Security into Development
For maximum impact, organizations should focus on integrating application security testing throughout the software development life cycle. Key steps include:
- Training developers on secure coding practices to build more resilient apps from the start.
- Using SAST during coding to identify and remediate vulnerabilities in real time.
- Performing DAST against staging environments to detect issues before deployment.
- Utilizing IAST on CI/CD pipelines to validate production-safe builds.
- Employing RASP for runtime monitoring and threat detection post-release.
Shifting application security left in the development process drastically reduces costs and risk exposure over relying solely on post-deployment testing.
Final Thoughts
Application security tools play a critical role in protecting valuable software assets and user data from constantly evolving threats. By understanding the different categories and top solutions, organizations can craft an effective application security program integrated into the SDLC.
Choosing the right tools involves analyzing your budget, risk tolerance, development workflows, and compliance needs. Utilizing a combination of SAST, DAST, IAST, RASP, and MAST maximizes coverage across the entire application lifecycle.
With application security threats continuing to rise, automated app security tools for vulnerability detection, prevention, and runtime protection provide a key line of defense. Integrating security into development from the start results in higher-quality, resilient applications at reduced cost.
Frequently Asked Questions (FAQ) About Application Security Tools
When should you implement application security testing?
Implementing application security as early as possible in the software development lifecycle (SDLC) provides the greatest benefit. Static and dynamic application testing should be used from initial coding through integration, testing, and deployment stages.
What app sec tools can developers use directly?
Developers can utilize static application security testing (SAST) solutions integrated into IDEs and build tools to scan code as they write it. This provides fast feedback to fix vulnerabilities without slowing down development.
Are open-source application security tools as effective as commercial ones?
Yes, many open-source application security tools, such as OWASP ZAP and dependency checkers, offer comparable functionality to their commercial counterparts. The trade-off is typically less extensive feature sets and a lack of professional vendor support.
How do you choose between on-premise or SaaS application security tools?
On-premise application security tools allow for customization and integration with internal infrastructure but require dedicated resources to deploy and manage. SaaS options remove infrastructure burdens at the cost of relying on the vendor’s cloud and giving up some control.
What mobile application security testing tools should be used?
Leading options for mobile app sec testing include Micro Focus Fortify on Demand, NowSecure Lab Automated, and QA Wolf. Evaluate tools against coverage for iOS, Android, hybrid, web, and back-end APIs.
Can application security tools completely prevent successful attacks?
No solution can offer 100% protection against sophisticated threats. Application security tools significantly reduce risk and enable rapid response, but they should be used alongside robust monitoring, defense-in-depth protections, and an incident response plan.
How can you maximize the accuracy of application security tools?
Combining static, dynamic, and interactive analysis provides the most accurate results by minimizing false positives. Tuning tools specifically for your tech stack and only flagging high-probability threats also improves the signal-to-noise ratio.
What compliance standards require the use of application security tools?
Major regulations like PCI DSS, HIPAA, and GDPR explicitly require application security testing. Standards like OWASP and NIST also provide prescriptive guidance on utilizing different types of app security tools.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.