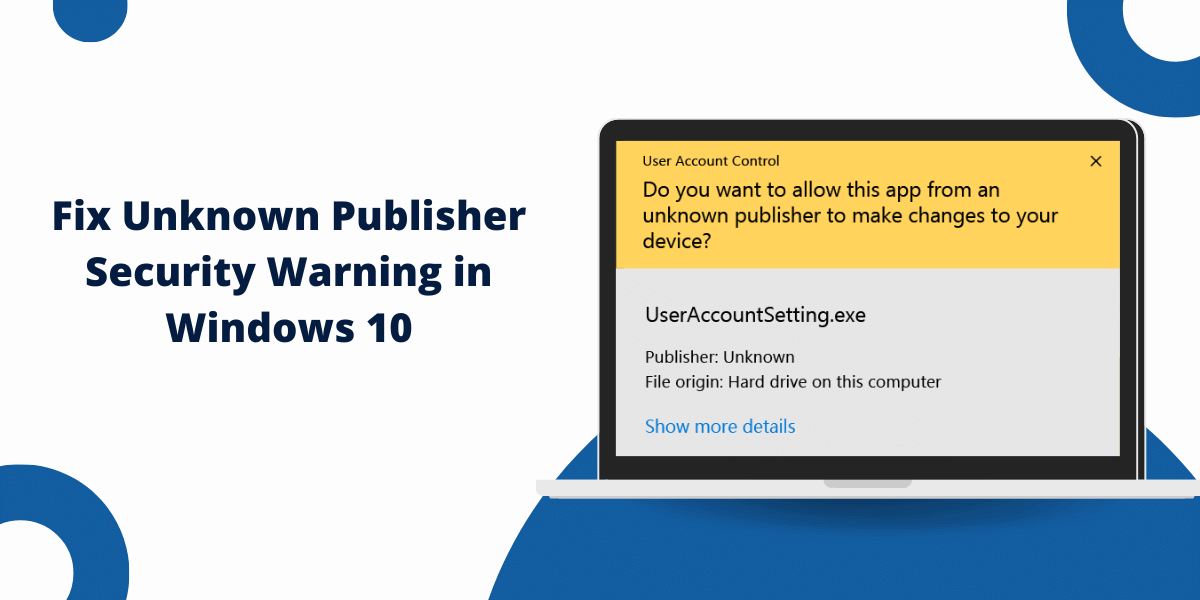
A Step-by-Step Guide to Use Code Signing in MacOS
Code signing is an important security practice for MacOS applications and software that verifies the identity of developers and ensures code integrity. It helps prevent tampered or malicious software from running on a user’s system. This comprehensive guide will explain what code signing is, why it’s important, how it works in MacOS, and provide step-by-step instructions on how developers can code sign their software.
Key Takeaways
- Code signing verifies the identity of developers and checks that code has not been altered or corrupted.
- All software on the Mac App Store must be code-signed, and the Gatekeeper requires a signature for apps from outside the store.
- Developers sign their code by obtaining certificates from Apple or trusted third parties and using code signing tools.
- Users can check an app’s code signature before running it by checking its context menu or using Utilities.
- Code signing improves security, establishes trust between devs and users, and ensures the smooth running of apps in MacOS.
Basic Overview of Code Signing
Code signing refers to the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. The signature is created using the private key of a digital certificate.
Code signing provides two main assurances:
- Authenticity: It establishes the identity of the software publisher/author and proves that the app came from the developer and has not been tampered with.
- Integrity: Any changes to the signed code will invalidate the signature, which alerts users that the code should not be trusted. This prevents malicious software from running.
On MacOS, code signing is an important security practice followed by all major developers. Apple requires all apps submitted to the Mac App Store to be signed. MacOS also enforces mandatory code signing for certain scripts and binaries through its Gatekeeper security feature.
How Code Signing Works in MacOS
Here is an overview of how code signing is implemented and verified in MacOS:
Signing the Code
- Developers first obtain a signing certificate (also called code signing certificate) from Apple or trusted third-party Certificate Authorities like DigiCert.
- The certificate contains the developer’s public-private key pair and acts as their digital identity.
- The code is signed using the private key by running tools like codesign, which generates a cryptographic hash of the code and embeds the signature.
- The signature is stored within the app bundle or binary.
Verifying the Signature
- When a user launches the signed app, MacOS checks the code’s signature to verify its authenticity and integrity.
- It uses the developer’s public key (from their certificate) to decrypt the hash and compares it with a freshly computed hash of the same code.
- If the hashes match, the signature is valid, and the app is allowed to run. Else, MacOS blocks the app.
- MacOS includes built-in mechanisms like Gatekeeper that enforce signature checks for downloaded apps and other unsigned code attempting to run.
Chain of Trust
- Certificates are issued by Certificate Authorities (CAs), which form a chain of trust.
- MacOS has a store of trusted root certificates from authorities like Apple and trusted third parties.
- Any certificate issued by these trusted CAs is automatically verified by MacOS, establishing the developer’s identity.
This system of cryptographic signing and verification helps maintain the integrity of the MacOS ecosystem.
How to Obtain a Code Signing Certificate for Signing Mac Apps
Developers have to obtain the appropriate code signing certificate from Apple or a trusted third-party Certificate Authority to sign their Mac apps and binaries. Here are the options:
Apple Certificates
Apple provides two main types of code signing certificates:
- Developer ID Certificate: Used to sign apps distributed outside the Mac App Store. Apps signed with this can be gatekeeper approved.
- Mac App Distribution Certificate: Required for submitting apps to the Mac App Store. Apple re-signs apps.
These certificates can only be obtained by joining the Apple Developer Program, which costs $99 per year. You can manage them using XCode or the Apple Developer Portal.
Third-Party Certificates
Developers can also get code signing certificates from trusted CAs like DigiCert, Comodo, etc.
Advantages include:
- There is no need to enroll in the Apple Developer Program
- Flexible options like code signing for Windows apps or hardware devices.
- Cheaper than Apple certificates in many cases
The disadvantage is that these apps may need to get gatekeeper approval and could prompt warnings on MacOS.
Research and choose a reputable third-party CA that provides purpose-built code signing certificates.
Code Signing Tools for macOS
Once developers have obtained the appropriate code signing certificate, they can sign their apps and binaries using MacOS tools:
Xcode
Xcode provides an easy way for app developers to code-sign apps. On Xcode, go to Project Settings > Signing & Capabilities to select the certificate, Provisioning Profile, etc. Xcode will automatically sign the app before archiving or distribution.
command-line tools
Apple provides a codesign command line tool that can be used to manually sign apps, binaries, scripts, plugins, and more.
Some examples of using codesign:
# Sign an application
codesign -s "Developer ID" /path/to/MyApp.app
# Sign a binary
codesign -fs "John Doe" /path/to/binary
# Sign a plugin
codesign -s "Developer ID" /path/to/plugin.bundle
The -s flag specifies the name or identifier of the code signing certificate. With additional flags, we can also verify signatures, display detailed certificate information, and more.
Specialized tools like product signs are also available to sign installer packages.
Other Tools
Some third-party tools and IDEs, like JetBrains AppCode, provide GUIs and additional options for signing MacOS binaries and apps.
For command-line-averse developers, these tools can help simplify and streamline the code signing process.
How to Check Signature on Apps
MacOS provides simple ways for users to check the code signature on any app before running it:
Finder Context Menu
Right-click on the app in Finder and select ‘Get Info.’ Expand the “General” section. If the app is signed, signature details will be displayed here:
![App Context Menu Signature Check][]
Gatekeeper Interface
Trying to launch unsigned or modified apps will trigger the Gatekeeper prompt. It displays the app verification status and signature details
![Gatekeeper Signature Check][]
Certificate Tool
The Certificate Tool utility provides advanced certificate info. Launch it and drag and drop the app icon onto it. The signature(s) on the app will be displayed.
![Certificate Tool][]
These options let users verify the code signing status before running any new apps on their MacOS devices.
Gatekeeper and Code Signing
Gatekeeper is the MacOS security feature that enforces code signing by blocking unsigned apps or binaries from running or altering critical files or settings.
Some examples of Gatekeeper’s code signing requirements:
- Apps downloaded from outside the Mac App Store must be signed by a Developer ID
- Kernel extensions and drivers require a Developer ID signature
- Apps that want full disk access must be signed
- Scripts and binaries that are launched via sudo must be signed
- Automator workflows that create or modify files require a trusted signature
- Plugins and extensions like login items need valid signatures
Gatekeeper has three modes that users can choose from:
- Mac App Store: Most restrictive, allows only apps from the official Mac App Store.
- Mac App Store and identified developers: The default setting allows App Store apps and apps to be signed with a Developer ID.
- Anywhere: Disables Gatekeeper completely and allows launching anything. It is not recommended due to risks.
Users can check and change the Gatekeeper setting by going to System Preferences > Security & Privacy > General.
Developers can ensure their apps work smoothly across all Gatekeeper modes by getting them correctly signed. Apps signed with a Developer ID certificate (or Apple certificate for the App Store) will work in the default mode.
Gatekeeper is an important line of defense against malicious unsigned code. Enforcing code signing improves security for everyday MacOS users.
Benefits and Risks of Disabling Gatekeeper
Some advanced users may want to disable Gatekeeper entirely to install and run unsigned/modified code. Here are some benefits and potential risks of disabling Gatekeeper:
Pros of Disabling Gatekeeper
- Ability to run unsigned apps and binaries downloaded from the internet
- Launch unsigned modified/patched versions of apps
- Install apps blocked by Gatekeeper for being unsigned or “damaged.”
- Run unofficial kernel extensions, drivers, or plugins
- Freedom to run scripts and other code without signatures
Cons of Disabling Gatekeeper
- Increased exposure to malicious apps containing viruses/malware
- Code could be tampered with or modified by others for exploits without your knowledge
- Buggy unsigned app modifications may cause system instability or crashes
- Malfunctioning drivers or kernel extensions could severely impact system security or performance
- Loss of accountability since unsigned code has anonymous authors
Fully disabling Gatekeeper negates many of the protections and trust benefits of code signing and is generally not recommended for most users. However, it allows advanced users more control over running unsigned code if they are willing to accept the risks.
Code Signing for Open-Source Mac Apps
For open-source apps on MacOS, code signing provides a way to retain accountability and integrity benefits while still allowing public contribution and transparency. Some options for handling code signing in open-source Mac projects include:
- Designated trusted project leaders/developers should handle signing using their certificates. They can sign builds before release.
- Using a certificate issued to the common open source project name rather than an individual. E.g. “MyOpenSourceApp”.
- Using reproducible builds so multiple people can verify that signed binaries were built from the same source code.
- Having build systems automatically sign executables using a checked-in certificate.
- We are using tools like notarization to publish evidence for Gatekeeper without private keys.
Final Thoughts
Code signing is a critical aspect of the overall security model for any MacOS apps and software. When implemented properly, it assures users that they are running trusted code that hasn’t been tampered with. Although it adds some overhead for developers, the major benefits around trust, integrity, and malware prevention make it well worth the effort.
Apple provides good support and tooling to streamline code signing, from XCode and command-line tools to a full-fledged certificate management system. Third-party CAs also offer flexible options for various development needs. With some learning and best practices, both independent and enterprise Mac developers can utilize code signing to ship secure software their users can rely on.
Following code signing best practices is strongly recommended for any reputable MacOS software. The wide availability of certificates and signing tools makes the process accessible for developers of all levels. Overall, enforcing valid signatures creates a more robust and safer MacOS ecosystem.
Frequently Asked Questions
Do all apps on the Mac App Store need to be signed?
Yes, all apps submitted to Apple for the Mac App Store must be signed with an Apple-issued certificate as part of the approval process. Apple resigns apps before being distributed via the store.
Can I sign the code without joining the Apple Developer Program?
Yes, you can get code signing certificates from trusted third-party Certificate Authorities like DigiCert, Sectigo, etc., without enrolling as an Apple developer. However, these apps won’t get Gatekeeper approval.
What happens if I try to launch an unsigned app in MacOS?
If Gatekeeper is enabled, it will block the app and show a warning dialog that the app cannot be opened because the developer cannot be verified. You can override this and open the app anyway by right-clicking and selecting Open.
Do self-developed scripts and binaries need to be signed?
If you are launching scripts/binaries yourself on your own Mac, signing is not strictly required. But signing is mandatory if you want to distribute them to other users or use features like sudo access.
Can I sign up for an app that I downloaded from outside the Mac App Store?
No, you can only sign your original apps/code. Trying to re-sign a downloaded app will invalidate the original developer’s signature.
What are the major differences between Developer ID vs Mac App Store signing?
Developer ID allows distribution outside the Mac App Store but doesn’t guarantee Gatekeeper will approve your app. Mac App Store signing requires Apple’s approval process but enables smooth Gatekeeper compatibility.
What happens if my code signing certificate expires?
Once it expires, you will no longer be able to sign a new code using that certificate. Existing apps signed with the certificate will stop launching with Gatekeeper enabled and must be resigned.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.