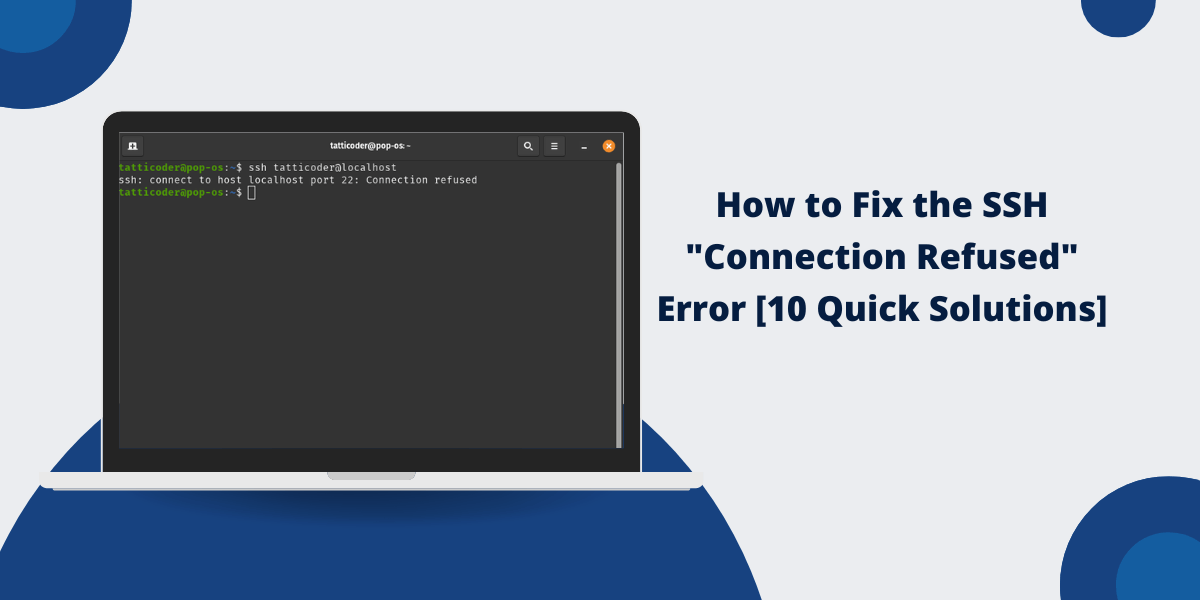
Why does SSH show ‘Connection Refused’?
The SSH ‘Connection Refused’ error occurs when the remote server rejects connections, usually because the SSH service isn’t running (sudo systemctl start sshd), port 22 is blocked (sudo ufw allow 22), or network/firewall rules prevent access. Verify the service status, check local and cloud firewall settings, test port connectivity with telnet, and review Fail2Ban restrictions. Misconfigured IP addresses or sshd_config files can also cause this. Most cases resolve by ensuring SSH is active and the correct port is accessible.
This comprehensive guide investigates every possible reason behind this error while providing complete step-by-step solutions to restore SSH connection functionality. The following troubleshooting procedures will assist system administrators’ developers and IT professionals to diagnose and resolve their SSH connection problems efficiently.
What Causes the SSH ‘Connection Refused’ Error?
You need to understand the root causes of this error before starting the solution process. The SSH (Secure Shell) protocol operates through multiple essential components which must function correctly:
- The SSH daemon (sshd) must be running on the server
- Network connectivity must be available between client and server
- Firewall rules must permit SSH traffic (typically on port 22)
- Authentication configurations must be properly set up
The “Connection Refused” error occurs when any of the essential components fail to operate correctly or when their configurations become misaligned. The following section analyzes each possible reason together with its corresponding solution.
10 Quick Solutions to Fix the SSH “Connection Refused” Error
- Verify SSH Service Status on the Server
- Confirm SSH Server Configuration
- Verify Network Connectivity
- Firewall Configuration Checks
- Checking for IP Bans (Fail2Ban)
- SELinux Considerations
- Verifying Host Keys and Known_hosts
- Checking Resource Limitations
- Alternative Connection Methods
- Complete Reinstallation
1. Verify SSH Service Status on the Server
The most fundamental check is whether the SSH daemon is actually running on your server.
Checking SSH Service Status
On Linux systems using systemd (most modern distributions), run:
sudo systemctl status ssh
Or for older systems using init.d:
sudo service ssh status
Interpreting the Output
You should see one of three states:
- Active (running): SSH is working correctly
- Inactive (dead): SSH is not running
- Failed: SSH crashed or encountered an error
Starting the SSH Service
If the service isn’t running:
sudo systemctl start ssh # Start immediately
sudo systemctl enable ssh # Enable at boot
For older systems:
sudo service ssh start
update-rc.d ssh enable # On Debian/Ubuntu
chkconfig ssh on # On CentOS/RHEL
Troubleshooting Service Start Failures
If the service fails to start, check the logs:
journalctl -u ssh.service -b # Systemd systems
tail -n 50 /var/log/auth.log # Debian/Ubuntu
tail -n 50 /var/log/secure # CentOS/RHEL
Common startup issues include:
- Invalid configuration in /etc/ssh/sshd_config
- Port conflicts (another service using port 22)
- Permission problems with host keys
2. Confirm SSH Server Configuration
The SSH server’s configuration file determines how it operates. Let’s examine key settings.
Checking the SSH Configuration File
Open the configuration file:
sudo nano /etc/ssh/sshd_config
Key directives to verify:
- Port: Should match what you’re connecting to (default 22)
- ListenAddress: Should include your server’s IP
- PermitRootLogin: If disabled, you can’t SSH as root
- PasswordAuthentication: If disabled, you need SSH keys
Common Configuration Issues
- Custom SSH Port: If you changed from default port 22, ensure:
- Your client connects to the correct port (ssh -p 2222 user@host)
- The firewall allows the custom port
- Custom SSH Port: If you changed from default port 22, ensure:
AllowUsers username
DenyUsers restricted_user
Ensure your username is allowed
- IPv6 Issues: If ListenAddress only specifies IPv4, IPv6 connections may fail
sudo systemctl restart ssh
3. Verify Network Connectivity
Before assuming SSH is the problem, confirm basic network connectivity.
Basic Network Tests
- Ping the Server:
ping server_ip
If this fails, you have a network-level problem
- Check if Port is Open:
telnet server_ip 22 nc -zv server_ip 22
Should show “Connected” or “succeeded”
- Test from Different Networks:
- Try from a different computer
- Try using mobile hotspot
- Test from within the same network (if possible)
Advanced Network Diagnostics
For deeper analysis:
traceroute server_ip # Shows network path
mtr server_ip # Combines ping+traceroute
ss -tulnp | grep ssh # Shows if SSH is listening
4. Firewall Configuration Checks
Firewalls at multiple levels might block SSH:
Local Firewall (UFW/iptables)
UFW (Ubuntu):
sudo ufw status sudo ufw allow 22/tcp sudo ufw enable
iptables:
sudo iptables -L -n -v # View rules sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT sudo service iptables save
Cloud Provider Firewalls
For AWS, GCP, Azure, etc.:
- Check Security Groups (AWS)
- Verify Firewall Rules (GCP)
- Examine Network Security Groups (Azure)
ISP or Corporate Firewalls
Some ISPs block port 22. Solutions:
- Use a different port (e.g., 2222)
- Set up a VPN first
- Use SSH over HTTPS (advanced)
sudo certbot certonly --standalone -d yourdomain.com
5. Checking for IP Bans (Fail2Ban)
Repeated failed attempts may trigger automatic bans:
Check active bans:
sudo fail2ban-client status sshd
Unban an IP:
sudo fail2ban-client set sshd unbanip your_ip
Temporarily disable Fail2Ban (for testing):
sudo systemctl stop fail2ban
6. SELinux Considerations
On RHEL/CentOS systems, SELinux might interfere:
Check SELinux status:
sestatus
Temporarily set to permissive (for testing):
sudo setenforce 0
sudo semanage port -a -t ssh_port_t -p tcp 2222 # If using custom port
7. Verifying Host Keys and Known_hosts
Client-side issues can sometimes manifest as connection problems:
Remove old host key (if server keys changed):
ssh-keygen -R server_ip
Debug connection attempts:
ssh -vvv user@server_ip
8. Checking Resource Limitations
Server resource exhaustion can prevent new connections:
Check system resources:
top
df -h
free -h
Review SSH max connections:
grep MaxStartups /etc/ssh/sshd_config
9. Alternative Connection Methods
When all else fails, try:
- Console access (AWS EC2, DigitalOcean, etc.)
- Out-of-band management (IPMI, iDRAC)
- Serial console (for physical servers)
10. Complete Reinstallation
As a last resort:
sudo apt purge openssh-server && sudo apt install openssh-server # Debian/Ubuntu
What Are the Best Practices to Avoid SSH Connection Issues?
Once resolved, implement these best practices:
- Configure SSH securely:
- Disable root login
- Use key-based authentication
- Change default port
- Set up monitoring:
sudo apt install monit
- Implement backups::
- Backup /etc/ssh/sshd_config
- Document all changes
Final Thoughts
The SSH “Connection Refused” error requires methodical troubleshooting across multiple potential failure points to resolve. The following guide provides a complete process starting with basic checks through advanced diagnostics to help you identify and solve your connection problems.
SSH problems originate from various points including the SSH service and system configurations as well as network settings and external firewalls. Begin with basic checks before advancing to complex solutions.
The verbose SSH output (ssh -vvv) provides essential information about connection process failures when dealing with persistent issues. System logs from /var/log/auth.log or /var/log/secure provide complete authentication process visibility when used with the verbose SSH output.
Frequently Asked Questions (FAQs)
Why does SSH say connection refused?
SSH shows “connection refused” when the SSH service is not running on the target server. This error also occurs if the firewall blocks port 22 or if SSH configurations contain incorrect settings.
How do I enable SSH connection?
Enable SSH by installing OpenSSH server using ‘sudo apt-get install openssh-server’ on Ubuntu/Debian systems. Start the SSH service with ‘sudo systemctl start sshd’. Check if port 22 is open in your firewall settings.
What port is SSH connection refused?
SSH uses port 22 by default. The connection refused error appears when this port is blocked or closed. Users can verify port status using the command ‘netstat -tuln | grep 22’.
How do I fix SSH permission denied?
Fix SSH permission denied by setting correct file permissions (chmod 600) for SSH keys. Check user authentication settings in the /etc/ssh/sshd_config file. Ensure the user has proper access rights to the target system.
How do I know if SSH is running?
Check SSH status with ‘sudo systemctl status sshd’ command on Linux systems. Use ‘ps aux | grep ssh’ to see running SSH processes. The command ‘netstat -tuln’ shows if port 22 is listening.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.