How to Ignore HSTS on Firefox?
To ignore HSTS (HTTP Strict Transport Security) in Firefox, you can bypass it through Firefox’s advanced settings. Open Firefox and type ‘about:config’ in the address bar. Click “Accept the Risk” when prompted. Search for ‘security.ssl.enable_ocsp_stapling’ and set it to false. Next, search for ‘security.cert_pinning.enforcement_level’ and change the value to ‘0’. This disables HSTS checks. Note that disabling HSTS reduces security and should only be done for testing purposes. After testing, restore these settings to their default values to maintain browser security.
How to Bypass HSTS in Firefox
Firefox provides a handy toggle in advanced settings to disable HSTS and allow unsafe HTTP access to HSTS sites when necessary:
- Enter about:config in the Address Bar
- Search for security.cert_pinning.enforcement_level
- Set the Value to off
- Restart the Browser
- Revert Setting When Done
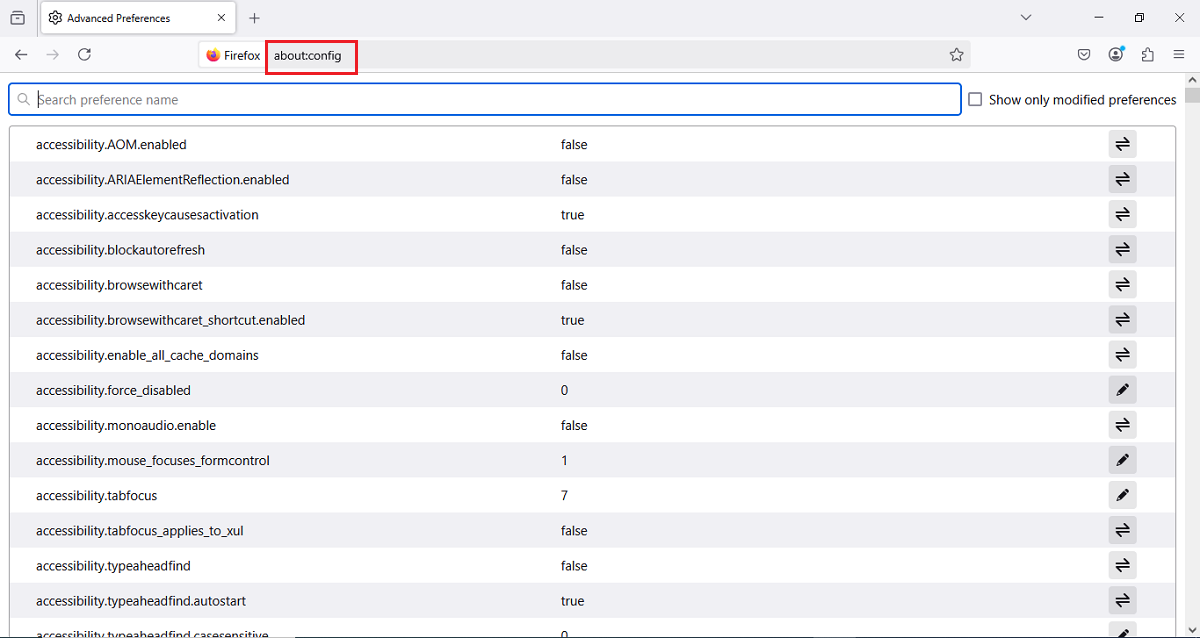
Step 1: Enter about:config in the Address Bar
The about:config page shows Firefox’s list of customizable advanced settings.
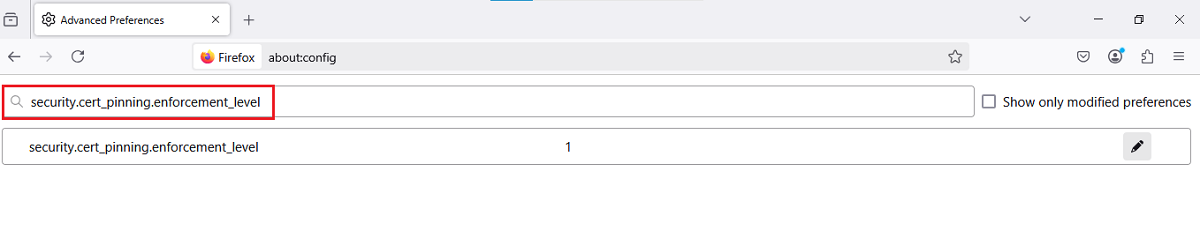
Step 2: Search for security.cert_pinning.enforcement_level
This preference controls Firefox’s HSTS behavior. The default value is strict, which enforces pinned HTTPS connections.
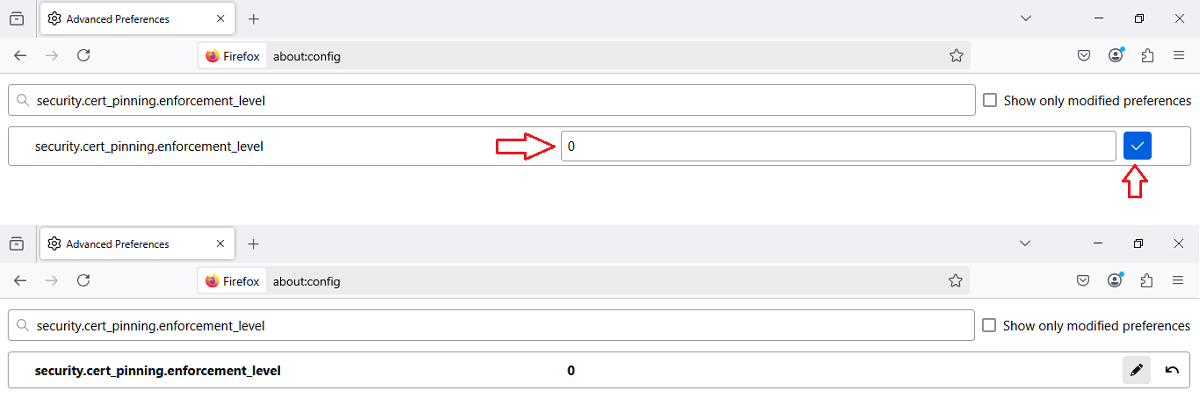
Step 3: Set the Value to 0
Double-click the preference and set the value to 0. This completely disables HSTS and allows HTTP access to HSTS-enabled sites.
Step 4: Restart the Browser
For the change to take full effect, you need to restart Firefox.
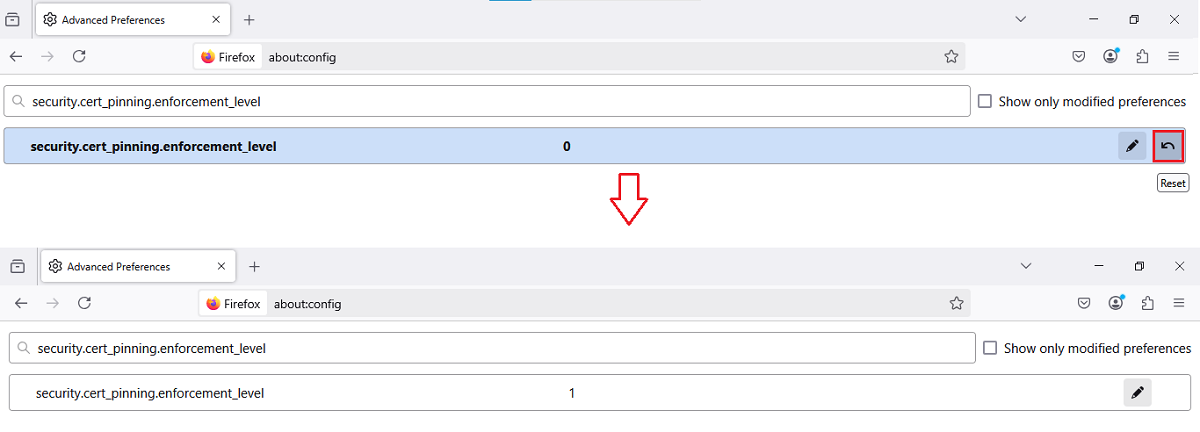
Step 5: Revert Setting When Done
When you are finished with testing, revert the security.cert_pinning.enforcement_level setting back to strict with value 1 (default) and restart Firefox again to re-enable HSTS protections.
When You Might Need to Bypass HSTS
There are some legitimate reasons why you may want to access a site over HTTP, even if it has HSTS enabled:
- Checking for mixed content errors before migrating a site to HTTPS-only.
- Using development/testing tools that don’t support HTTPS connections.
- Temporarily roll back HTTPS to debug connection issues.
Of course, you should only temporarily bypass HSTS for testing purposes. For better security, normal browsing should always be done with HSTS enabled.
Other Ways to Temporarily Bypass HSTS
Some other options for bypassing HSTS in Firefox include:
- Using the security.cert_pinning.process_headers_from setting to disable HSTS for specific sites.
- Firefox is starting in Safe Mode, which launches with HSTS disabled by default.
- Using the Firefox DevTools to disable HSTS on a particular domain.
- Installing a plugin like Disable HTTP Strict Transport Security (HSTS)
However, simply toggling the global enforcement level is usually the easiest way to disable HSTS when needed for temporary testing.
Final Thoughts
While HSTS improves security, bypassing it in Firefox provides flexibility in certain development or debugging situations. Just make sure to re-enable it after testing for maximum security when browsing production sites.

Priya Mervana
 Verified Web Security Experts
Verified Web Security Experts
Priya Mervana is working at SSLInsights.com as a web security expert with over 10 years of experience writing about encryption, SSL certificates, and online privacy. She aims to make complex security topics easily understandable for everyday internet users.



