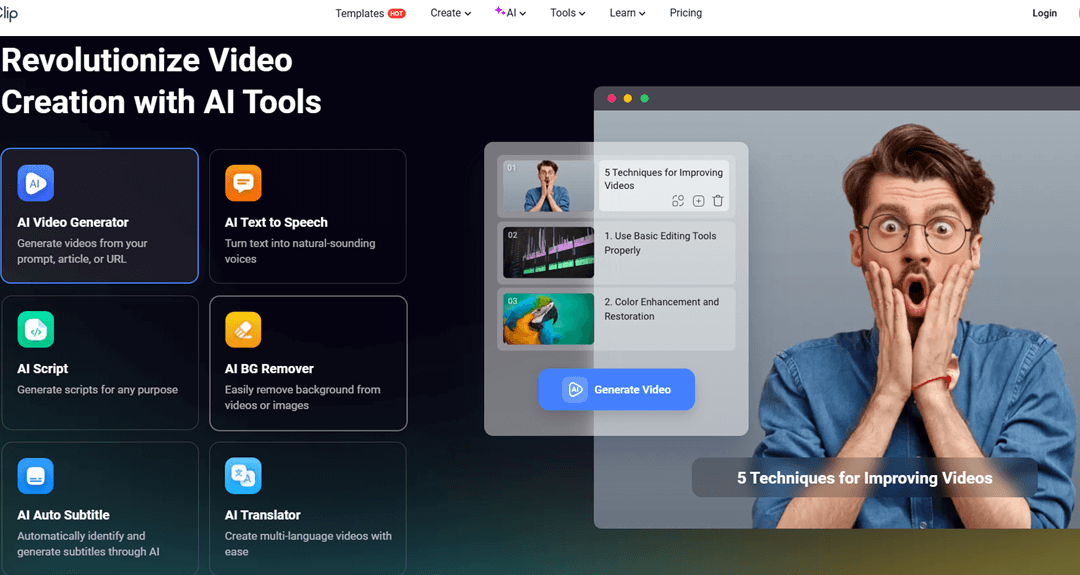
Your online shop thrives when you truly understand your buyers. Online shopping is everywhere now, and businesses must grasp what makes customers click 'buy.' It is where an SEO team steps in. When businesses really watch what customers do, they can create winning...