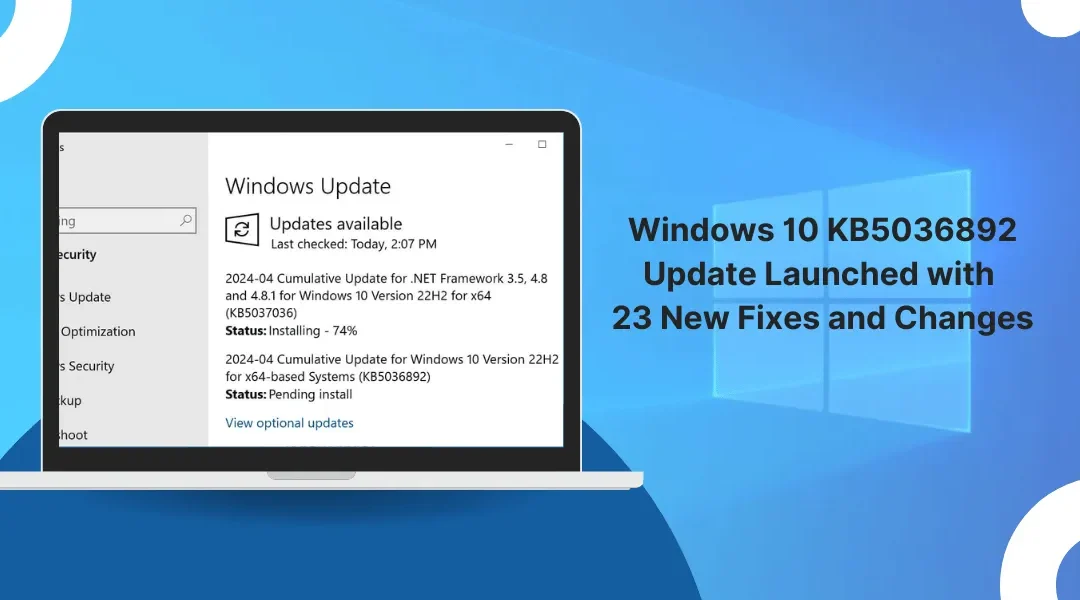
Windows 10 KB5036892 Update with 23 New Fixes and Changes Microsoft recently released the Windows 10 KB5036892 cumulative update for April 2024 as part of the company's monthly Patch Tuesday security updates. This mandatory update contains bug fixes, new features, and...